SunShineCTF2022

This year sunshineCTF was amazing. The CTF was challenging. We had no internet, The wifi they provided was constently disconnecting everyone. Most of the challenges was about pwn and RE, which Im not so good at. So I decided to focus on Web Challenges. Here are some of the challenges I solved.
Challenge → Transparency
Point → 50
Description → This one is simple! Just look where you
might look at the cryptographic history of the sunshinectf.org domain! There’s a Yeti in one and a Nimbus in another!
Flag Format: sun*endflag
example: sun-this-is-the-flag-endflag
Solution → After researching for sometime, I found this website where you can see history of SSL/TLS Certificates.
https://ui.ctsearch.entrust.com/ui/ctsearchui
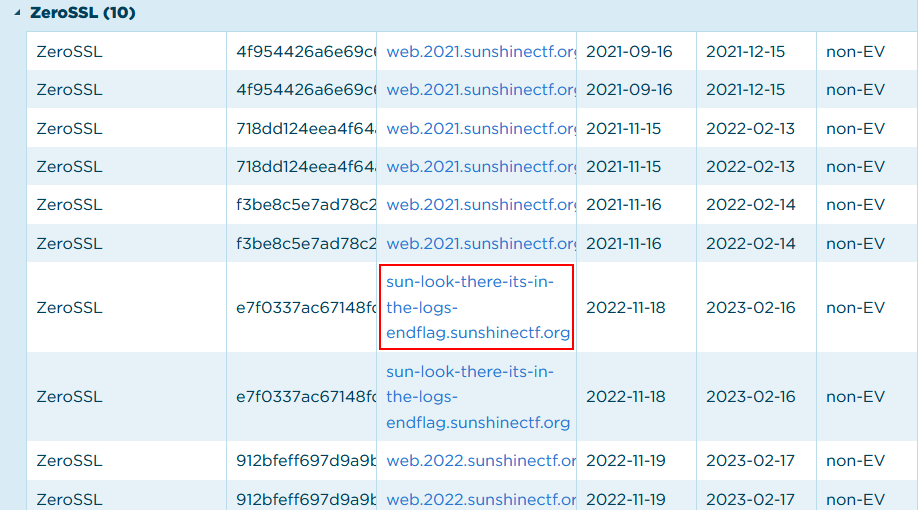
Flag → sun-look-there-its-in-the-logs-endflag
Challenge → Inspect Element
Point → 50
Description → DONT inspect-element. Our education game servers are now secure.They used to have flags on them, but we’ve made the website 100% secure now.All malicious hackers are now instructed, do not use inspect element on this page. Problemo solved!
Automation → Inspect Element
Solution → There is a lot going on the website. I decided to check the source code.
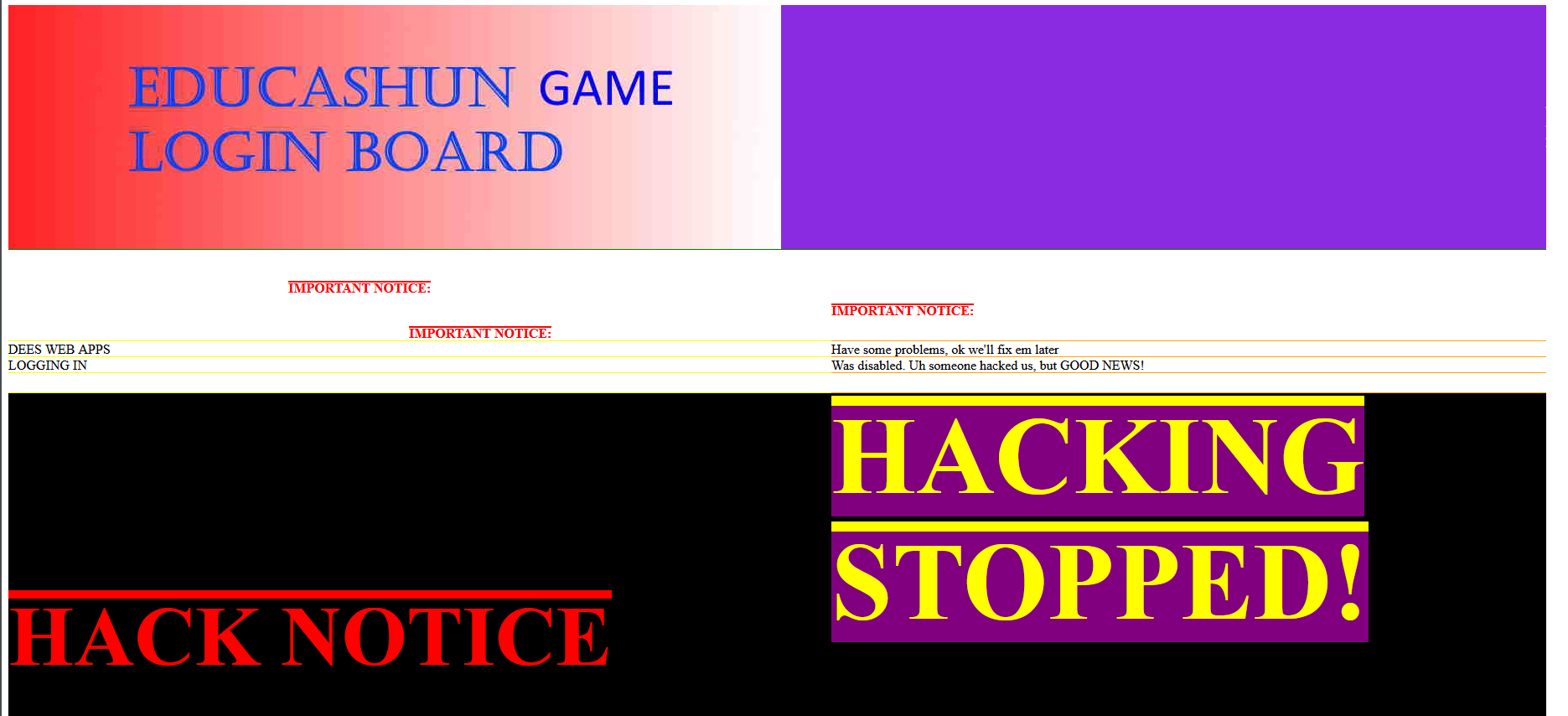
After looking at the source code I found the flag.
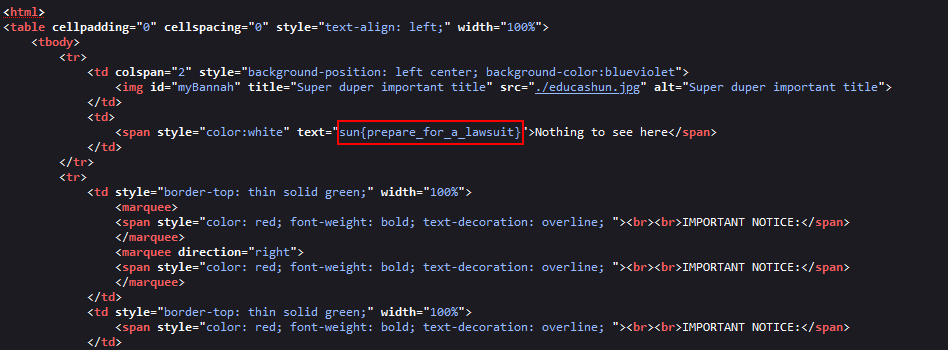
Flag → sun{prepare_for_a_lawsuit}
Challenge → Network Pong
Point → 100
Description →Introducing Network Pong : Pong for the Internet! In this game, you just ping random websites and try to get the lowest latency. It is protected with state-of-the-art
anti-hacking techniques, so it should be unhackable according to our security team of well-trained monkeys and felines.
Automation → Network Pong
Solution → Upon visiting the website, I found a perameter which takes IP. So I tried a random IP to check it out.
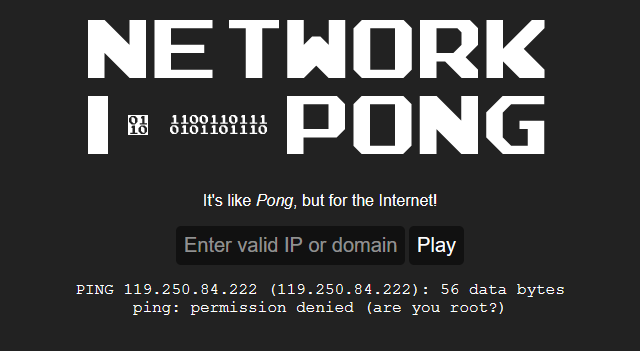
From the result It looks like its dealing with the system. I decided use the following OS command payload to get the flag.
0.0.0.0$(less${IFS}flag.txt)
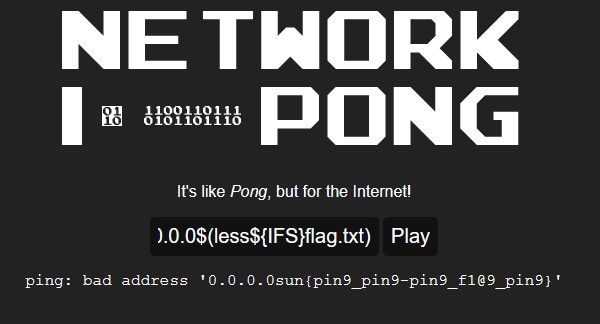
Flag → sun{pin9_pin9-pin9_f1@9_pin9}










